BCACTF 2019 Write-up
はじめに
2019/06/09 ~ 2019/06/16に開催されたBCACTFに個人で参加しました.
成績
115位(902チーム中)でした.
Welcome
hello-world [50pts, 858solves]
Input your first ever flag! The flag is bcactf{hello!}
アプローチ:問題文を読む
bcactf{hello!}
net-cat [50pts, 700solves]
Some problems in this CTF will require you to use netcat to access server-side problems.
For this problem netcat in to our server by using
nc challenges.ctfd.io 30126
アプローチ:問題文を読む
> nc challenges.ctfd.io 30126
bcactf{5urf1n_7h3_n37c47_c2VydmVyc2lkZQ}
bcactf{5urf1n_7h3_n37c47_c2VydmVyc2lkZQ}
wuphf [50pts, 563solves]
Social media is so fractured today. I mean, there's Discord, Twitter, Instagram... Don't you wish there was just one platform that could send things to every platform? Sadly that's not the case, so to find the flag you will have to collect flag-ments from all of our platforms.
アプローチ:問題文を読む
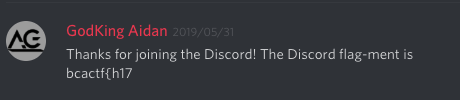
Thanks for checking out our twitter! Why don't you drop us a follow?
— BCACTF (@bca_ctf) 2019年5月30日
Flag-ment: _u5_uP_d3
Discord: bcactf{h17
Twitter: _u5_uP_d3
Instagram: VwaGYuY29t}
bcactf{h17_u5_uP_d3VwaGYuY29t}
Binary-exploitation
executable [150pts, 217solves]
It's in there somewhere. Good luck!
> file executable-ubuntu executable-ubuntu: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=2d69b145cafba5b1850ed1677373b4058b19a78e, not stripped
アプローチ:strings
stringsするとBrainf*ckっぽいのが出てきます.
> strings executable-ubuntu [snip] Welcome to the lottery! So now we're going to pick a ginormous number! If it's 1, you win! Your number is %d! Congratulations, you're our lucky winner! Try again next time! --[----->+<]>----.+.--.++.-[--->+<]>--.+++[->+++<]>+.+[----->+<]>.>-[----->+<]>.+[--->++<]>.[++>---<]>-.-[->++<]>-.-[--->+<]>-.-.>-[----->+<]>+.---[->++<]>.++++++++++.[-->+<]>---.--[--->++<]>---.++[->+++<]>.[--->+<]>---.+++[->+++<]>.+++++++.-[--->+<]>--.-------.---------------.+[-->+<]>+.+.++.+[->++<]>.--.---.+++++++++++++.--[->+++++<]>.++++++++.+.-------.++.+.>--[-->+++<]>. ;*3$" GCC: (Ubuntu 5.4.0-6ubuntu1~16.04.11) 5.4.0 20160609 [snip]
適当なインタプリタで実行すればflagが出てきます.
bcactf{3x3cut4bl3s_r_fun_124jher089245}
これのどこにPwn要素があるんだろう?
Crypto
basic-numbers [50pts, 698solves]
We have a raw flag here, but what do we do with it?
01100010 00110001 01101110 01100001 01110010 01111001 01011111 01110011 00110000 01101100 01110110 00110011 01100100 01011111 01100111 00110000 00110000 01100100 01011111 01110111 00110000 01110010 01101011
アプローチ:bin to ascii
bins = '01100010 00110001 01101110 01100001 01110010 01111001 01011111 01110011 00110000 01101100 01110110 00110011 01100100 01011111 01100111 00110000 00110000 01100100 01011111 01110111 00110000 01110010 01101011' flag = '' for b in bins.split(' '): flag += chr(int(b, 2)) print('bcactf{{{0}}}'.format(flag))
bcactf{b1nary_s0lv3d_g00d_w0rk}
cracking-the-cipher [50pts, 627solves]
Hackers work in the most unlikely of places. We have recently discovered one working in a grocery store (weird), and he was able to print out receipts to pass on information to certain customers. We have obtained one of the receipts, but we cannot tell what it says.
vjg rcuuyqtf ku ngctpkpi_ecguct_ekrjgtu_ku_hwp!
アプローチ:rot24
the password is learning_caesar_ciphers_is_fun!
bcactf{learning_caesar_ciphers_is_fun!}
three-step-program [125pts, 300solves]
We found this strange file with a bunch of stuff in it... Can you help us decode it?
MzIgLSAgfDMgVGltZXMgQSBDaGFybXwgLSAzMg==
JJGTEVSLKNBVISSGINCU2VCTGJFVETCWKNGVGTKLKJEEKQ2VJNEUSNC2KZKVCS2OJFNE4RKPKNFUUSKSJNKTITSDKJFEERKUI5GTETKJLJGVMQ2RJNLEWUSLIZAVES2DJRFE2RKDK5JU2SKKJBCTEVKLJBDUSWSUI5KTETSLKZEVKS2TLJKEWUSFIU2FKU2WJRBEIVCFKFJVASKWIFKU2USLIRDUUR2FGJJEWQ2LKJGFMR2TJNCUYSSIIRFU2U2UJFCTEVKJKZJUMSKKJNKU6VK2KRFVES2VGZKEWUSKIJCVIR2XKNBEUNKGIZDVMMSEJRFEERKDKRJVOR2SJJKUGV2TJVFDKR2VGRLVGSKLJUZEKSKWJNHEWWSKKVDVCSSUJFJEERJUK5JVKTCCIZKEKVCDIVFFUQKWKFITEQSJJZEVKV2SGJDEYQSCKVBVMSSTJFFEMRSFKMZEISKFLJCVSTKTIZEUUTCGJ5JVUV2KJJAVKNSVKNMUWTSBKZKU2MSUJJLEYRCFKEZEETCKJNDECVCSKZFU4QSVI5ITEU2LJZCEMU2VJNDEYRSOIVKVCS2OJRFE4RKPKFNFIS2SINCTEUSTKZGEERCVKNJEGRKKGVDEISKXINBEOVSDIVGVES2DJM2UIVKXKNFUKSS2I5LE2VSLLBGEKWSVJFJFGUCLLJHEKQ2QJI2UQVJWKE6T2PJ5
lhlm oad lamaew eyhmgs. lg i sxsro rgu ntee qhj a qesg? dbfcp rgu stne xtve tm lhtl xac, b’dl rh wadr gn jhm ayw zayw at zowr.
mvscey{bu57_j0n_o4i7_kgbhmffhlqe} bfm, te htjnpw, feim lixx at hhf’t mx ko dbepwx…
アプローチ:Vigenere cipher
first-stepのbase64をデコードします.
> echo 'MzIgLSAgfDMgVGltZXMgQSBDaGFybXwgLSAzMg==' | base64 -D 32 - |3 Times A Charm| - 32
???
何も分からないのでthird-stepの暗号化方式をエスパーしてVigenere Solverで無理やり解きます.
that was simple enough. so i heard you came for a flag? since you have made it this far, i’ll go easy on you and hand it over.
bcactf{ju57_y0u_w4i7_znjhbmnhaxm} but, be warned, next time it won’t be so simple…
bcactf{ju57_y0u_w4i7_znjhbmnhaxm}
keyはsaltらしいです.
a-major-problem [200pts, 313solves]
A mysterious figure named Major Mnemonic has sent you the following set of words. Figure out what they mean!
"Pave Pop Poke Pop Dutch Dozen Denim Deism Loot Thatch Pal Atheism Rough Ditch Tonal"
アプローチ:Mnemonic major system
オンラインツールを使ってデコードするとメッセージは98, 99, 97, 99, 116, 102, 123, 103, 51, 116, 95, 103, 47, 116, 125に対応していることがわかります.
asciiに変換すると以下のようになります.
num_words = [98, 99, 97, 99, 116, 102, 123, 103, 51, 116, 95, 103, 47, 116, 125] flag = [chr(x) for x in num_words] print(''.join(flag))
bcactf{g3t_g/t}
これで終わりかと思いきやこのflagをsubmitしてもincorrectと言われます.
色々と試してみても上手く行かなかったので最終的にエスパーで通しました (/に違和感があったので0に置き換えてsubmitするとcorrectになりました).
bcactf{g3t_g0t}
Forensics
split-the-red-sea [100pts, 551solves]
Moses used a staff to split the Red Sea. What will you use?

アプローチ:Exif
> exiftool redsea.png | grep bcactf
Text Layer Name : bcactf{7w0_r3d5_sdf3wqa}
Text Layer Text : bcactf{7w0_r3d5_sdf3wqa}
bcactf{7w0_r3d5_sdf3wqa}
bca-craft [125pts, 460solves]
Yo I made a sic Minecraft adventure MAP! Try it out it's kewler than ur Fortnite gamez!
アプローチ:grep
> grep -r 'flag' ./BCACraft
./BCACraft/datapacks/bcacraft/data/bca/functions/flag.mcfunction:tellraw @a ["Hello ", {"selector": "@p", "color": "yellow"}, "! The flag is: ", "b", "c", "a", "c", "t", "f", "{", {"text": "m1n3cr4f7_b347s_f0rtn1t3", "color": "blue", "bold": true, "obfuscated": true, "hoverEvent": {"action": "show_text", "value": {"text": "Good luck! ", "extra": [{"text": "Hint: Where does Minecraft store its worlds?", "color": "dark_gray", "italic": true}]}}}, "}"]
bcactf{m1n3cr4f7_b347s_f0rtn1t3}
file-head [125pts, 457solves]
It looks like the PNG file that holds our flag has been corrupted. My computer isn't able to recognize the file type, maybe it has something to do with how the file type is recognized...
> file flag.png flag.png: 5View capture file
アプローチ:マジックナンバー
バイナリエディタでflag.pngを開くとヘッダが0xAAで潰されていることが分かります.
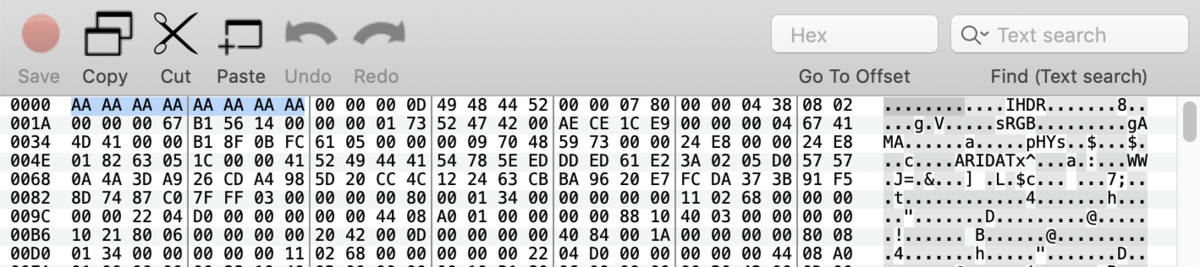
89 50 4E 47 0D 0A 1A 0Aに修正します.
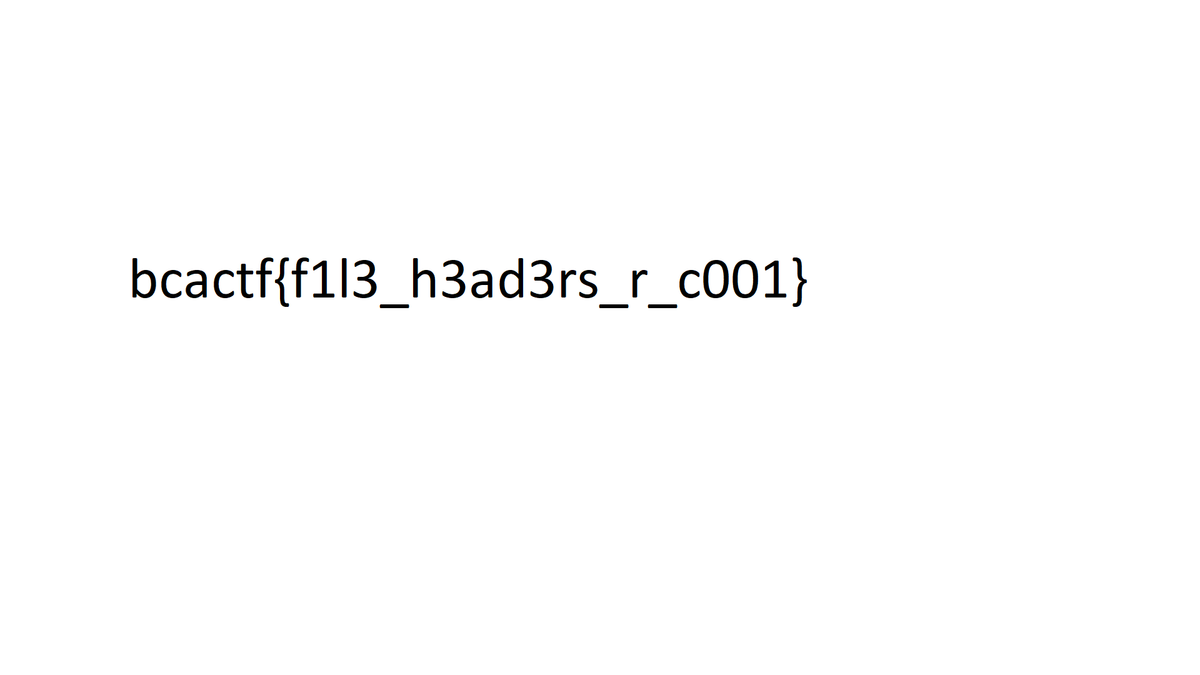
bcactf{f1l3_h3ad3rs_r_c001}
of-course-rachel [150pts, 219solves]
Ugh, I had a really important file with the flag, but sadly it broke. My friend Rachel said that snapshots are good for backing up, and luckily I listened so here is my screenshot. Do you think you could help me put it back together?
> tree snapshot snapshot ├── part1.png ├── part2.png ├── part3.png ├── part4.png └── part5.png 0 directories, 5 files
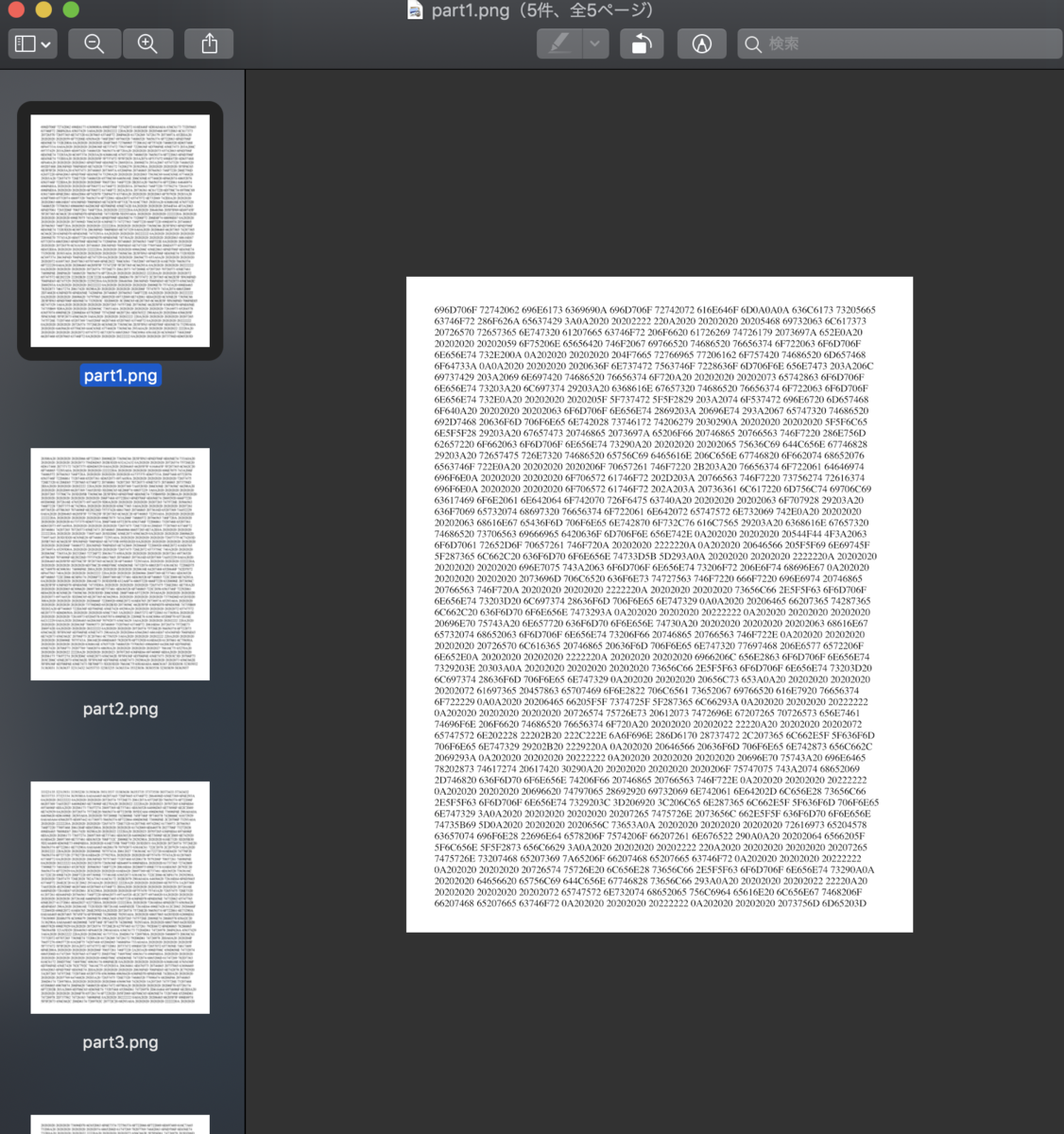
part*.pngにはそれぞれhex dataっぽいものが描画されているのでOCRを使ってテキストデータに変換します.
テキストデータを1つのファイルにまとめます
from Crypto.Util.number import long_to_bytes with open('./snapshot/memo.txt') as f: hex_lines = [line.strip() for line in f.readlines()] flag = b'' for line in hex_lines: for msg in line.split(' '): flag += long_to_bytes(int(msg,16)) with open('flag.py', 'wb') as f: f.write(flag)
import binascii import random class Vector(object): """ This class represents a vector of arbitray size. You need to give the vector components. Overview about the methods: constructor(components : list) : init the vector set(components : list) : changes the vector components. __str__() : toString method component(i : int): gets the i-th component (start by 0) __len__() : gets the size of the vector (number of components) euclidLength() : returns the eulidean length of the vector. operator + : vector addition operator - : vector subtraction operator * : scalar multiplication and dot product copy() : copies this vector and returns it. changeComponent(pos,value) : changes the specified component. TODO: compare-operator """ def __init__(self, components=[]): """ input: components or nothing simple constructor for init the vector """ self.__components = list(components) def set(self, components): """ input: new components changes the components of the vector. replace the components with newer one. """ if len(components) > 0: self.__components = list(components) else: raise Exception("please give any vector") def __str__(self): """ returns a string representation of the vector """ return "(" + ",".join(map(str, self.__components)) + ")" def component(self, i): """ input: index (start at 0) output: the i-th component of the vector. """ if type(i) is int and -len(self.__components) <= i < len(self.__components): return self.__components[i] else: raise Exception("index out of range") def __len__(self): """ returns the size of the vector """ return len(self.__components) def eulidLength(self): """ returns the eulidean length of the vector """ summe = 0 for c in self.__components: summe += c**2 return math.sqrt(summe) def __add__(self, other): """ input: other vector assumes: other vector has the same size returns a new vector that represents the sum. """ size = len(self) if size == len(other): result = [self.__components[i] + other.component(i) for i in range(size)] return Vector(result) else: raise Exception("must have the same size") def __sub__(self, other): """ input: other vector assumes: other vector has the same size returns a new vector that represents the differenz. """ size = len(self) if size == len(other): result = [self.__components[i] - other.component(i) for i in range(size)] return result else: # error case raise Exception("must have the same size") def __mul__(self, other): """ mul implements the scalar multiplication and the dot-product """ if isinstance(other, float) or isinstance(other, int): ans = [c*other for c in self.__components] return ans elif (isinstance(other, Vector) and (len(self) == len(other))): size = len(self) summe = 0 for i in range(size): summe += self.__components[i] * other.component(i) return summe else: # error case raise Exception("invalide operand!") def copy(self): """ copies this vector and returns it. """ return Vector(self.__components) def changeComponent(self, pos, value): """ input: an index (pos) and a value changes the specified component (pos) with the 'value' """ # precondition assert (-len(self.__components) <= pos < len(self.__components)) self.__components[pos] = value flag = 820921601166721424573282546345206805820898697321521913920196691573868657577500743744203737234698 def zeroVector(dimension): """ returns a zero-vector of size 'dimension' """ # precondition assert(isinstance(dimension, int)) return Vector([0]*dimension) def main(): print(int_to_text(flag)) def unitBasisVector(dimension, pos): """ returns a unit basis vector with a One at index 'pos' (indexing at 0) """ # precondition assert(isinstance(dimension, int) and (isinstance(pos, int))) ans = [0]*dimension ans[pos] = 1 return Vector(ans) def axpy(scalar, x, y): """ input: a 'scalar' and two vectors 'x' and 'y' output: a vector computes the axpy operation """ # precondition assert(isinstance(x, Vector) and (isinstance(y, Vector)) and (isinstance(scalar, int) or isinstance(scalar, float))) return (x*scalar + y) def randomVector(N, a, b): """ input: size (N) of the vector. random range (a,b) output: returns a random vector of size N, with random integer components between 'a' and 'b'. """ random.seed(None) ans = [random.randint(a, b) for i in range(N)] return Vector(ans) def text_to_int(inp): hexed = binascii.hexlify(inp) return int(hexed, 16) def int_to_text(inp): hexed = hex(inp) return bytearray.fromhex(hexed[2:]).decode() class Matrix(object): """ class: Matrix This class represents a arbitrary matrix. Overview about the methods: __str__() : returns a string representation operator * : implements the matrix vector multiplication implements the matrix-scalar multiplication. changeComponent(x,y,value) : changes the specified component. component(x,y) : returns the specified component. width() : returns the width of the matrix height() : returns the height of the matrix operator + : implements the matrix-addition. operator - _ implements the matrix-subtraction """ def __init__(self, matrix, w, h): """ simple constructor for initialzes the matrix with components. """ self.__matrix = matrix self.__width = w self.__height = h def __str__(self): """ returns a string representation of this matrix. """ ans = "" for i in range(self.__height): ans += "|" for j in range(self.__width): if j < self.__width - 1: ans += str(self.__matrix[i][j]) + "," else: ans += str(self.__matrix[i][j]) + "|\n" return ans def changeComponent(self, x, y, value): """ changes the x-y component of this matrix """ if x >= 0 and x < self.__height and y >= 0 and y < self.__width: self.__matrix[x][y] = value else: raise Exception("changeComponent: indices out of bounds") def component(self, x, y): """ returns the specified (x,y) component """ if x >= 0 and x < self.__height and y >= 0 and y < self.__width: return self.__matrix[x][y] else: raise Exception("changeComponent: indices out of bounds") def width(self): """ getter for the width """ return self.__width def height(self): """ getter for the height """ return self.__height def __mul__(self, other): """ implements the matrix-vector multiplication. implements the matrix-scalar multiplication """ if isinstance(other, Vector): # vector-matrix if (len(other) == self.__width): ans = zeroVector(self.__height) for i in range(self.__height): summe = 0 for j in range(self.__width): summe += other.component(j) * self.__matrix[i][j] ans.changeComponent(i, summe) summe = 0 return ans else: raise Exception( "vector must have the same size as the " + "number of columns of the matrix!") elif isinstance(other, int) or isinstance(other, float): # matrix-scalar matrix = [[self.__matrix[i][j] * other for j in range(self.__width)] for i in range(self.__height)] return Matrix(matrix, self.__width, self.__height) def __add__(self, other): """ implements the matrix-addition. """ if (self.__width == other.width() and self.__height == other.height()): matrix = [] for i in range(self.__height): row = [] for j in range(self.__width): row.append(self.__matrix[i][j] + other.component(i, j)) matrix.append(row) return Matrix(matrix, self.__width, self.__height) else: raise Exception("matrix must have the same dimension!") def __sub__(self, other): """ implements the matrix-subtraction. """ if (self.__width == other.width() and self.__height == other.height()): matrix = [] for i in range(self.__height): row = [] for j in range(self.__width): row.append(self.__matrix[i][j] - other.component(i, j)) matrix.append(row) return Matrix(matrix, self.__width, self.__height) else: raise Exception("matrix must have the same dimension!") def squareZeroMatrix(N): """ returns a square zero-matrix of dimension NxN """ ans = [[0]*N for i in range(N)] return Matrix(ans, N, N) def randomMatrix(W, H, a, b): """ returns a random matrix WxH with integer components between 'a' and 'b' """ random.seed(None) matrix = [[random.randint(a, b) for j in range(W)] for i in range(H)] return Matrix(matrix, W, H) main()
> python flag.py
bcactf{0p71c4lly_r3c0gn1z3d_ch4r4c73rs}
open-docs [150pts, 420solves]
Yay! I really enjoy using these free and open file standards. I love them so much, that I made a file expressing how much I like using them. Let's enjoy open standards together!
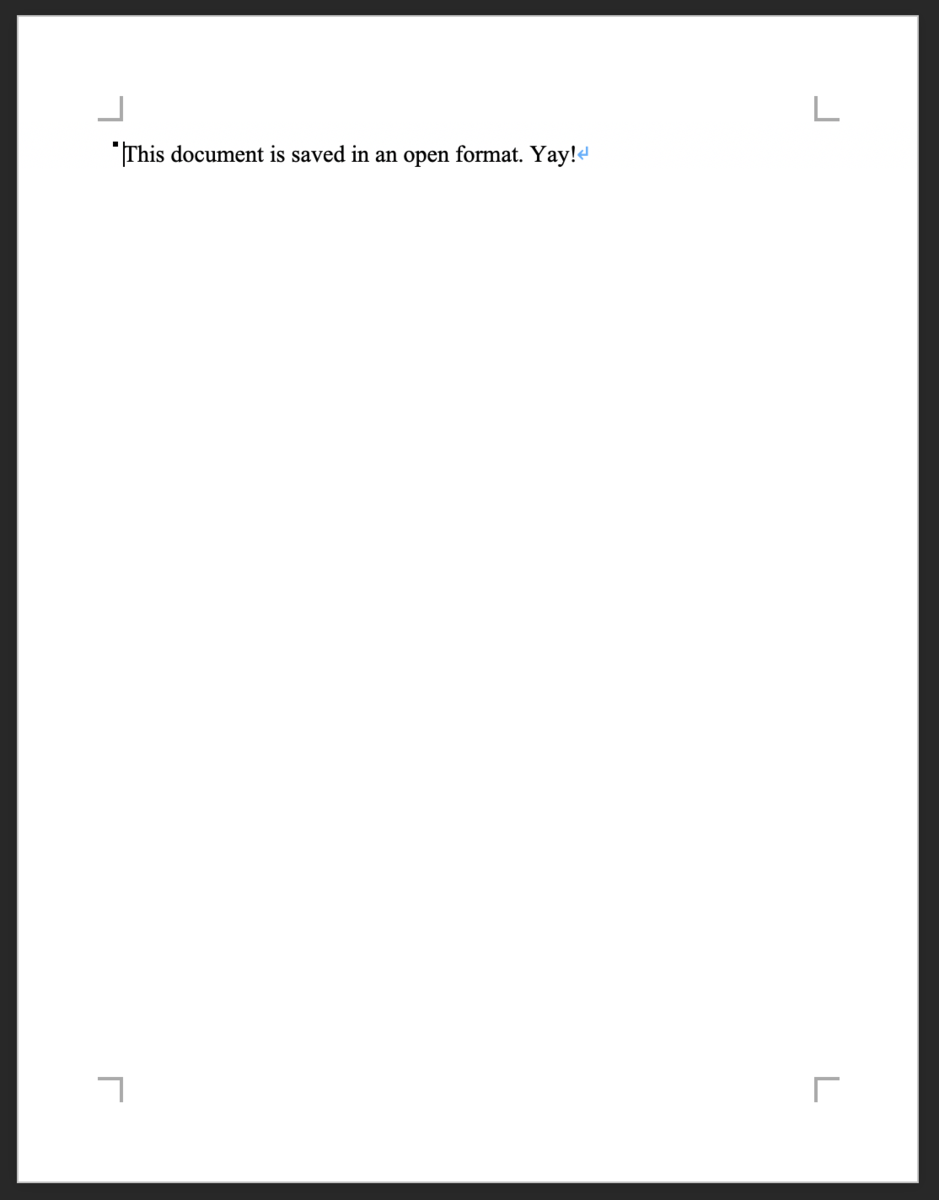
アプローチ:unzip
docxファイルをunzipして中身詳しく見ていきます.
> tree open
open
├── [Content_Types].xml
├── _rels
├── docProps
│ ├── app.xml
│ └── core.xml
└── word
├── _rels
│ └── document2.xml.rels
├── document2.xml
├── fontTable.xml
├── secrets.xml
├── settings.xml
├── styles.xml
├── theme
│ └── theme1.xml
└── webSettings.xml
5 directories, 11 files
secret.xmlに怪しいbase64テキストがあります.
<?xml version="1.0" encoding="utf-8"?> PHNlY3JldCBmbGFnPSJiY2FjdGZ7ME94TWxfMXNfNG00ejFOZ30iIC8+
> echo 'PHNlY3JldCBmbGFnPSJiY2FjdGZ7ME94TWxfMXNfNG00ejFOZ30iIC8+' | base64 -D
<secret flag="bcactf{0OxMl_1s_4m4z1Ng}" />
bcactf{0OxMl_1s_4m4z1Ng}
study-of-roofs [150pts, 294solves]
My friend has always gotten in to weird things, and his recent obsession is with roofs. He sent me this picture recently, and said he hid something special in it. Do you think you could help me find it?

アプローチ:ファイル抽出
binwalkすると別のjpgが埋め込まれていることがわかります.
> binwalk dem_shingles.jpg DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 JPEG image data, EXIF standard 12 0xC TIFF image data, big-endian, offset of first image directory: 8 14689 0x3961 Unix path: /www.w3.org/1999/02/22-rdf-syntax-ns#"> <rdf:Description rdf:about="" xmlns:xmpMM="http://ns.adobe.com/xap/1.0/mm/" xmlns:stEvt= 1562983 0x17D967 JPEG image data, EXIF standard 1562995 0x17D973 TIFF image data, big-endian, offset of first image directory: 8 1568937 0x17F0A9 Unix path: /www.w3.org/1999/02/22-rdf-syntax-ns#"> <rdf:Description rdf:about="" xmlns:xmp="http://ns.adobe.com/xap/1.0/" xmlns:xmpMM="http 1573688 0x180338 Copyright string: "Copyright (c) 1998 Hewlett-Packard Company"
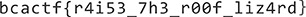
bcactf{r4i53_7h3_r00f_liz4rd}
wavey [150pts, 347solves]
My friend sent me his new mixtape, but honestly I don't think it's that good. Can you take a look at it and figure out what's going on?
> file straightfire.wav straightfire.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 22050 Hz
アプローチ:スペクトログラム
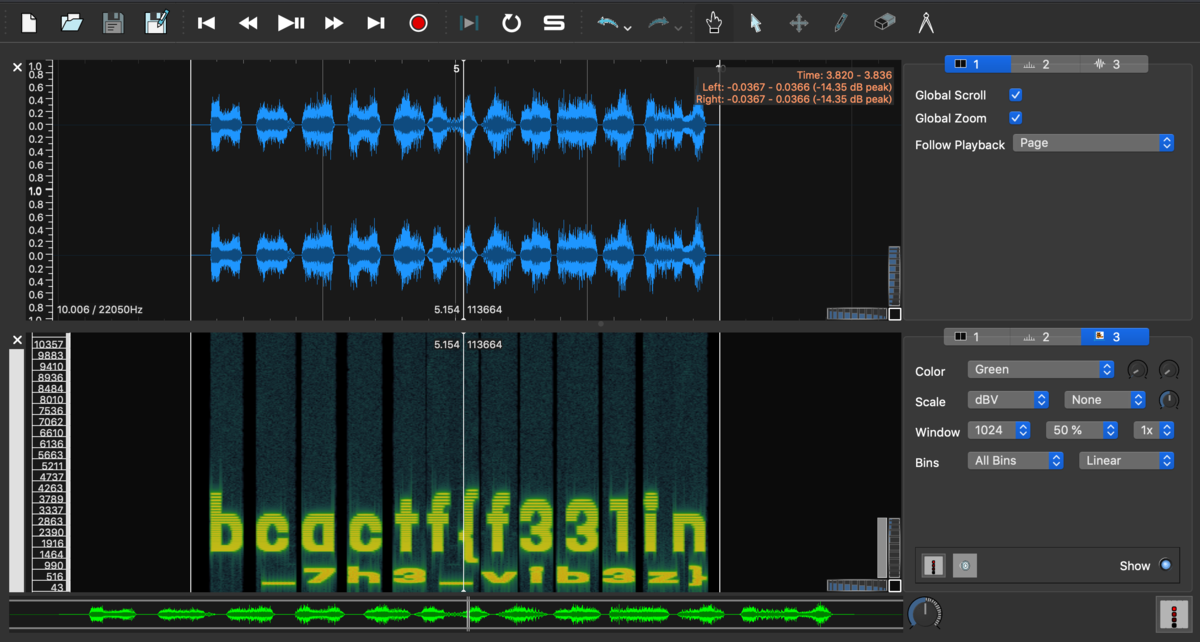
bcactf{f331in_7h3_vib3z}
corrupt-psd [200pts, 343solves]
I wanted to use Photoshop to embiggen my head, but er... something happened. It looks like Photoshop isn't the signature image editing program it used to be.
> file flag.psd flag.psd: data
アプローチ:マジックナンバー

バイナリエディタでflag.psdを開くとヘッダがOOPSになっていることが分かります.
本来のpsdファイルのヘッダは0x38425053なのでヘッダを修正します.
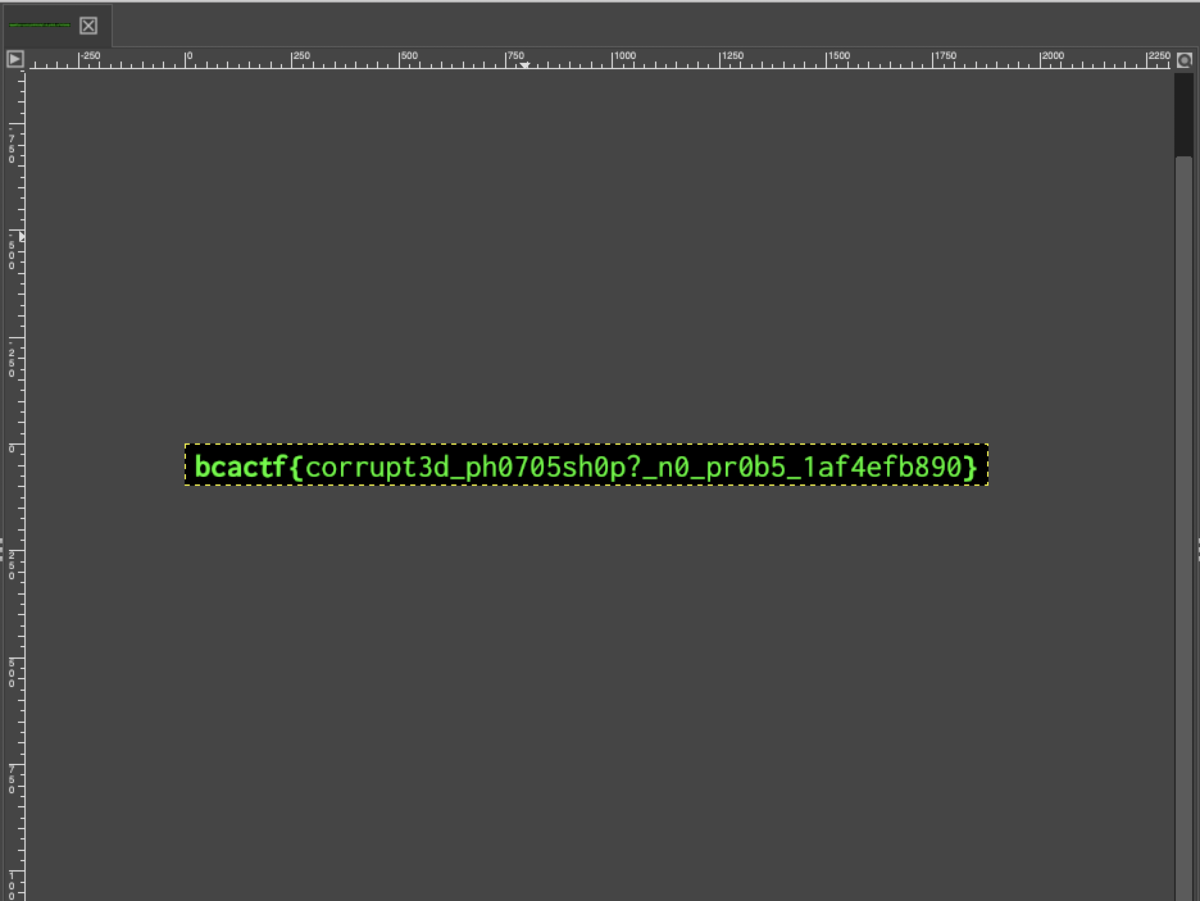
bcactf{corrupt3d_ph0705sh0p?_n0_pr0b5_1af4efb890}
the-flag-is [200pts, 377solves]
I have a flag! The flag is... wait... did my PDF editor not save the flag? OH NO! I remember typing it in, can you help me find it?
> file flag.pdf flag.pdf: PDF document, version 1.3

アプローチ:foremost
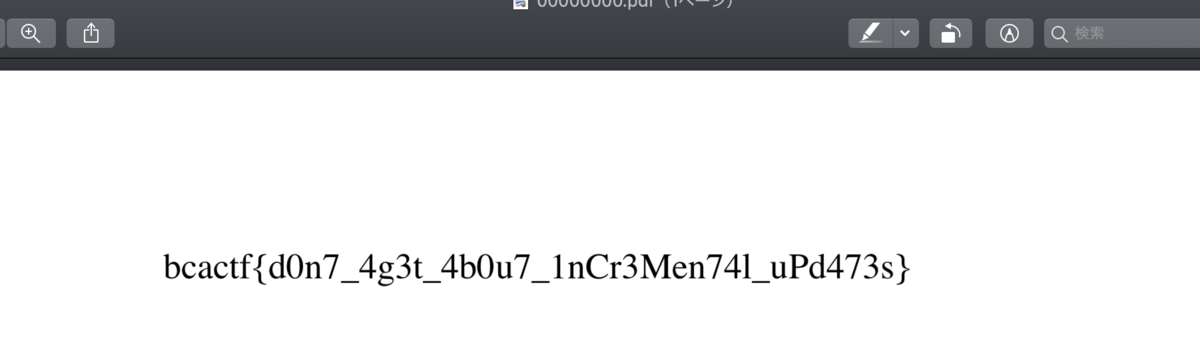
bcactf{d0n7_4g3t_4b0u7_1nCr3Men74l_uPd473s}
Programming
1+1=window [75pts, 307solves]
hex+hex=hex
> file one.txt two.txt one.txt: ASCII text two.txt: ASCII text
one.txt
0x23 0x49 0x16 0x46 0x45 0x16 0x3c 0x3c 0x45 0x64 0x16 0x37 0x3c 0x3c 0x3c 0x16 0x46 0x45 0x37 0x1e 0x49 0x16 0x46 0x49 0x16 0x1e 0x16 0x32 0x32 0x3c 0x32 0x49 0x3c 0x64 0x1e 0x32 0x3c 0x18 0x64 0x32 0x32 0x50 0x14 0x64 0x32 0x5a 0x45 0x32 0x32 0x55 0x50 0x49 0x3c 0x14 0x3c 0x5f
two.txt
0x26 0x2b 0x0a 0x23 0x2e 0x0a 0x29 0x25 0x2e 0x15 0x0a 0x37 0x25 0x25 0x2c 0x0a 0x23 0x2e 0x37 0x09 0x2b 0x0a 0x23 0x2b 0x0a 0x21 0x0a 0x30 0x31 0x25 0x31 0x2b 0x2a 0x17 0x13 0x2d 0x2c 0x18 0x0c 0x01 0x2d 0x29 0x1c 0x11 0x2d 0x1b 0x2e 0x01 0x2d 0x1b 0x29 0x2b 0x2c 0x1c 0x32 0x1e
アプローチ:足す
with open('./one.txt') as f: one = f.readline().strip().split(' ') with open('./two.txt') as f: two = f.readline().strip().split(' ') flag = [chr(int(o[2:], 16) + int(t[2:], 16)) for o, t in zip(one, two)] print(''.join(flag))
It is easy naah isn't it ? bcactf{1_h0p3_y0u_us3_pyth0n}
bcactf{1_h0p3_y0u_us3_pyth0n}
bca-store [75pts, 247solves]
You are a cashier for a small store that sells a few items. Coming up is the annual sale, and you really don't want to do that much math. So, being you, you decide to automate it.
You are a cashier for a small store that sells a few items. Coming up is the annual sale, and you really don't want to do that much math. So, being you, you decide to automate it. Items: A: $45, no sale B: $52, buy one get one 10% off C: $67, buy one get one half off D: $75, buy two get one free Input: What the customer ordered, separated by spaces. The amount the customer paid. For example, C B B C A 250. The input file is attached. If we had the above twice, then you can use the following to test on your local machine: C B B C A 250 D A B B 250 D D D D D A B 390 5.70 31.20 -1
input.txt
C B B C A 250 A C D A 230 A B C D 240 D D D 225 A A A A 150 A A A A B B B B B C C C C C D D D D 1000 A A A A B B B B B C C C C C D D D D 900
アプローチ:普通に計算する
クソコードになってしまった
import fileinput flag = '' for line in fileinput.input(): print('-' * 100) A_cnt = 0 B_cnt = 0 C_cnt = 0 D_cnt = 0 problem = line.strip().split(' ') paid = int(problem[-1]) for x in problem[:-1]: if x == 'A': A_cnt += 1 elif x == 'B': B_cnt += 1 elif x == 'C': C_cnt += 1 else: D_cnt += 1 print(problem) print(A_cnt, B_cnt, C_cnt, D_cnt) ans = paid - (A_cnt * 45 + B_cnt//2*52*0.9 + (B_cnt - B_cnt//2)*52 + C_cnt//2*67*0.5 + (C_cnt - C_cnt//2)*67 + (D_cnt - D_cnt//3)*75) print('{:.2f}'.format(ans)) if ans < 0: flag += '-1 ' else: flag += '{:.2f}'.format(ans) + ' ' print(flag)
5.70 -1 1.00 75.00 -1 77.40 -1
instructions [175pts, 320solves]
We intercepted a message between two agents from a terrorist group known as 0x4556494c. We think it might contain some useful information, so we'd like you to crack it. Here is the message.
Dear Agent Reffef, I have attached the super secret plans for operation 0x576f726b206f6e207468652070757a7a6c652c2073746f702072656164696e672068657821. You will need to decode it first though. The rules are simple: A line is "viable" if the length of a line is divisible by 3, and the line does not contain the `&` character. For every viable line, you will grab the `n`th character, where `n` is the corresponding number at the top of the file (Counting from one!) The first viable line will use the first number, etc. Put all the letters together to find the answer! - Agent Doposi
> wc -l flag.txt
1656 flag.txt
flag.txt
20 30 8 14 17 24 44 19 17 29 20 34 35 27 42 34 7 25 7 21 8 38 13 25 14 13 42 14 20 23 3 27 38 9 18 41 3 11 35
X=yU|(}J=|%Std-RtJ)hWb^+)$F$Usne}u7UaTB50+Yn52#(Zj9(j[PW61|}c++%*I+a6O9li\89M;)
V6Em{hdTl#5nc:xb0zPj1KqhlrS;pIGTUtM&94BXY-r0x1#OTd6yD-
]t!xTzZg-Yz|#+Av*Ha[#Ps;l$d+;whUGx64C^n]Jt\XG)%eUoR4K{KZyTUFLY^xsuX}g%3W+
C0+FQdv\IZGkP8rk-|FirmeqgtPHpfp$OM_6hm=b9[:bV]
YHsM5*w43A]btgOX_(9FFfNv)\12IhwLf:-b0_9m
1cTwC]Sp%LUoRnDr}fzPvA]tQ9BgGhIT&i0kIr[60[kV7Lnh5#CUs\f}tuyP{-L7FvLXQCHHp}t)W6
\IPx6FXK7dNj%cyot*eGpAj4Mm7hKvs1-4-So5pwfwA1-gDZ=1Rj\vBxp9dtJOv[R@}ng])UjO}g
+\;XqU#{#u^x:i[SjqozO)vGQ9x&2Go:oGH49C#fU\vH+l1mMk]:w;W:@|P+svp
Xu2AcLyn*&c2$2+pZxe-bTcFCzmxhU;x}AOXBg8veQ}BzFrSD@RtKRN{hRqQptj-DEz$U3@rlRH
[snip]
アプローチ:ルールに従って実装する
文字列長が3の倍数であり,&を含んでいないテキストを抽出し,x文字目を参照します.
flag = '' with open('./flag.txt') as f: msg = [line.strip() for line in f.readlines()] secret_lines = [] for x in msg[1:]: if len(x) % 3 == 0 and '&' not in x: secret_lines.append(x) for secret, secret_line in zip(msg[0].split(' '), secret_lines): flag += secret_line[int(secret,10) - 1] print(flag)
bcactf{f0110w_tH3_r00lz_<3_l0ve_m3_pls}
public-library [200pts, 404solves]
Hidden in this mysterious public library is the flag. Can you get it?
> file PublicLibrary.class PublicLibrary.class: compiled Java class data, version 52.0 (Java 1.8)
アプローチ:strings
> strings PublicLibrary.class | grep bcactf
,bcactf{t4k3_4_j4v4_c7a55_789208694209642475}
bcactf{t4k3_4_j4v4_c7a55_789208694209642475}
これ系(デコンパイルして系)の問題出すならflagを生で保持していてはダメなのでは…
manner-of-thpeaking [250pts, 191solves]
Tho, I came Acroth thith therieth of inthturcthins, and thomething that thaid "the key ith the attached litht of ATHCII printableth." Tho anywayth, here'th the inthtructhinth.
printableth.txt
(( !\"#$%&'\(\)*+,-./)(0123456789)(:;<=>?@)(ABCDEFGHIJKLMNOPQRSTUVWXYZ)(\[\\\]^_`)(abcdefghijklmnopqrstuvwxyz)(\{|\}~))
inthtructhins.txt
cadadddddr, caddadddddr, caadddddr, caddadddddr, cadddddddddddddddddddadddddr, cadddddadddddr, caaddddddr, cadddddddddddadddr, cadadr, cadddddadr, cadddddddadr, caddddaddddr, caddddddddadr, caddddadr, cadddddadr, cadddadr, cadddadddddr, caddddaddddr, cadddddddddddddddadddddr, cadddddddddddddddddadddr, caadr, caddddddadddddr, cadddddddddddddddddadddr, caddddadr, caddddddddddddadddr, caddddddddddddadddddr, cadadr, cadddddddddddddadddddr, caddddddadddr, caddddaddddr, cadadr, cadddddadr, caddddaddddr, caddddadr, caddddddddddddddddddddddadddddr, cadddadr, caddddddddddddddddddadddr, caadr, caddddddddddddadddr, caddddadddddr, cadar, caddaddddddr
アプローチ:CARとCDR
inthtructhins.txtのコマンドがlispのCARとCDR(リストを操作するための基本的な2つの関数)っぽく見えたのでそれっぽい処理を実装します.
printables = [' !\"#$%&\'()*+,-./', '0123456789', ':;<=>?@', 'ABCDEFGHIJKLMNOPQRSTUVWXYZ', '[\\]^_`', 'abcdefghijklmnopqrstuvwxyz', '{|}~'] flag = '' with open('./inthtructhins.txt') as f: cmds = f.readline().strip().split(' ') for cmd in cmds: d_count = 0 s = printables for x in cmd[1:-1][::-1]: if x == 'd': d_count += 1 elif x == 'a': s = s[d_count:][0] d_count = 0 flag += s print(flag)
bcactf{L157_8453d_pR0gR4Mm1nG_15_4w3S0Me!}
Quest
for-the-night-is-dark-1 [150pts, 254solves]
Hello, traveler. Welcome to your quest. You must walk the Red Lord's shining path, guided by his shining stars. Here is a picture of those stars. A map if you will. May the Lord of Light give you wisdom.
> file starmap.bmp starmap.bmp: PC bitmap, Windows 3.x format, 63 x 63 x 24

アプローチ:R value to ascii
from PIL import Image img = Image.open('./starmap.bmp') size = img.size msg = '' for y in range(size[1]): for x in range(size[0]): rgb = img.getpixel((x,y)) if rgb[0] > 0: msg += chr(rgb[0]) print(msg)
> python solve.py http://rhllor.xyz/7h3fir31n0urh3ar75_d2VsY29tZSB0byBzdGVwIG9uZQ
ソルバを実行するとURLが出力されます.
飛ぶとflagがとれます.
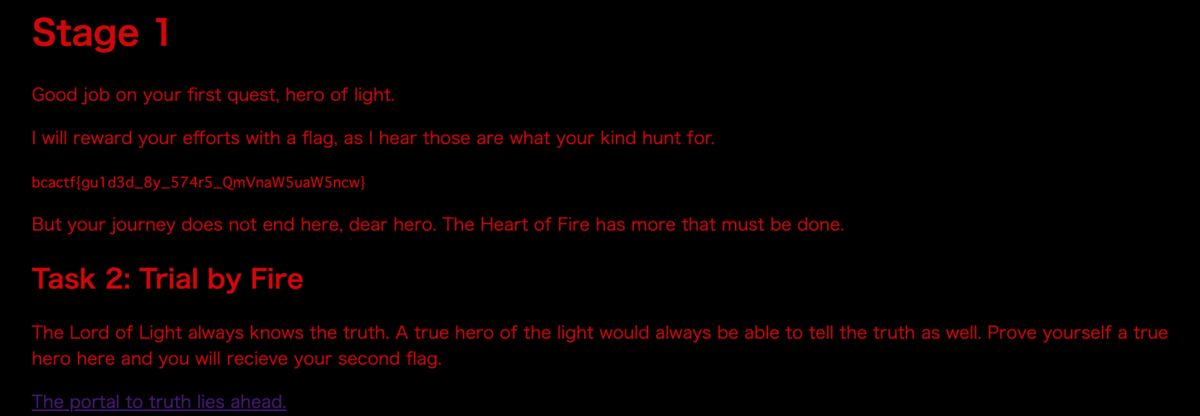
bcactf{gu1d3d_8y_574r5_QmVnaW5uaW5ncw}
for-the-night-is-dark-2 [150pts, 247solves]
The Lord of Light always knows the truth. A true hero of the light would always be able to tell the truth as well. Prove yourself a true hero here and you will recieve your second flag.
アプローチ:md5
stage2.js
$("#target").submit(function( event ) { var hash = md5($("#secret").val()) if (hash == "3758002ab24653af8d550c0c50473098") { var encode = "ÐßÏ½æ¦ ÐÞÙ֩û¤× úªîÈ©¼×ÐÖËÕ§£¢Íç«ÖÉ̱ÈÕÒßÊÕÅ" var newstr = "" var key = $("#secret").val() for (var i = 0; i < encode.length; i++) { newstr += String.fromCharCode(encode.charCodeAt(i) - key.charCodeAt(i%key.length)) } window.location = "/f" + newstr } $("#secret").val("") event.preventDefault(); });
入力値のmd5が3758002ab24653af8d550c0c50473098と一致すればflagがとれるようです.
上記のサイトによると3758002ab24653af8d550c0c50473098はdarknightのハッシュ値らしいです(厨二病か?.
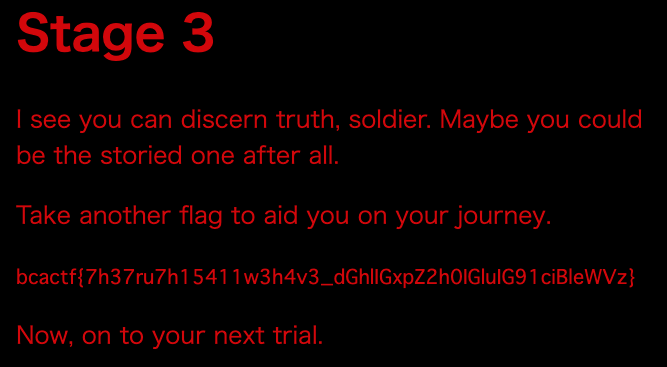
bcactf{7h37ru7h15411w3h4v3_dGhlIGxpZ2h0IGluIG91ciBleWVz}
Rev
basic-pass-1
Your company is testing out a new login software, and being one of the CompSec experts, they want you to test it. They say that they have hidden a key somewhere in the program, and want you to look for it. Find it, and they might even consider giving you a pay raise...
They have told you that there is a four digit pin on the program to unlock it.
> file basic-pass-1-linux basic-pass-1-linux: ELF 64-bit LSB shared object x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=9cee815c93440268757240e6499bc622fbbed466, not stripped
アプローチ:strings
> strings basic-pass-1-linux | grep bcactf{
Congrats! The key is bcactf{hey_its_a_password}
scratch-that [150pts, 433solves]
I made a Guess the Flag game! It's in Scratch, what could be easier? Click here to access the game.

アプローチ:ネコにflagを言わせる
generate flagをReversingするのはちょっと面倒なのでScratchのブロックの1つである***と***秒言う ブロックを使ってネコにflagを吐かせます.
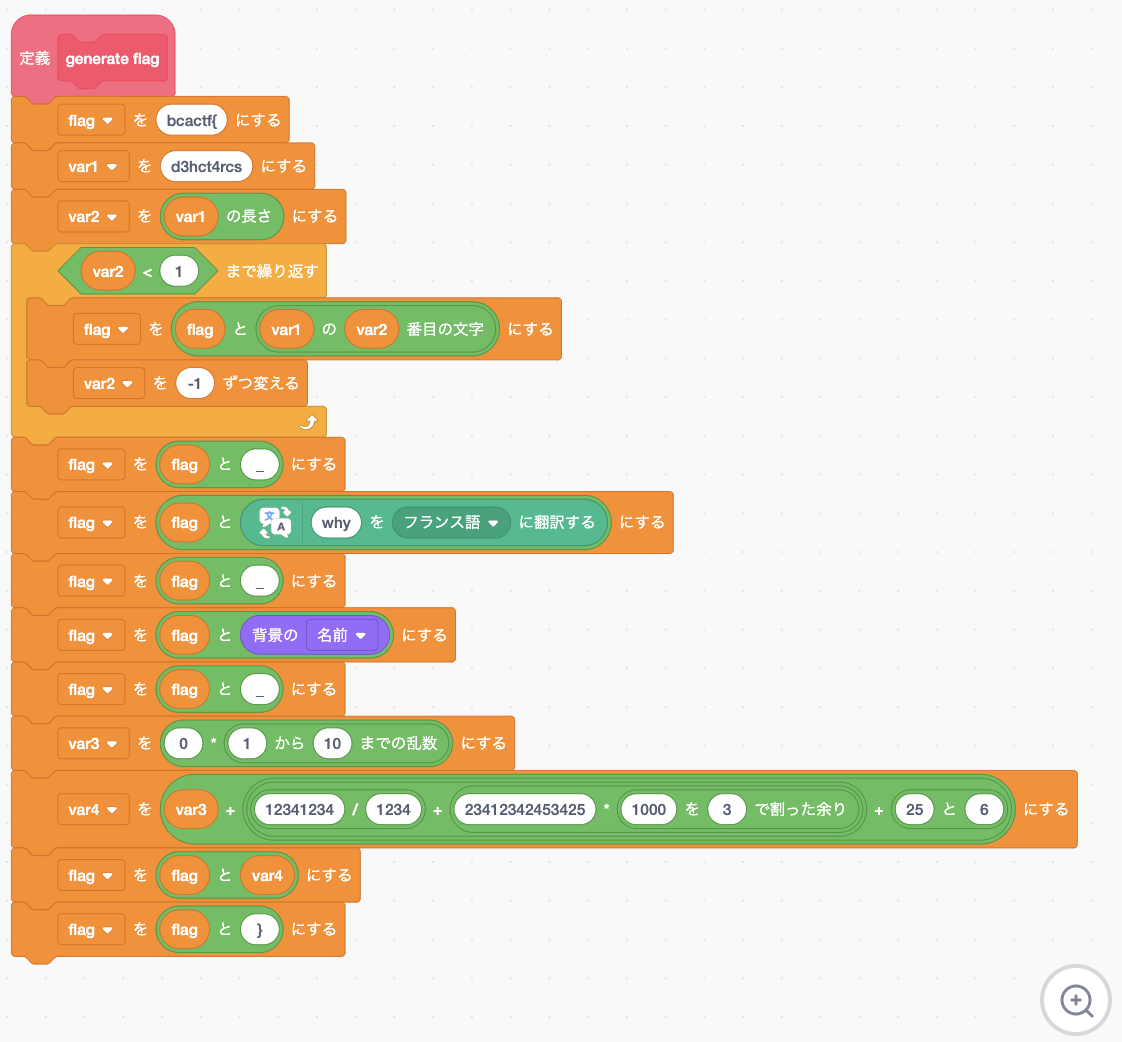

bcactf{scr4tch3d_Pourquoi_empty_23412342463682}
another-pass [200pts, 174solves]
Alright. Your friend John found this cool binary file on the Interwebz. Against all best practices, he downloaded it. Strange, it doesn't appear to be a virus. Because of the password prompt, you feel like it will lead to something important. Figure this one out!
> file another-linux another-linux: ELF 64-bit LSB shared object x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=d262a12229a4736c50637beb2133d07c1ea03c2c, not stripped
アプローチ:頑張って処理を追う
文字列の和が0x4bになるパスワードを入力するとCorrect.になるっぽいことが分かります.
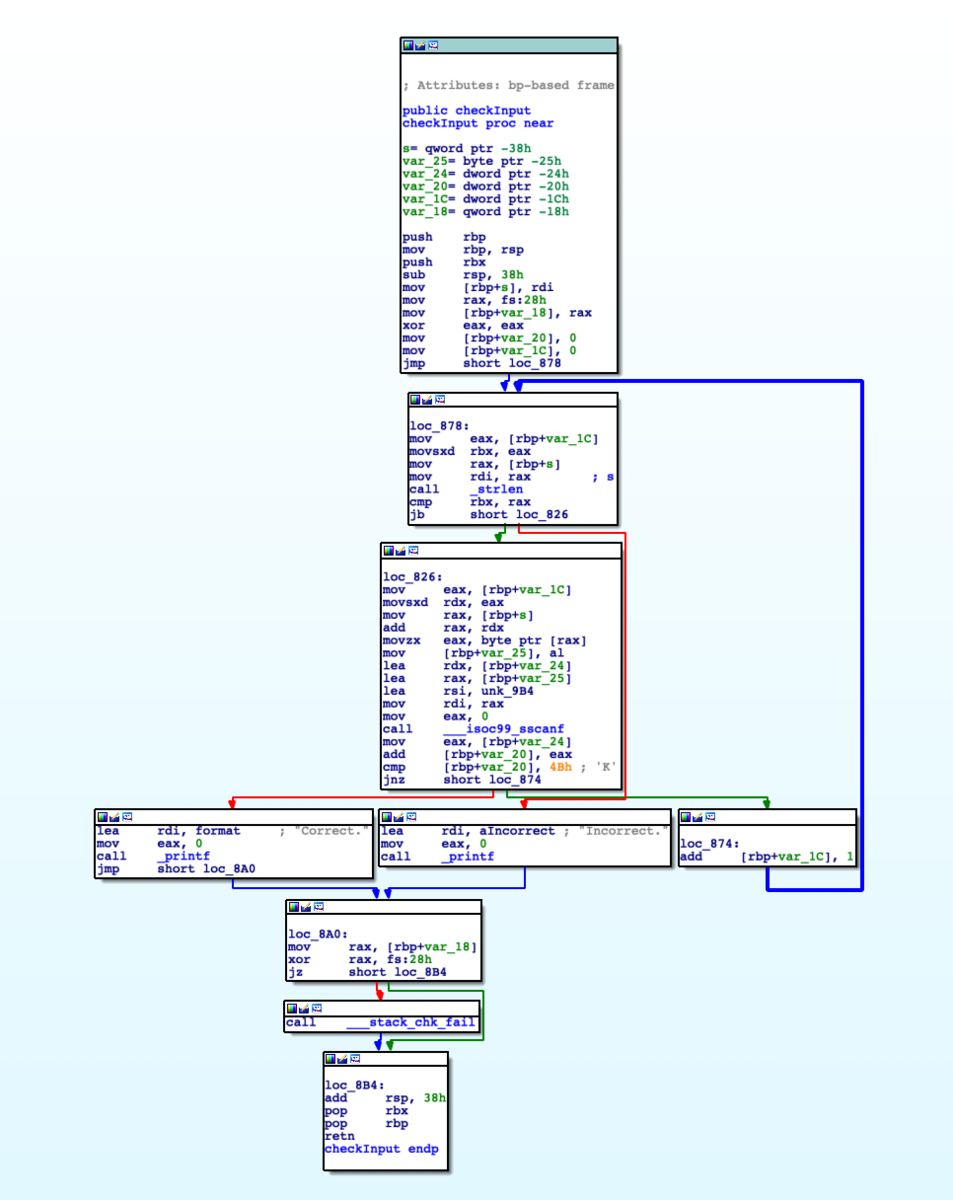
> ./another-linux Pass: 99999999111 Correct.
99999999111
これ何通りも正解があるし問題としてどうなの
basic-pass-2 [200pts, 449solves]
Your company is testing out its new employee portal. After your previous shot, they made the password a bit more secure, so you can't brute force it anymore. Rise up to the occasion and demonstrate why a local machine is a bad idea, and having the account credentials on a remote server is a better idea.
アプローチ:ltrace
ltraceしたらstrcmpを使って入力文字列のチェックをしていたので簡単にパスワードが分かります.
ltrace -s 100 ./basic-pass-2-linux "this is a much more secure password, i think"
strcmp("this is a much more secure password, i think", "this is a much more secure password, i think") = 0
puts("Congrats! The key is bcactf{its_another_password}"Congrats! The key is bcactf{its_another_password}
) = 50
+++ exited (status 0) +++
bcactf{its_another_password}
basic-pass-3 [200pts, 356solves]
Ok, the sysadmin finally admits that maybe authentication should happen on a server. Can you just check everything really quick to make sure there aren't any problems now? He put some readouts for people who forget their passwords.
nc challenges.ctfd.io 30133
> nc challenges.ctfd.io 30133
welcome to the login portal.
Enter the password.
hoge
00000000000000000000000000000000000000
Enter the password.
bcactf{
11111110000000000000000000000000000000
Enter the password.
アプローチ:全探索
flagのn番目の文字列が正しければn番目のbitが立つことが分かります.
from socket import * import string s = socket(AF_INET, SOCK_STREAM) s.connect(('challenges.ctfd.io', 30133)) flag = 'bcactf{' rec = s.recv(1024).decode('utf-8') for _ in range(32): pre_x = '' for x in string.printable: s.send((flag + x).encode('utf-8') + b'\n') rec = s.recv(1024).decode('utf-8') msg = rec.split('\n')[0][:(len(flag) + 1)] if '0' not in msg and '1' in msg: flag += pre_x print(flag) break pre_x = x
> python solve.py
bcactf{y
bcactf{y0
bcactf{y0u
bcactf{y0u_
bcactf{y0u_4
bcactf{y0u_4r
bcactf{y0u_4r3
bcactf{y0u_4r3_
bcactf{y0u_4r3_4
bcactf{y0u_4r3_4_
bcactf{y0u_4r3_4_m
bcactf{y0u_4r3_4_m4
bcactf{y0u_4r3_4_m45
bcactf{y0u_4r3_4_m457
bcactf{y0u_4r3_4_m4573
bcactf{y0u_4r3_4_m4573r
bcactf{y0u_4r3_4_m4573rm
bcactf{y0u_4r3_4_m4573rm1
bcactf{y0u_4r3_4_m4573rm1n
bcactf{y0u_4r3_4_m4573rm1nD
bcactf{y0u_4r3_4_m4573rm1nD!
bcactf{y0u_4r3_4_m4573rm1nD!_
bcactf{y0u_4r3_4_m4573rm1nD!_Y
bcactf{y0u_4r3_4_m4573rm1nD!_Ym
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9v
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9vb
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9vbG
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9vbGl
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9vbGlu
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9vbGlu}
bcactf{y0u_4r3_4_m4573rm1nD!_Ym9vbGlu}
compression [200pts, 301solves]
A stranger on the internet is giving away his passwords. They claim they are encrypted, but you quickly realize that it is only compressed. You have to get hold of their passwords so that you can prove them wrong.
> file 999 999: bzip2 compressed data, block size = 900k
アプローチ:bzip => gzip => bzip
999を解凍すると123ファイルが出現します.
123ファイルは何らかのファイルのhexdumpっぽいのでこれを復元します.
00000000: 1f8b 0808 348e 365c 0003 3531 3100 019d ....4.6\..511...
00000010: 0762 f842 5a68 3931 4159 2653 59f7 ed65 .b.BZh91AY&SY..e
00000020: dd00 006d 7fff ffff ffff ffff ffff ffff ...m............
00000030: ffff ffff 7fff ffff ffff ffff ffff 7fff ................
00000040: ffff ffff ffff d004 1ef7 79a5 af7b 65d7 ..........y..{e.
00000050: b9ce 6578 6453 d264 0f50 6991 ea3c 88f2 ..exdS.d.Pi..<..
00000060: 9ea1 a0f4 8d34 c434 643c 93d4 d0d3 ca3d .....4.4d<.....=
00000070: 468d 0327 a1a2 36a6 83d4 69a6 8c8d a9ea F..'..6...i.....
00000080: 6341 0191 e90f 28f5 068c d1a9 a69e a794 cA....(.........
00000090: 6d46 8c81 b506 c206 936a 7a9b d354 f53c mF.......jz..T.<
000000a0: a1e8 c90f d29a 69b5 10d1 a009 e826 9823 ......i......&.#
000000b0: d4d3 1320 6002 186a 3068 9813 6a69 9300 ... `..j0h..ji..
000000c0: 0001 3c84 c046 98d3 4980 1a0d 01a9 e826 ..<..F..I......&
000000d0: 0004 f47a 40d1 a4c3 4981 190c 9a69 9a98 ...z@...I....i..
000000e0: 0009 821a 24f2 261a 0460 1368 134c 04f4 ....$.&..`.h.L..
000000f0: 4c9a 6032 0119 3009 a7a3 4469 e9a3 44f4 L.`2..0...Di..D.
00000100: 098d 23d3 2989 b203 4041 a323 4601 0c98 ..#.)...@A.#F...
00000110: 0133 5193 d04f 200d 00d4 c10c 9a69 e9a9 .3Q..O ......i..
00000120: 91a6 130d 263a 9ea3 1a46 9e50 dea8 f518 ....&:...F.P....
00000130: 46d4 d8a6 86d4 7a64 d314 69a7 b532 834d F.....zd..i..2.M
00000140: 313c 834d 4f14 f51e 9368 8d1a 7a41 8868 1<.MO....h..zA.h
00000150: c4c8 3d4f 51a3 d46d 2611 b534 7a4c 2794 ..=OQ..m&..4zL'.
00000160: c4f5 0f24 3d23 d468 3464 f49a 1934 3681 ...$=#.h4d...46.
00000170: 0f53 d468 d34d 1e44 c41d 1ea6 84f5 3d26 .S.h.M.D......=&
00000180: 344d 306a 7a13 d027 a341 a340 98d2 7a20 4M0jz..'.A.@..z
00000190: c27a 04c0 689e 8000 11a6 9ea6 099a 9846 .z..h..........F
000001a0: d081 a0c4 da04 f531 327a 0119 a21b 499a .......12z....I.
000001b0: 9a7a 0261 184c 8699 06d1 1930 3426 5722 .z.a.L.....04&W"
000001c0: 054b 04b9 6f83 285d e411 270c 9d3b 1727 .K..o.(]..'..;.'
000001d0: dbfc 8629 e02c da67 7450 5730 d011 a8d0 ...).,.gtPW0....
000001e0: 887a 84b4 093b f9bd 408e 1e60 a318 419d .z...;..@..`..A.
000001f0: 99e8 b139 b31d b8c1 8310 8380 863d 737b ...9.........=s{
00000200: fd2b f4df 3c6e 030e ea17 73f4 b0f5 73ef .+..<n....s...s.
00000210: 382f 880d 7672 3b34 b9db b9c7 de29 c6aa 8/..vr;4.....)..
00000220: e5f4 df56 4968 8a62 9734 a614 cf46 8a6a ...VIh.b.4...F.j
00000230: 1507 b984 8400 32cf d8e0 1f7c 324d eba8 ......2....|2M..
00000240: d360 4b80 d091 0e11 0c61 5a73 94db c820 .`K......aZs...
00000250: d5a0 08df c32a 20d1 92dd de81 bc49 a54f .....* ......I.O
00000260: ad98 51f2 6b51 3bae 165d 8e30 873e d8ef ..Q.kQ;..].0.>..
00000270: 0280 7f49 ca02 3451 7e49 a407 c418 e3a8 ...I..4Q~I......
00000280: 4cc6 9b07 003d 4ac0 a963 c186 8df1 4a95 L....=J..c....J.
00000290: fd92 9903 75d3 16b2 1f60 f99c d118 e7c1 ....u....`......
000002a0: 23bf 452b 11e3 d096 f1c6 464a bbee 4893 #.E+......FJ..H.
000002b0: 28d6 e813 0c68 8088 004f ce0a 805d c5d7 (....h...O...]..
000002c0: c5a4 bb71 5289 9e9d 4cd4 071c 4831 339d ...qR...L...H13.
000002d0: cdcc 8ec3 a823 a062 f450 b5c6 2415 abd3 .....#.b.P..$...
000002e0: faf8 ff82 46aa 9ec5 cf5f 38e5 ff71 9ed1 ....F...._8..q..
000002f0: 4bcf 8e8d a8c7 320a f5a8 375c c3f5 ef84 K.....2...7\....
00000300: 29fc 91b1 ac85 c677 d1fd e134 240f 0e8d )......w...4$...
00000310: 93ee 7d80 ab73 5a9d cf4e 4b9e 60bc 5c41 ..}..sZ..NK.`.\A
00000320: 0ac9 687d 2d04 039c c382 f516 b54b 3d4c ..h}-........K=L
00000330: 7e1a 3336 a410 985a e0e3 e25e 4e2a 9bfe ~.36...Z...^N*..
00000340: 5f92 e1bd 5909 13e4 2049 4a45 871c ea07 _...Y... IJE....
00000350: 1705 b805 bfc7 20c1 6b2f 8b90 4e7d 7e50 ...... .k/..N}~P
00000360: 8c24 a043 d655 6a8d f32c 09ce f12d 26dc .$.C.Uj..,...-&.
00000370: 23b4 98a4 d647 2383 0b72 7152 045a 8e80 #....G#..rqR.Z..
00000380: fa4e 8790 5480 7d5e 989c 41ea 158a 4e23 .N..T.}^..A...N#
00000390: 4518 d97a 6fef a53e c075 5a48 1813 de0c E..zo..>.uZH....
000003a0: 7503 226c bb73 2ae6 d01e c44b 68ad 8767 u."l.s*....Kh..g
000003b0: 0532 5c0b 84cf 9e8a 3b8f b661 8b02 b748 .2\.....;..a...H
000003c0: 672a 4d4d 0702 2899 c021 76b7 3d6d 2a85 g*MM..(..!v.=m*.
000003d0: 2bcb 6014 3a6d ee03 2d7b 5e92 1211 e320 +.`.:m..-{^....
000003e0: 7725 aa83 57fa 9243 e877 c62a 73a2 f589 w%..W..C.w.*s...
000003f0: 10b0 e323 5203 a52c 504d c5b7 1170 e87d ...#R..,PM...p.}
00000400: 8327 11fa e4ca d8be 03c2 cbe4 f16c cf75 .'...........l.u
00000410: b20b ac94 855a 485d 1dde e8dc 78a0 d116 .....ZH]....x...
00000420: c58f 1f69 e4ff bd9b e180 7c84 2048 e26d ...i......|. H.m
00000430: 5fa1 5c2b 11b4 cf67 de67 2619 841a 71d4 _.\+...g.g&...q.
00000440: da3c 658d 2bca b130 ff83 7f4c a932 bc84 .<e.+..0...L.2..
00000450: 2565 fd66 8925 1d73 2904 5eb2 1ed2 4fb1 %e.f.%.s).^...O.
00000460: 2922 82a4 9f88 f0f4 e082 2774 9da2 a8c7 )"........'t....
00000470: 3649 d1e9 52ce 9814 8b9b 1430 b977 cfcd 6I..R......0.w..
00000480: 65fb 17e8 9b4a 68d2 c114 ca93 5856 f8f9 e....Jh.....XV..
00000490: 05a4 2709 4983 b7f3 8e13 72e4 b2fe b557 ..'.I.....r....W
000004a0: 748b 6bed ddbc d3a9 816a d750 0a92 b2fe t.k......j.P....
000004b0: 4290 8c32 4b9e 7b27 2afe 83fc 9594 3c1d B..2K.{'*.....<.
000004c0: 34b9 9092 1a0b 4857 13eb 9d25 eaf0 3562 4.....HW...%..5b
000004d0: cde8 cf39 9492 8952 cb53 1823 6909 0fef ...9...R.S.#i...
000004e0: 34c1 8dac c38e 1d0e fd7a 4667 6edd 98d7 4........zFgn...
000004f0: f995 2f2e 2f8d 2c51 b81d 535e e047 f033 .././.,Q..S^.G.3
00000500: 84fb a724 c117 b45d fad9 6b26 87df f3c8 ...$...]..k&....
00000510: 9180 005f 6e7d 9c76 3173 61ee d89e 60d0 ..._n}.v1sa...`.
00000520: e83d d3a1 9865 298b 493a fd78 5d23 61c4 .=...e).I:.x]#a.
00000530: 0527 3d55 6f5b c9b9 fc83 aa8f 0cf6 ce7f .'=Uo[..........
00000540: 2d27 c625 6882 a80b 7596 0563 4d29 a920 -'.%h...u..cM).
00000550: 59af a871 8db1 768e a400 14c5 4e19 800c Y..q..v.....N...
00000560: fa15 6c55 e041 bc98 6682 c601 8114 e994 ..lU.A..f.......
00000570: 3613 5c8e afc4 86cc 199b ec6c b7a9 0da6 6.\........l....
00000580: 4a89 4e0a 48eb 314c 0a80 7141 c53f d7db J.N.H.1L..qA.?..
00000590: 40c2 343e 00b6 7573 758d b795 292f c2a5 @.4>..usu...)/..
000005a0: ab7a 85ab 26f1 cc96 7c05 7dd4 8661 6d68 .z..&...|.}..amh
000005b0: 2513 ee39 33a0 6fc6 b437 f070 4be8 fee2 %..93.o..7.pK...
000005c0: 3f3f 2d0c 3005 d554 743e e716 f3fb 59af ??-.0..Tt>....Y.
000005d0: 9181 1715 c470 8269 fb36 da47 b97b 5a54 .....p.i.6.G.{ZT
000005e0: b434 f892 3dea d2b5 6fe0 02db b126 eb0a .4..=...o....&..
000005f0: 4c81 417d 19d0 f77f 2ea2 d6ab 8dd5 1d2e L.A}............
00000600: 2e97 0bec 8c09 1345 26ca 8abe d3cf e06e .......E&......n
00000610: 3d84 3710 5023 e29d 8211 9508 4a6e e878 =.7.P#......Jn.x
00000620: ca43 fa05 9e52 a57f 2239 7c39 b6a2 98c7 .C...R.."9|9....
00000630: 6f4a 53af 708d 67af 2c2f c5e3 4577 dd9f oJS.p.g.,/..Ew..
00000640: 244f 6460 5851 f703 54f2 0994 956c efbe $Od`XQ..T....l..
00000650: 72c7 4ca3 0f98 2310 f0de 56f7 fa8a a6cf r.L...#...V.....
00000660: 0d34 1a52 c1db 569d 17d8 c202 1d7a 7432 .4.R..V......zt2
00000670: 68f4 c57d c535 e3d3 aea4 9d2c 8a55 4456 h..}.5.....,.UDV
00000680: 106c 4d60 374a c41e 5500 5425 3975 1298 .lM`7J..U.T%9u..
00000690: d484 7125 9d2f 237a f054 7352 d72d 9a57 ..q%./#z.TsR.-.W
000006a0: 874b b8a7 f69e 6bac 1e54 7319 b45f 6f10 .K....k..Ts.._o.
000006b0: 66d1 6d24 f0d0 5808 58a0 acb3 a294 a823 f.m$..X.X......#
000006c0: 77fb 0e29 bb37 946a 6919 bd0a 9e5b 8b01 w..).7.ji....[..
000006d0: 1cc6 b86d 71d9 1ad1 6ee1 0344 d244 0086 ...mq...n..D.D..
000006e0: 95a0 30bd 0d42 e51c 56a9 a37a bafc 561f ..0..B..V..z..V.
000006f0: 9d78 1db5 1f61 4778 f82a 2040 16c9 e6f1 .x...aGx.* @....
00000700: b309 e7c1 50d6 a645 c305 473d 7906 7404 ....P..E..G=y.t.
00000710: c807 ea26 a4cd 408d c1c9 0e05 e286 235d ...&..@.......#]
00000720: 177e 0f68 a5b7 4d67 8d41 16be 8c57 e0ce .~.h..Mg.A...W..
00000730: d637 c69a d7b0 68cd f71d 39b6 e954 993c .7....h...9..T.<
00000740: 1ddc 097c f740 88c5 5c17 49bc bf38 97e5 ...|.@..\.I..8..
00000750: 77a9 9da5 61b9 711c 2d32 955a 8467 e1f5 w...a.q.-2.Z.g..
00000760: b6b1 794c 6d90 9eb4 522a 0711 86a7 7f38 ..yLm...R*.....8
00000770: c688 392a 8304 04ff c8a0 337e c2d7 49e0 ..9*......3~..I.
00000780: 594d 598d 9230 000d ef2f ba8e e1ce a6d2 YMY..0.../......
00000790: 20f3 4460 9a69 08ad 2833 8854 878c b81c .D`.i..(3.T....
000007a0: f301 c582 0fbe 2ee4 8a70 a121 efda cbba .........p.!....
000007b0: e0a3 c611 9d07 0000 ........
> file output_from_123 output_from_123: gzip compressed data, was "511", last modified: Thu Jan 10 00:13:40 2019, from Unix, original size 1949
復元結果はgzipだったのでこれを解凍すると240ファイルが出現します.
240ファイルも何らかのファイルのhexdumpっぽいので再度復元します.
00000000: 425a 6839 3141 5926 5359 51cd bcbb 0000 BZh91AY&SYQ.....
00000010: 24ff ffff fde7 4eff cd5f ffab df7c ddff $.....N.._...|..
00000020: ff6c 7bff ed5b e8ff f5fd 7fff ffde ffff .l{..[..........
00000030: 97ff bfb0 0159 99a0 ca00 69a0 d00d 0006 .....Y....i.....
00000040: 8000 0068 0000 0000 0000 01a7 a83d 41a0 ...h.........=A.
00000050: 0320 6832 000d 3400 34d0 c206 9826 d350 . h2..4.4....&.P
00000060: 5526 9ea3 4c81 a346 8034 0000 00f5 0d01 U&..L..F.4......
00000070: 90f5 0000 0000 0190 1900 d00c 9a00 c8d0 ................
00000080: 34d0 0000 341a 0d00 000a a23d 41a0 d1a6 4...4......=A...
00000090: 8340 0f53 20d0 0064 1a00 0006 9a00 00c8 .@.S ..d........
000000a0: 3400 1a00 001a 340f 5000 01a0 0640 069a 4.....4.P....@..
000000b0: 6868 0032 8c25 0a13 4849 9562 ebc5 e593 hh.2.%..HI.b....
000000c0: 108f 58e6 3000 343a 9c36 870e 77db d52e ..X.0.4:.6..w...
000000d0: 0001 ff2b 994e f837 b6da c385 3428 1c83 ...+.N.7....4(..
000000e0: 60cd 7e12 0010 3e1e 6204 5953 4636 3cb3 `.~...>.b.YSF6<.
000000f0: 9ac3 4936 11f3 694e dd4a 871b 0ce8 f659 ..I6..iN.J.....Y
00000100: 10e1 e006 f887 db92 4273 4a10 000c 3bed ........BsJ...;.
00000110: a0b0 7300 8409 1040 6a8b 98f5 6b24 ea3b ..s....@j...k$.;
00000120: b720 22f6 46db 75f0 12a1 fac0 afcf fcd5 . ".F.u.........
00000130: cf00 126d 0903 8636 8775 e869 434c e368 ...m...6.u.iCL.h
00000140: e95f 800a abcc 933a 4882 431b 3270 96a7 ._.....:H.C.2p..
00000150: be9d c773 8179 a851 4048 71d5 9620 f07c ...s.y.Q@Hq.. .|
00000160: afbc 0504 129a f6a2 1e67 e584 39f2 c48d .........g..9...
00000170: 2c10 5c00 6925 3f72 28f8 6f99 4fed 8454 ,.\.i%?r(.o.O..T
00000180: 5993 a5ca 707c 1c5d 4c44 3079 9d4a 9e3f Y...p|.]LD0y.J.?
00000190: dfeb e05f 4400 25cb df6f 1941 ed15 d350 ..._D.%..o.A...P
000001a0: 16fd 4fd8 af92 1013 1c49 c044 1c70 14c8 ..O......I.D.p..
000001b0: 911e e7d2 61e7 a525 7f11 65a7 8e64 08f3 ....a..%..e..d..
000001c0: 1d1b c5cd 91dd 1642 03eb 8691 1401 1059 .......B.......Y
000001d0: 232e 970d c982 e4a4 caa9 7e3e 5448 f054 #.........~>TH.T
000001e0: 4f0c 29f2 bafa 63b4 a991 d7c2 4eef 1342 O.)...c.....N..B
000001f0: 6773 ded6 49fd 1989 3cb3 8001 ad52 2d21 gs..I...<....R-!
00000200: 441c e65c 2a96 d234 de02 690f dfb1 1257 D..\*..4..i....W
00000210: 6e98 86c3 3aea 9444 32fa efea 3188 3d03 n...:..D2...1.=.
00000220: 426c b227 2a6e d4c3 e330 9ee2 461d 83db Bl.'*n...0..F...
00000230: 112a c222 c3dd a384 78bf 62d6 0d29 810d .*."....x.b..)..
00000240: 1dac a81d c234 10ab 17e7 0a7a 1390 37fa .....4.....z..7.
00000250: 73b0 6692 7933 fd6f 204f 61f1 838a 19ac s.f.y3.o Oa.....
00000260: 0ef1 99e4 d36d 7009 fc1f f8bb 9229 c284 .....mp......)..
00000270: 828e 6de5 d8 ..m..
> file output_from_240 output_from_240: bzip2 compressed data, block size = 900k
復元結果はbzipだったのでこれを解凍すると000ファイルが出現します.
000ファイルがflagでした
bcactf{A_l0t_0f_c0mPr3s510n}
Web
the-inspector [50pts, 568solves]
The Federal CTF Inspector dropped by today looking for some hidden flags. He clearly needs to pursue a different career because we hid the flag right in plain sight.
アプローチ:inspect
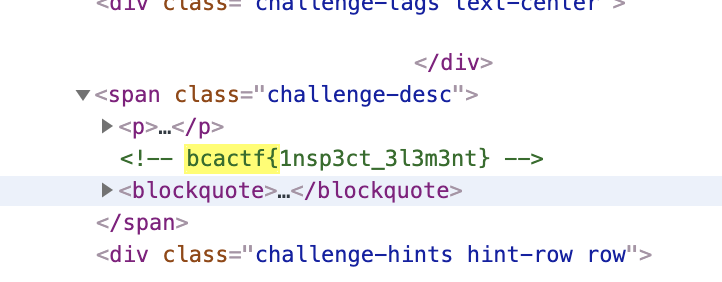
bcactf{1nsp3ct_3l3m3nt}
wite-out [50pts, 559solves]
Wait, where's the flag?
アプローチ:inspect
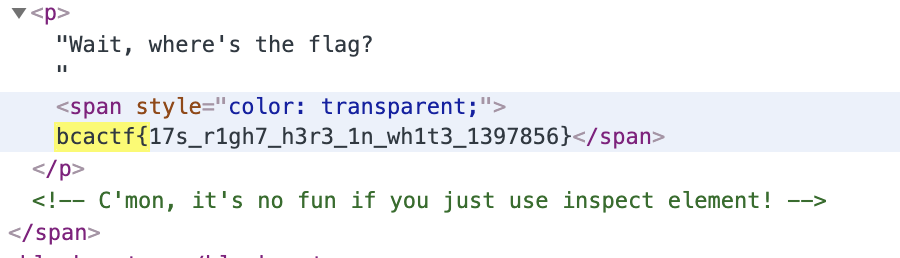
bcactf{17s_r1gh7_h3r3_1n_wh1t3_1397856}
dig-dug [100pts, 486solves]
I found this super sketchy website called hole.sketchy.dev. Can you help me dig up some of its secrets?
Oh, and someone told me that the secrets are TXT. I don't know what this means, so good luck!
アプローチ:dig
> dig -t TXT hole.sketchy.dev
; <<>> DiG 9.10.6 <<>> -t TXT hole.sketchy.dev
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20628
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;hole.sketchy.dev. IN TXT
;; ANSWER SECTION:
hole.sketchy.dev. 3600 IN TXT "bcactf{d1g-f0r-h073s-w/-dns-8044323}"
;; AUTHORITY SECTION:
sketchy.dev. 10737 IN NS molly.ns.cloudflare.com.
sketchy.dev. 10737 IN NS greg.ns.cloudflare.com.
;; ADDITIONAL SECTION:
molly.ns.cloudflare.com. 154304 IN A 173.245.58.205
molly.ns.cloudflare.com. 154304 IN AAAA 2400:cb00:2049:1::adf5:3acd
;; Query time: 15 msec
;; SERVER: 192.168.2.1#53(192.168.2.1)
;; WHEN: Tue Jun 11 20:36:17 JST 2019
;; MSG SIZE rcvd: 194
bcactf{d1g-f0r-h073s-w/-dns-8044323}
cookie-clicker [150pts, 550solves]
My friend built a cookie clicker. How do I beat it?
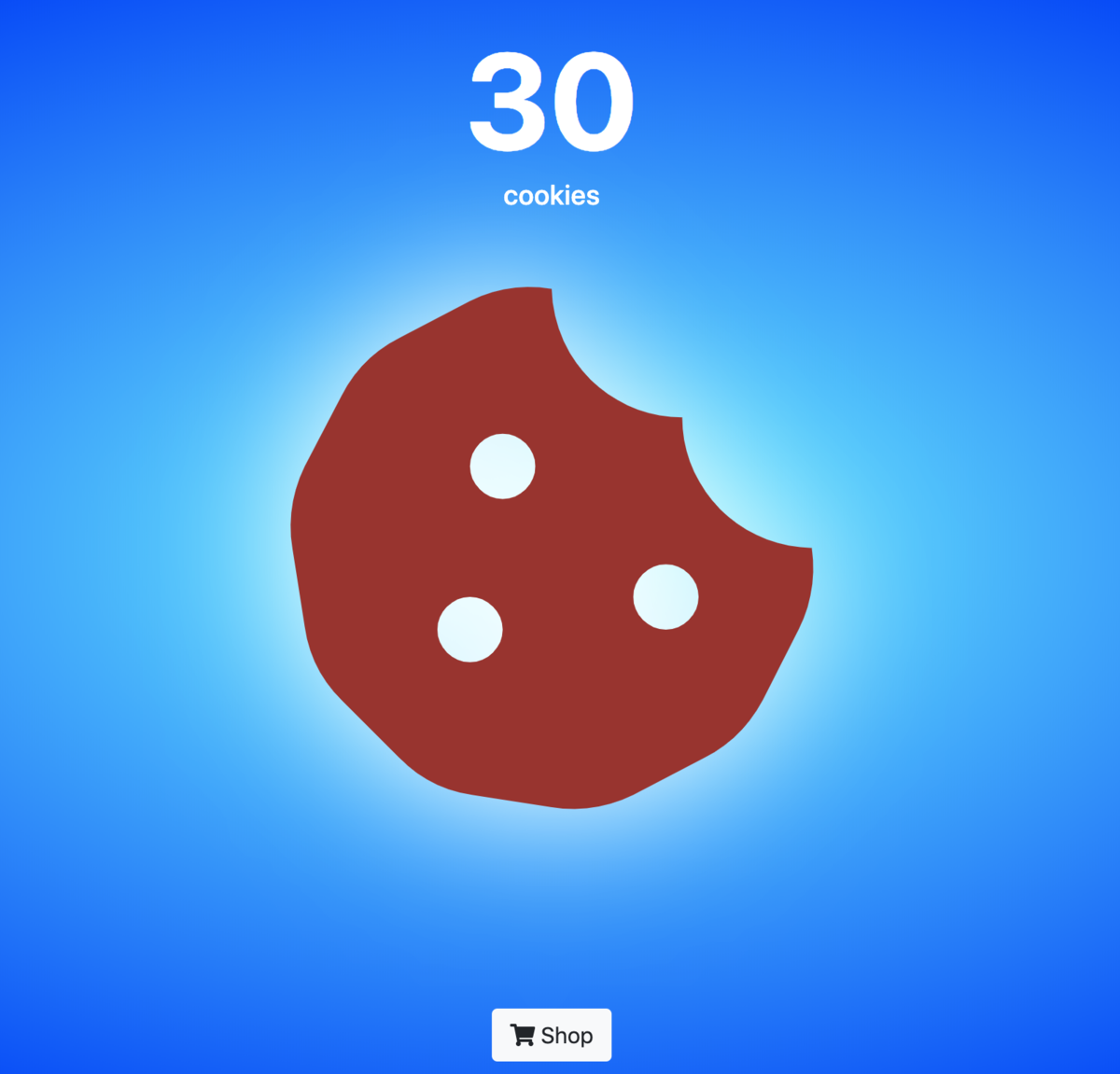
アプローチ:クッキーの書き換え
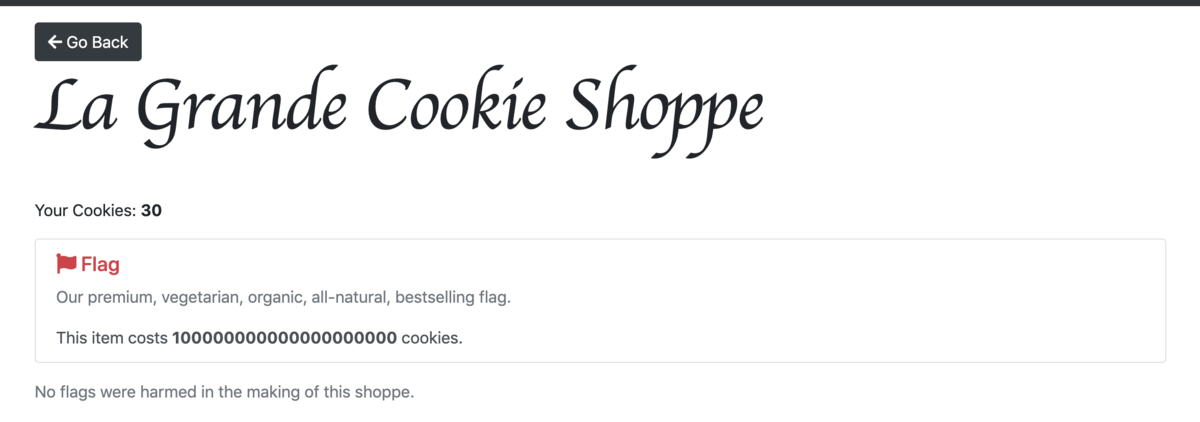
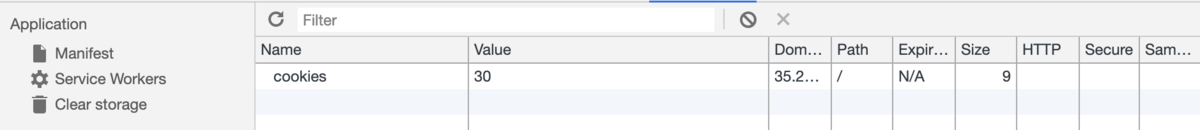
どうやらクッキーがいっぱい必要らしいのでクッキーを書き換えてflagをgetします.
> curl -b cookies=100000000000000000000000000000000000000000000000 http://35.225.2.44:5001/flag
bcaCTF{c00k13s_c71ck3d_34a2344d}%
まとめ
- Crypto問のCrypto感がなくて悲しかった
- 全体的にエスパー系だった